Vulnerability Management
With single sign-on users only have to enter one set of credentials to access their web apps in the cloud and behind the firewall – via desktops, smartphones and tablets. This foundational identity and access management (IAM) measure is a first step in building trusted experiences for your workforce, customers, and partners.
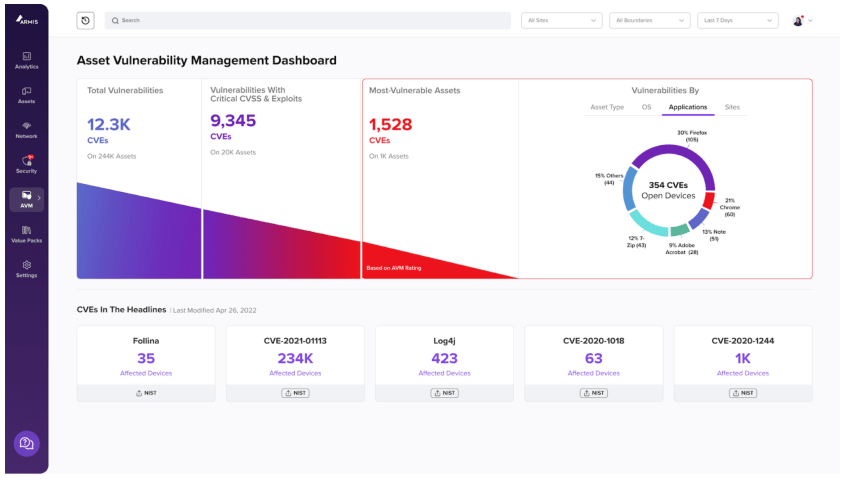
What is Vulnerability Management
What tool does Kappa Data Offer?
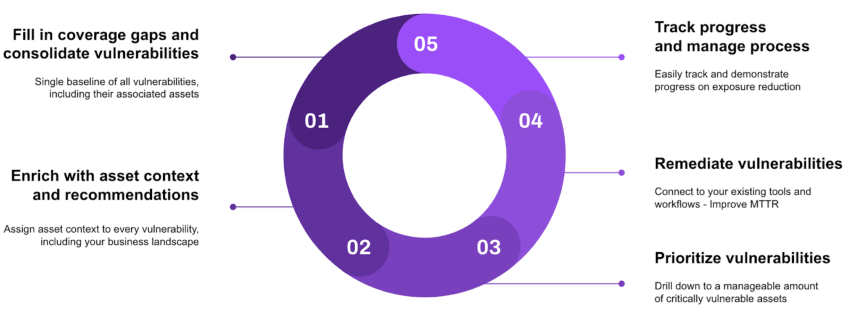
Implementing a Vulnerability Management Strategy
Inventory All Assets
The first step in any vulnerability management strategy is to create a comprehensive inventory of all your IT assets. This includes hardware, software, and network devices. Understanding what you have in your environment is crucial for effective vulnerability management.
Steps to Create an Asset Inventory:
- Automated Discovery Tools: Use automated tools to scan your network and identify all connected devices and software.
- Manual Audits: Complement automated discovery with manual audits to ensure no assets are missed.
- Classification and Categorization: Classify assets based on their criticality, type, and location. This helps in prioritizing vulnerability management efforts.
- Regular Updates: Continuously update the inventory to reflect changes in the IT environment, such as new devices or software installations.
Assess vulnerabilities
Once you have a comprehensive inventory, the next step is to assess the vulnerabilities associated with each asset. This involves identifying known vulnerabilities and evaluating their potential impact on your organization.
Steps to Assess Vulnerabilities:
- Vulnerability Scanning: Use vulnerability scanning tools like Armis ViPR to identify known vulnerabilities in your assets. These tools compare the software and firmware versions against a database of known CVEs.
- Patch Management Systems: Integrate with patch management systems to get real-time updates on available patches for identified vulnerabilities.
- Risk Assessment: Evaluate the potential impact of each vulnerability. Consider factors such as the exploitability, the criticality of the asset, and the potential damage in case of a breach.
Prioritize vulnerabilities
Not all vulnerabilities pose the same level of risk. Prioritizing vulnerabilities based on their severity and potential impact is crucial for effective remediation.
Criteria for Prioritization:
- Exploitability: How easily can the vulnerability be exploited? Vulnerabilities that are actively being exploited should be prioritized.
- Asset Criticality: The importance of the affected asset. For example, vulnerabilities in critical servers or databases should be addressed first.
- Business Impact: The potential business impact if the vulnerability were to be exploited. This includes financial loss, data breach implications, and reputational damage.
- Regulatory Compliance: Vulnerabilities that affect compliance with regulations such as GDPR, HIPAA, or PCI-DSS should be given high priority.
Apply updates and patches
Once vulnerabilities are prioritized, the next step is to apply the necessary updates and patches. This step requires careful planning to ensure that updates do not disrupt business operations.
Steps to Apply Updates:
- Patch Testing: Before applying patches, test them in a controlled environment to ensure they do not cause issues with existing systems.
- Scheduled Maintenance: Schedule patch deployment during maintenance windows to minimize the impact on business operations.
- Automated Deployment: Use automated patch management tools to deploy patches efficiently and consistently across all affected systems.
- Rollback Plans: Have rollback plans in place in case a patch causes unexpected issues. This ensures you can quickly revert to the previous state without significant downtime.
Monitor and report
Continuous monitoring and reporting are essential to ensure the ongoing effectiveness of your vulnerability management strategy. This involves tracking the status of vulnerabilities, assessing the success of remediation efforts, and keeping stakeholders informed.
Steps for Effective Monitoring and Reporting:
- Continuous Scanning: Regularly scan your network for new vulnerabilities and reassess existing ones. Automation tools can help in maintaining up-to-date vulnerability status.
- Incident Tracking: Maintain a log of all identified vulnerabilities, their status, and the actions taken to remediate them. This helps in tracking progress and ensuring accountability.
- Performance Metrics: Establish key performance indicators (KPIs) to measure the effectiveness of your vulnerability management strategy. Examples include the number of vulnerabilities detected, mean time to patch, and the number of incidents prevented.
- Stakeholder Reporting: Provide regular reports to stakeholders, including IT management, security teams, and executive leadership. These reports should highlight the current security posture, progress in vulnerability remediation, and any significant risks.
Continuous Improvement
Vulnerability management is not a one-time effort but an ongoing process. Continuously improving your strategy ensures that you stay ahead of emerging threats and maintain a robust security posture.
Steps for Continuous Improvement:
- Regular Reviews: Periodically review and update your vulnerability management policies and procedures to reflect changes in your IT environment and the threat landscape.
- Training and Awareness: Ensure that your IT and security teams are well-trained on the latest tools, techniques, and best practices in vulnerability management.
- Vendor Collaboration: Work closely with your software and hardware vendors to stay informed about new vulnerabilities and patches.
- Feedback Mechanisms: Implement feedback mechanisms to gather insights from your IT and security teams on the effectiveness of your vulnerability management strategy and areas for improvement.
Leveraging Automation with Armis ViPR
To streamline and enhance your vulnerability management efforts, leveraging automation tools like Armis ViPR can be highly effective. Armis ViPR provides comprehensive capabilities to discover, assess, prioritize, and remediate vulnerabilities, significantly reducing the manual effort required.
Benefits of Using Armis ViPR:
- Comprehensive Discovery: Automatically identifies all assets in your network, providing a complete inventory.
- Real-Time Assessment: Continuously scans for vulnerabilities and provides real-time updates.
- AI-Driven Prioritization: Uses AI to prioritize vulnerabilities based on risk factors and business impact.
- Automated Remediation: Facilitates the automated deployment of patches, ensuring timely and accurate updates.
- Intuitive Interface: Features a user-friendly interface that simplifies the vulnerability management process, even for non-technical users.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usWhy should an organization consider using Armis ViPR?
An organization should consider using Armis ViPR to enhance its ability to manage and secure a diverse range of connected devices, including IoT and OT. By providing continuous visibility, real-time vulnerability assessment, and automated patch management, Armis ViPR helps organizations reduce their attack surface, improve compliance, and protect critical assets from cyber threats.
Why is vulnerability management important for organizations?
Vulnerability management is crucial for organizations because it helps identify and mitigate security weaknesses that could be exploited by attackers. Effective vulnerability management reduces the risk of data breaches, ensures compliance with regulatory standards, and protects the organization’s reputation and assets.
Which types of organizations would benefit the most from using Armis ViPR?
Organizations with a large number of connected devices, such as those in healthcare, manufacturing, energy, transportation, and finance, would benefit the most from using Armis ViPR. These sectors often have numerous IoT and OT devices that are critical to operations and can be challenging to manage and secure.
What is Armis ViPR?
Armis ViPR (Vulnerability and Patch Management) is a comprehensive security solution designed to identify, assess, and remediate vulnerabilities across all connected devices, including IoT, OT, and unmanaged devices. It provides continuous visibility and automated patch management to enhance the overall security posture of an organization.
What benefits can an organization expect from using Armis ViPR?
Benefits of using Armis ViPR include:
- Improved security posture: By identifying and mitigating vulnerabilities, organizations can significantly reduce their risk of cyber attacks.
- Operational efficiency: Automated patch management reduces the manual effort required to keep devices secure.
- Regulatory compliance: Helps organizations meet compliance requirements by ensuring that vulnerabilities are promptly addressed.
- Comprehensive visibility: Provides a complete view of all connected devices and their security status.
What are the key features of Armis ViPR?
Key features of Armis ViPR include:
- Continuous device discovery: Identifies and monitors all connected devices.
- Vulnerability assessment: Detects and evaluates vulnerabilities in real-time.
- Automated patch management: Streamlines the process of deploying patches to vulnerable devices.
- Integration with existing security tools: Enhances existing security infrastructure with additional capabilities.
- Detailed reporting: Provides actionable insights and compliance reports.
How does Armis ViPR work?
Armis ViPR works by continuously scanning the network to identify all connected devices and assess their security status. It uses advanced analytics to detect vulnerabilities and provides actionable insights for remediation. ViPR integrates with existing security tools to automate patch deployment and ensure devices are kept up-to-date with the latest security patches.
How does Armis ViPR integrate with existing security tools?
Armis ViPR integrates with existing security tools through APIs and connectors, allowing it to work seamlessly with SIEM systems, endpoint protection platforms, and network security tools. This integration enables organizations to leverage their current security investments while enhancing their vulnerability management capabilities.
How does Armis ViPR handle the patch management process?
Armis ViPR handles the patch management process by continuously monitoring for available patches and automatically deploying them to vulnerable devices. It prioritizes patches based on the severity of vulnerabilities and the criticality of devices, ensuring that the most important updates are applied first.
How does Armis ViPR enhance the security of IoT and OT devices?
Armis ViPR enhances the security of IoT and OT devices by providing continuous visibility into device vulnerabilities and automating the patch management process. It ensures that these devices are regularly updated with the latest security patches, reducing the risk of exploitation and ensuring they remain secure over time.
Contact us for a demo
Are you curious to learn whether Armis can help you with searching of assets in the network and how to protect these assets? Contact us for a demo via the below button.
