Extended Detection and Response (XDR)
Extended Detection and Response or XDR is becoming more important for threat hunting reporting and searching for the root cause whenever a breach is discovered.
This article will help you to understand XDR and to discover why the use of this tool can be a necessasity for your organization.

What is Extended Detection and Response?
Extended Detection and Response platforms enables you to detect, investigate, and respond to multi-stage threats across all key vectors, in the shortest time.
- Get complete visibility beyond the endpoint : Detect & stop adversaries as they move
- Maximize user efficiency : Optimized workflows accelerate investigation and response
- Compatible with your existing cybersecurity tools and technology investments
During this article we will address Sophos XDR since, this tool is the most extended version of XDR Kappa Data Provide

Extended Detection and Response platform
Accelerate detection, investigation and response
Sophos XDR includes tools and capabilities designed to maximize the efficiency of security analysts and IT admins. AI-guided investigations enable you to quickly understand the scope and cause of an incident and minimize the time to respond
AI-priotized detections over all surfaces
Investigate and hunt threats at speed
Powerful search tools, including pre-canned query templates, enable you to find the data you need faster without needing to be an SQL expert
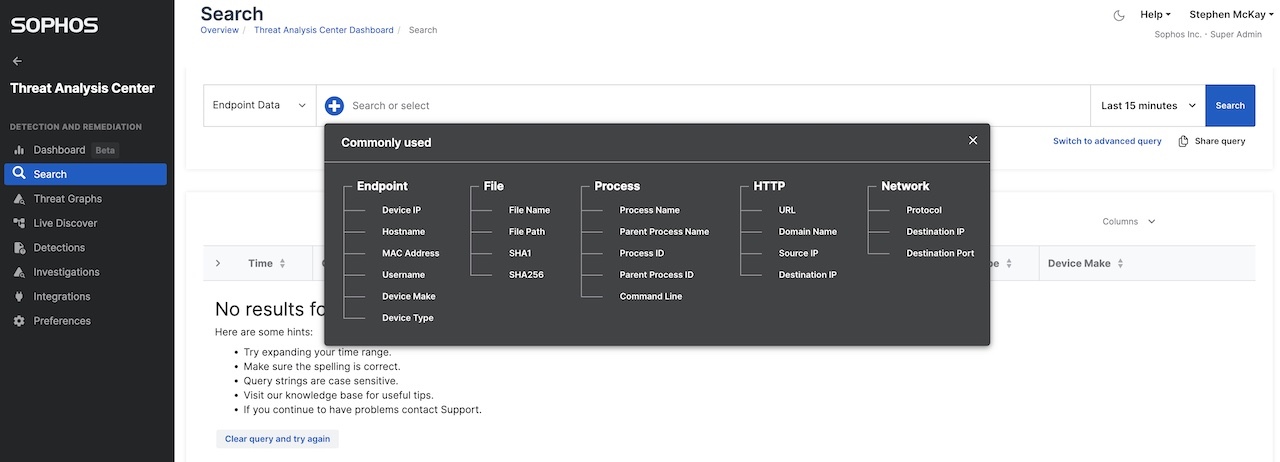
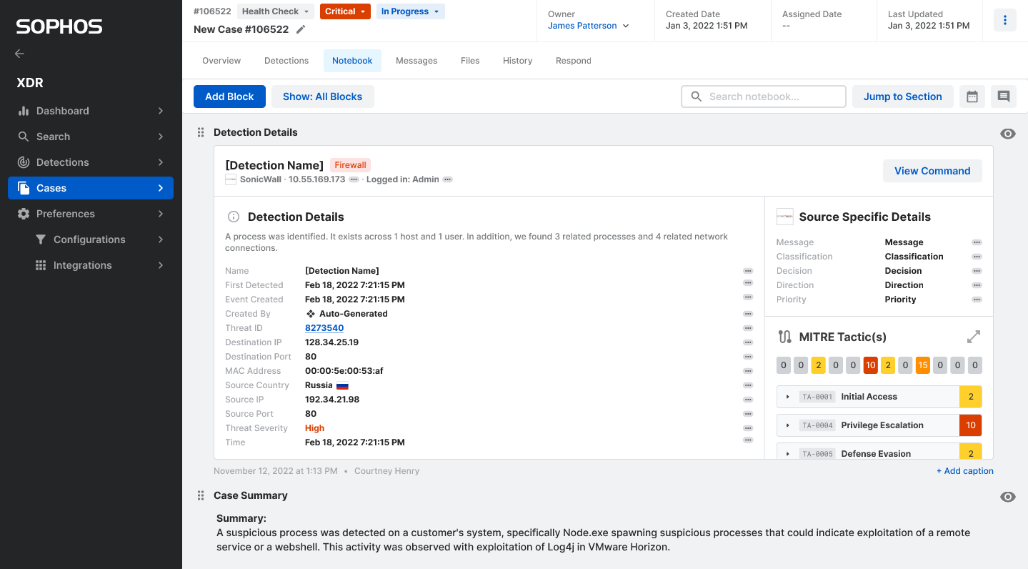
Collaborative case management
Automatic case creation enables rapid investigation, with comprehensive case management tools for collaboration with other team members.
MITRE ATT&CK Framework mapping
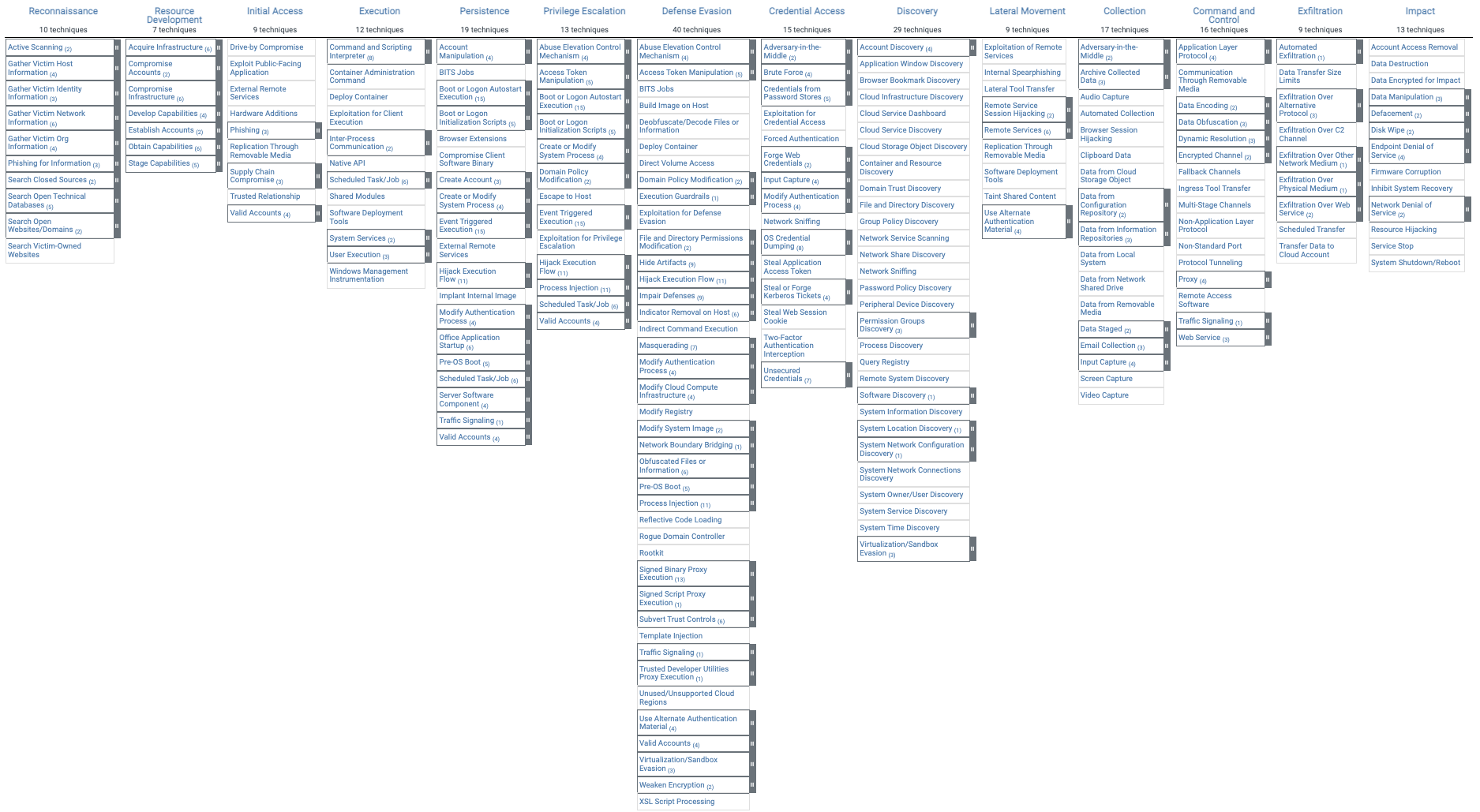
The MITRE ATT&CK framework is a universally accessible, continuously updated knowledge base for modeling, detecting, preventing and fighting cybersecurity threats based on cybercriminals’ known behaviors.
All known techniques of hackers are registered in this framework. All of these techniques are also registered in the Sophos XDR tools, on top of the techniques that are out of the scope of this framework but discovered by their own threat hunting team.
Sophos XDR Surfaces
Extended Detection and Response, or XDR, is the successor of EDR or Endpoint Detection and Response. This extension of surfaces has become necessary because hackers constantly look on the Internet for flaws in different types of devices and networks in order to “log-in” into the network.
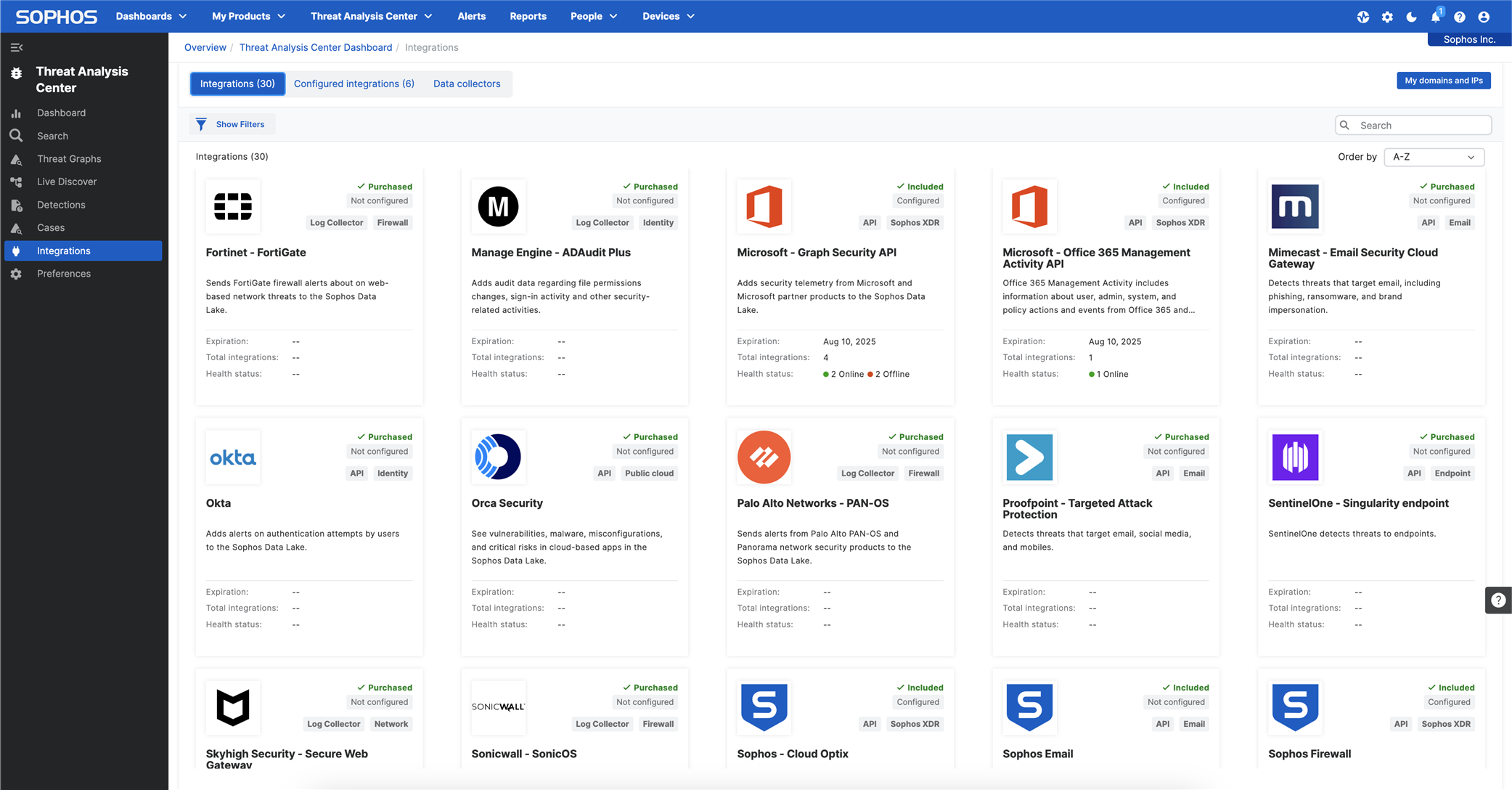
Sophos XDR Included Integrations
Sophos offers its own solutions like Endpoint Security, Network Security, Cloud Security and Email Every device is connected towards 1 central management platform, which is called Sophos Central.
In this overview, you will see as well the Microsoft Security Suite as the Google Security Suite included, what makes Sophos XDR quite interesting for organizations.
Sophos has its own ecosystem of different devices, as the graphic shows below.
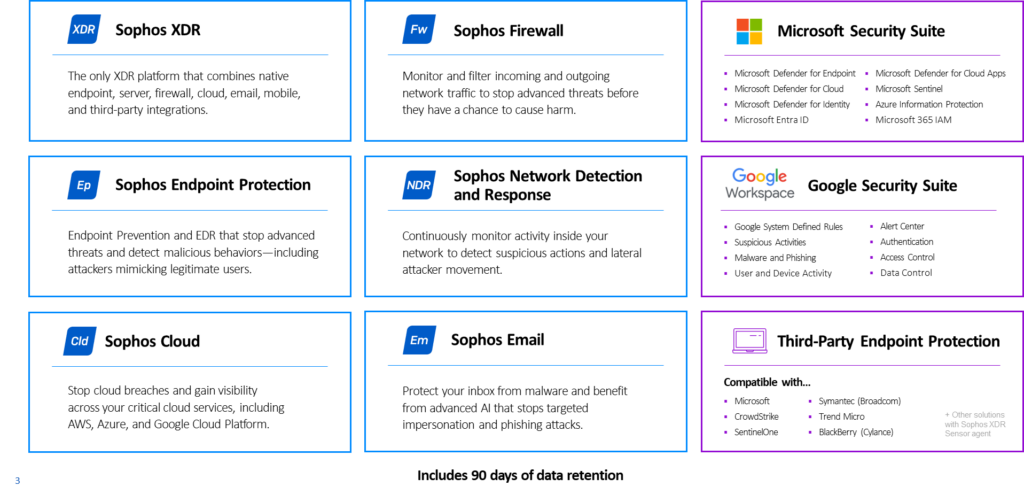
Sophos XDR External integrations
In many cases, companies have a network that exists out of different brands for firewalls, switches, Access Points, cloud directories, identity platforms, etc..
In order to implement XDR threat hunting, metadata of these different devices needs to be integrated into the data lake of Sophos. For integrating the metadata of these devices, Sophos uses Application Program Interfaces (API’s) for retrieving this data and order this data in their alerting system.

Using Sophos XDR
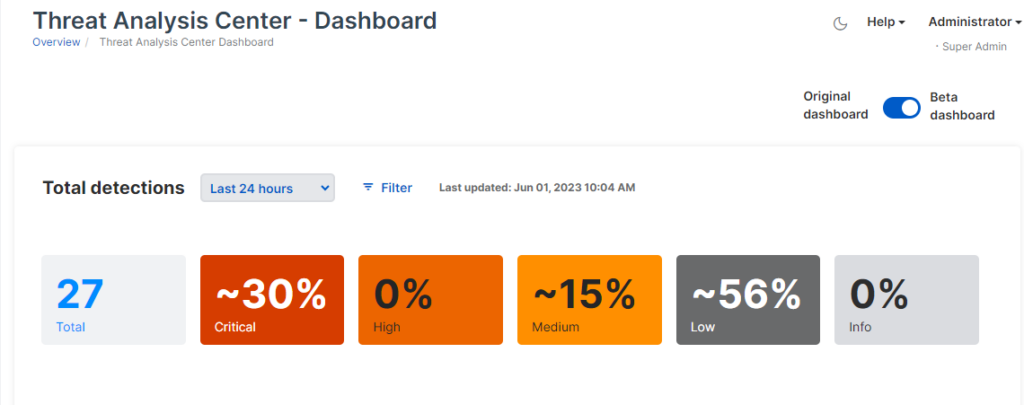
Sophos XDR lets you investigate detected threats (threat graph – see below) and search for new threats or security weaknesses. It also lets you monitor devices and fix issues remotely.
Within the Threat Analysis Center, you can find the most XDR features
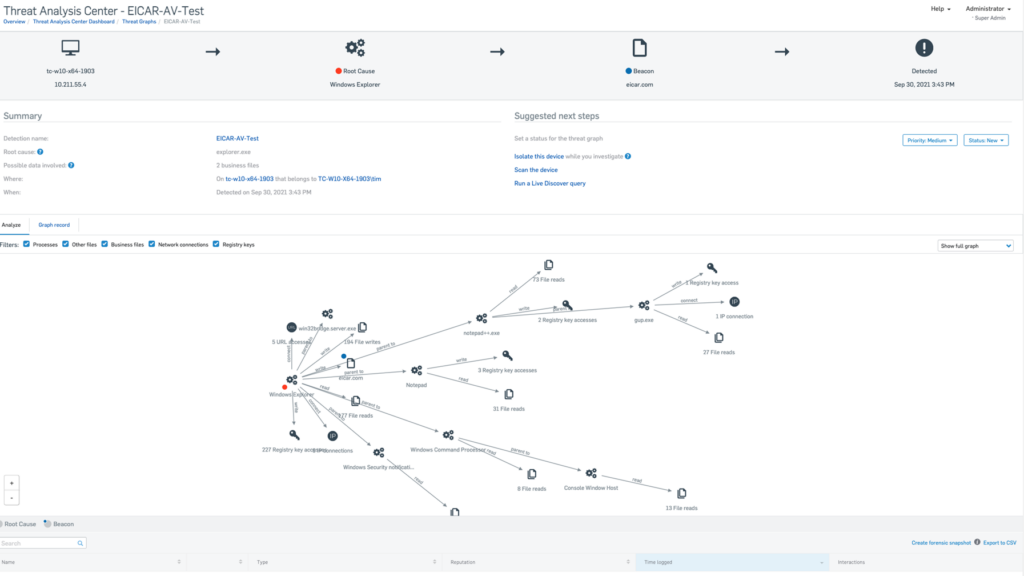
When you drill down you can track the root cause of a certain threat in order to stop the detection and eliminate the possibility a hacker can proceed with its activities
Is the use of Sophos XDR for everyone?
Using Sophos XDR (Extended Detection and Response) tools effectively requires a combination of technical knowledge, understanding of cybersecurity principles, and familiarity with the specific features and functionalities of Sophos XDR. Here are the basic requirements and knowledge areas you need:
Technical Requirements
-
System Requirements:
- Ensure that the systems where Sophos XDR will be deployed meet the necessary hardware and software requirements. This includes supported operating systems and sufficient resources (CPU, memory, disk space).
-
Network Requirements:
- Adequate network infrastructure to support the deployment of Sophos XDR tools.
- Configuration of network devices to allow communication between Sophos agents and the management console.
-
Sophos Central Account:
- Access to Sophos Central, the cloud-based management platform where Sophos XDR is managed and monitored.
Knowledge Requirements
-
Understanding of Cybersecurity Basics:
- Fundamental knowledge of cybersecurity principles and best practices.
- Familiarity with common threats, attack vectors, and mitigation strategies.
-
Endpoint Security:
- Knowledge of endpoint security concepts and tools, including antivirus, anti-malware, and endpoint detection and response (EDR) solutions.
-
Network Security:
- Understanding of network security principles, including firewall management, intrusion detection/prevention systems (IDS/IPS), and network traffic analysis.
-
Incident Response:
- Basic knowledge of incident response processes and procedures.
- Familiarity with the steps involved in detecting, analyzing, and responding to security incidents.
-
Threat Intelligence:
- Awareness of threat intelligence sources and how to use them to inform security decisions.
- Understanding of how threat intelligence integrates with XDR tools.
Practical Skills
-
Installation and Deployment:
- Ability to install and configure Sophos XDR agents on various endpoints.
- Experience with deploying security tools across different environments (on-premises, cloud, hybrid).
-
Configuration and Management:
- Skills in configuring policies, rules, and settings within Sophos XDR to tailor it to specific organizational needs.
- Familiarity with managing and maintaining Sophos Central.
-
Monitoring and Analysis:
- Proficiency in using the Sophos XDR dashboard to monitor security events and alerts.
- Ability to analyze security data, identify patterns, and interpret alerts to determine the severity and impact of incidents.
-
Reporting and Documentation:
- Capability to generate and interpret reports from Sophos XDR.
- Skills in documenting security incidents, actions taken, and lessons learned.
-
Integration and Automation:
- Knowledge of integrating Sophos XDR with other security tools and platforms for a cohesive security ecosystem.
- Familiarity with automation and scripting to streamline security operations and incident response.
Training and Certification
-
Sophos Training:
- Completing Sophos training courses and certifications related to XDR, such as the Sophos Certified Administrator or Sophos Certified Engineer programs.
-
Continuous Learning:
- Staying updated with the latest cybersecurity trends, threats, and best practices.
- Participating in ongoing education and training to keep skills and knowledge current.
If you don’t have the necessary skill or the resources to do threat hunting or do monitoring 24×7, Sophos offers as well Managed Detection and Response as a service that is discussed on this page.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow does Sophos XDR enhance threat detection and response capabilities?
Sophos XDR enhances threat detection and response by correlating data from various sources, providing a comprehensive view of the security landscape. It uses advanced analytics, machine learning, and automation to detect threats, prioritize alerts, and respond to incidents quickly. This holistic approach helps identify complex threats that might be missed by siloed solutions.
How does Sophos XDR fit into the current cybersecurity landscape?
In the current cybersecurity landscape, organizations face increasingly sophisticated and targeted attacks. Sophos XDR addresses these challenges by providing a comprehensive, integrated approach to threat detection and response. It helps organizations stay ahead of advanced threats by offering deep visibility, automated threat hunting, and coordinated responses across multiple security layers.
How does Sophos XDR support compliance and regulatory requirements?
Sophos XDR supports compliance and regulatory requirements by providing detailed logs, reports, and audit trails of security activities. It helps organizations meet standards such as NIS2, GDPR, HIPAA, and PCI DSS by ensuring robust protection, continuous monitoring, and quick response to incidents. The centralized management and comprehensive visibility also aid in demonstrating compliance during audits.
What are the basic requirements for implementing Sophos XDR?
The basic requirements for implementing Sophos XDR include:
- Deployment of Sophos endpoint and server protection: Ensure that Sophos security agents are installed on all relevant devices.
- Sophos Central account: Use the Sophos Central management console for centralized management and integration of XDR capabilities.
- Network infrastructure compatibility: Ensure the existing network infrastructure can integrate with Sophos XDR, including firewalls and other security tools.
- Adequate storage and processing power: Allocate sufficient resources for data collection, storage, and analysis.
What are the key components of Sophos XDR?
Key components of Sophos XDR include:
- Sophos Central: A unified management console for deploying and managing XDR capabilities.
- Endpoint and server protection: Advanced security agents that provide real-time threat detection and response.
- Firewall integration: Data from Sophos firewalls to enhance network-level threat visibility.
- Email security: Integration with Sophos email protection to cover another critical attack vector.
- Cloud security: Protection for cloud workloads and environments to ensure comprehensive coverage.
What features does Sophos XDR offer for threat investigation?
Features of Sophos XDR for threat investigation include:
- Unified data lake: Aggregates data from endpoints, servers, firewalls, and other sources for comprehensive analysis.
- Cross-product correlation: Links related security events across different products to identify sophisticated attacks.
- Automated threat hunting: Uses AI and machine learning to proactively search for threats.
- Detailed forensics: Provides in-depth analysis of security incidents, including root cause analysis and impact assessment.
- Custom queries: Allows security teams to create custom queries to investigate specific threats or anomalies.
What is Sophos XDR?
Sophos Extended Detection and Response (XDR) is an advanced cybersecurity solution that integrates endpoint, server, firewall, email, and other data sources to provide comprehensive threat detection, investigation, and response capabilities. It extends beyond traditional endpoint detection and response (EDR) to offer a more holistic view of an organization’s security posture.
What role does AI and machine learning play in Sophos XDR?
AI and machine learning play a critical role in Sophos XDR by enhancing its ability to detect and respond to threats. These technologies analyze large volumes of data to identify patterns, anomalies, and emerging threats in real-time. They enable automated threat hunting, prioritize alerts based on risk, and suggest optimal response actions, thereby improving the efficiency and effectiveness of security operations.
Which types of organizations would benefit the most from using Sophos XDR?
Organizations that handle sensitive data, have complex IT environments, or face sophisticated cyber threats would benefit the most from using Sophos XDR. This includes sectors such as finance, healthcare, education, government, and large enterprises with significant security needs.
Why is the integration of Sophos Email Security with XDR and MDR important for compliance with the NIS2 directives?
The integration of Sophos Email Security with XDR and MDR is important for compliance with the NIS2 directives because it ensures a robust, multi-layered defense against cyber threats. The NIS2 directives require organizations to implement comprehensive security measures, including proactive monitoring, threat detection, and incident response. By integrating email security with XDR and MDR, organizations can meet these requirements more effectively, ensuring the resilience of critical infrastructure and services.
Contact us for a demo
Are you curious to learn how Extended Detection and Response (XDR) can enhance your security in your global network? Contact us for a demo via the below button.
