Incident response needed for NIS2
For Essential and Important businesses, the way how cybersecurity events and incident response is needed is well described in the Cyberfundamentals Framework at CCB Belgium. Both type of entities needs to execute an Incident Reponse Plan in order to ensure the business is protected against significant disruptions.
View Webinar recording Response
Incident Response
Incident Resonse Plan
Essential and key entities must take appropriate and proportionate technical, operational and organizational measures to manage the risks to the security of the network and information systems they use for their operations or to provide their services, and to prevent incidents or mitigate the effects of incidents on the recipients of their services and on other services. An incident response plan must therefore contain a set of instructions to help IT staff to detect, respond and recover from network security incidents.
Obligated Incident reporting
NIS2 directives instruct every Essential and important entity to report significant incidents within 24 hours towards CSIRT (Computer Security Incident Reponse Team), which lead by Cybersecurity Center Belgium (CCB). Further reporting is as well required towards CSIRT, but as well towards partners within the supply chain. More information can be found below.
Security Operations Center
Cyber incident detection and response are often treated by Security Operations Center (SOC) teams by the entity or a indicated partner. The importance of using a SOC is only increasing day by day, since hackers are operational when a company is closed. Building a SOC is quite a challenge for many companies, but Kappa Data offers Managed XDR and Managed Detection & Response (MDR) via Services of our suppliers. More information can be found on our page Security Operation Center.
Incident Response within NIS2
Incident response within the NIS2 requirements are as well an important part of the global approach of this legislation. The core functions of the Cyberfundamentals framework Detect, Respond and Recover are required for Important as for Essential entities. Within incident response, several requirements are listed in the Cyberfundamentals Covers. Below you can find the requirements for an Essential Entity :
- Response plan is executed during or after an incident
- Personnel know their roles and order of operations when a reponse is needed
- Incidents are reported consistent with established criteria
- Information is shared consistent with reponse plan
- Coordination with stakeholders occurs consistent with reponse plan
- Voluntary information sharing occurs with external stakeholders to achieve broader cybersecurity situational awareness
- Notifications from detection systems are investigated
- The impact of the incident is understood
- Forensics are performed
- Incidents are categorized consistent with response plan
- Processes are established to receive, analyze and respond to vulnerabilities disclosed to the organization from internal and external resources.
- Incidents are contained
- Incidents are mitigated
- Newly identified vulnerabilities are mitigated or documented as accepted risks.
- Response plans incorporate lessons learned
- Response & recovery stategies are updated.
Importance Incidence Response NIS2 Directives in Belgium
Every Important and Essential entity, active in the defined sectors, as mentioned in the Scope of Sectors on our NIS2 page is obligated to follow the NIS2 law from the 18th of October 2024. When organizations are not registered or responding towards the NIS2 directives, penalties can be implemented between 500 and 10 million euros, depending on the size and nature of the penalty.
Management bodies from Essential and important entities can even be held accountable when the obligated directives are not implemented. For Essential entities, inspections can be held by Certification bodies before an incident. For important entities, inspections can be held after an incident has occured. More information on these penalties can be found in the Management Obligations & Responsibilities section on our NIS2 page.
Obligated Incident Reporting when incident
For important and essential entities, incident reporting of significant incidents must be done within 24 hours after the determination of an incident towards CSIRT.
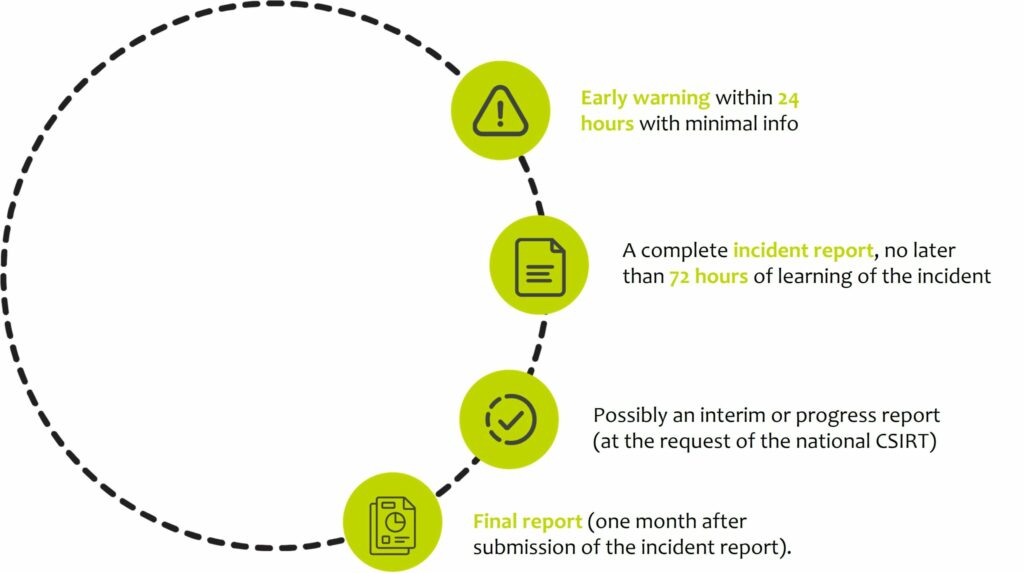
When an incident is significant enough, the following procdure must be followed :
- without delay and at the latest within 24 hours of becoming aware of the significant incident, the entity issues an early warning
- without delay and at the latest within 72 hours (24 hours for trust service providers) of becoming aware of the significant incident, the entity communicates an incident report
- at the request of the national CSIRT or, where applicable, the relevant sectoral government, the entity provides an interim report
- No later than one month after the incident report referred to in point 2, the entity shall provide a final report
- If the final report cannot be submitted because the incident is still ongoing, the entity provides a progress report and, within one month after it has finally dealt with the incident, the final report.
Landscape of Cybersecurity in Belgium
An interesting document to read is the Cybersecurity Monitor 2023 for the status of Cybersecurity Management in Belgium. Through CIONET the leaders of 250 companies participated at a voluntary survey. This survey resulted into a deep insight into topics that occupy the minds of executive leaders of cybersecurity.
Despite increased budget allocations, organizations continue to face a persistent shortage of cybersecurity staff. On average, only 7% of IT full-time equivalents (FTEs) are focused on cybersecurity, underscoring a systemic understaffing problem.
To tackle this talent shortage, organizations are implementing a twofold strategy. First, they are outsourcing certain cybersecurity functions, like Security Operations Centers (SOCs), to Managed Security Service Providers (MSSPs) to ease the burden. Second, they are decentralizing cybersecurity responsibilities by making product teams accountable.
This decentralized model is bolstered by security champions within product teams, who serve as proxies for the cybersecurity team and help bridge skill gaps.
Challenges and initiatives in cybersecurity
Cybersecurity challenges and initiatives
Several top challenges need to be addressed like staffing issues, complexity in cybersecurity landscapes, supply chain challenges and lapses in basic IT asset hygiene.
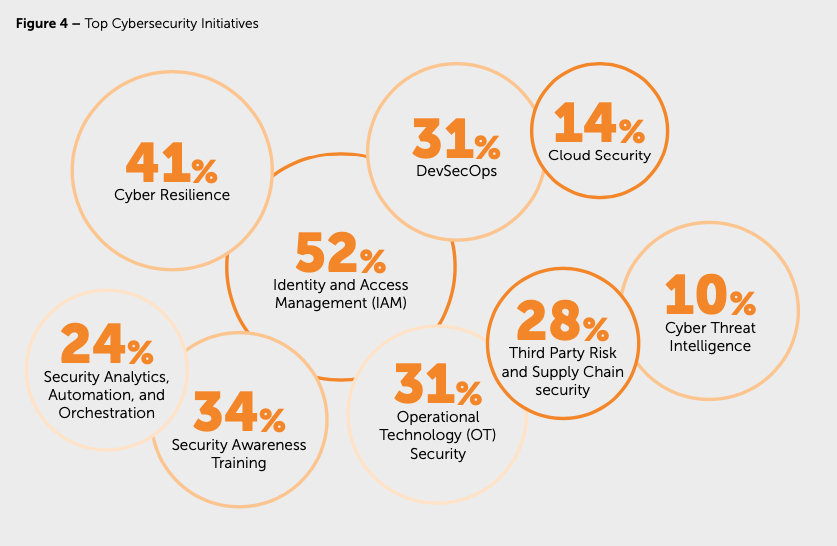
Organizations are prioritizing key cybersecurity initiatives. Identity Access Management (IAM) and cybersecurity resilience tops of the lists in this survey. Weekly we see at Kappa Data demands of IT partners regarding XDR tools and Managed Detection and Response services in order to increase the cybersecurity resilience at their customer sites.
With the rise in cyber attacks, resilience testing has become more critical. Prevention strategies, such as security awareness training and DevSecOps, also feature prominently. Automation and efforts to circumvent the talent shortage are pivotal in driving these initiatives forward.
 Source Inno.com/news/overall-state-cybersecurity-belgiumDownload this report
Source Inno.com/news/overall-state-cybersecurity-belgiumDownload this report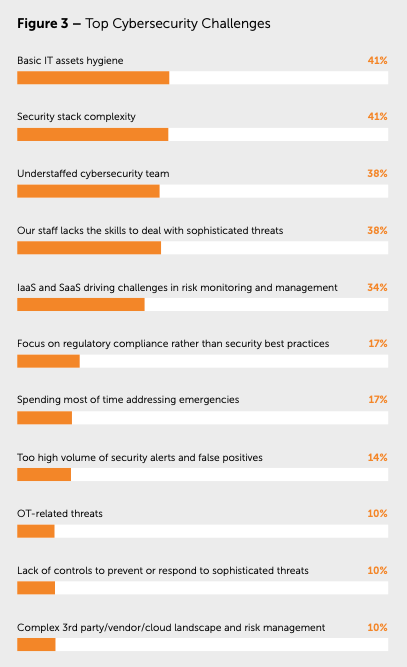
Recent Cybersecurity incidents and their impact
Cybersecurity incidents more often than we see in the media. Companies can withhold information, fearing reputation loss against its own suppliers or customers. In case of Ransom attacks, the impact can be life-changing.
When your organization has been attacked by a ransomware, hackers are asking in some cases high amounts of money. Besides the money, companies are affected on a business level. Daily sales and communication with its customer base has also been damaged. In some cases it is hard to calculate the impact on the losses in case of attack, but overall a cyberattack can be life-threatening for an organization. For a CEO that worked his whole life for his company, is a cyberattack a threat in many ways.
Some of the bigger cyberattacks do reach the news and are often communicated over the different channels. As an organization, it is never good for your own reputation to reach the news with such an event. During the past months, several brands and organizations were victim of such an attack.
“One of our suppliers invited last year somebody, on one of his events, which was a CEO of a photo and visual company that has been a victim of a ransomware attack. This person saw his company going bankrupt, where he lost his company and house, even his marriage. “
Patrick Banken Kappa Data
Building an Effective Incident Response Plan
Building an effective incident response plan can be challenging for companies who are less experienced with these type of policies. Therefore we share this plan, communicated by the Cybersecurity Center Belgium (CCB) with the document that you can view with the button below.
Incident Reporting and Management
Incident reporting is an obligated item, since the obligation within the NIS2 law that will be communicated from the 18th of October. When incidents are not reported, fines can be charged. More information can be found here.
Procedures for incident reporting
Incident reponse of significant incidents, requires as well procedures on the reporting side. In the paragraph above, Obligated Incident Response when incident, the procedure is communicated how to communicate towards CSIRT.
When an significant incident is detected, incidents needs to be reported consistently with established criteria. One of these criteria is clear communications towards the internal stakeholders. Not only internally, external stakeholders like industry security groups
Role of national authorities in incident management
In Belgium, the national authority responsible for cyber incident response is the Centre for Cybersecurity Belgium (CCB). The CCB plays a crucial role in coordinating and managing the country’s response to cyber incidents. Here are the key roles and responsibilities of the CCB:
National Coordination
The CCB coordinates with various national stakeholders, including government agencies, critical infrastructure operators, and private sector organizations, to ensure a unified and effective response to cyber incidents.
Incident Response:
Threat Intelligence:
Policy and Strategy Development:
Awareness and Training:
International Collaboration:
Regulatory Role:
Research and Development:
Future Trends in Incident Response and Cybersecurity
Emerging threats and trends
The landscape of cyber threats is continually evolving, influenced by technological advancements and shifts in the global environment. Understanding these emerging threats and trends is crucial for enhancing cybersecurity measures.
Ransomware-as-a-Service (RaaS) is one of the most concerning developments.
This model provides even non-technical criminals with the tools and infrastructure needed to launch ransomware attacks, leading to a significant increase in such incidents. Similarly, supply chain attacks have become more prevalent, with attackers targeting less-secure elements within a supply chain to infiltrate larger, more secure organizations. The SolarWinds attack is a notable example of this strategy.
Deepfake technology
Poses a growing threat as it allows for the creation of convincing fake videos and audio recordings. These can be used in social engineering attacks, disinformation campaigns, and even to manipulate stock prices or political outcomes. Additionally, the proliferation of Internet of Things (IoT) devices has introduced new vulnerabilities. Many IoT devices lack robust security measures, making them attractive targets for cybercriminals.
Zero-day exploits continue to be a significant threat.
These involve exploiting unknown vulnerabilities before they are patched, often allowing attackers to gain unauthorized access to systems. On the other hand, phishing attacks are becoming increasingly sophisticated. They are now more personalized and harder to detect, with advanced techniques such as spear-phishing and business email compromise (BEC) being commonly used.
Artificial intelligence (AI) and machine learning (ML) leveraged by cybercriminals.
These technologies enhance attack methods, making them more effective and difficult to detect. They are used to automate attacks and create more convincing social engineering tactics. As businesses increasingly migrate to the cloud, cloud security challenges have become prominent. Misconfigurations, inadequate access controls, and the complexities of shared responsibility models are common issues exploited by attackers.
The rise of crypto jacking
Another trend is crypto jacking, where attackers hijack computer resources to mine cryptocurrencies, driven by the profitability of cryptocurrencies and the relatively low risk of detection.
Additionally, attacks on critical infrastructure such as power grids, water supply systems, and transportation networks are becoming more frequent. These attacks can have severe consequences, including service disruptions and economic damage.
With the introduction of privacy and data protection regulations like GDPR and CCPA, organizations face new challenges in ensuring compliance. Non-compliance can result in significant fines, making data protection a top priority.
Social media
Social Media is also being exploited by cybercriminals to distribute malware, conduct phishing attacks, and gather intelligence on potential targets. The widespread use of social media makes it a valuable tool for attackers.
Quantum computing
Although still in its early stages, quantum computing poses a potential future threat to current encryption standards. Cybersecurity experts are beginning to explore quantum-resistant algorithms to mitigate this risk.
To combat these emerging threats, organizations are adopting various defensive strategies. Zero Trust Architecture is being implemented, requiring verification of all users and devices attempting to access resources, regardless of their location. Enhanced threat detection and response technologies, such as Extended Detection and Response (XDR) and Security Information and Event Management (SIEM), are being utilized to identify and mitigate threats in real-time.
Cyber threat intelligence sharing is becoming more common, with organizations collaborating with industry peers and cybersecurity groups to share threat intelligence and best practices.
User awareness and training
Regular user awareness and training programs are essential to help employees recognize and respond to phishing attempts and other social engineering tactics. Additionally, regular security audits and penetration testing are being performed to identify and address vulnerabilities before attackers can exploit them.
Staying informed about these emerging threats and trends is essential for organizations to proactively defend against cyberattacks and protect their assets.
Innovations in incident response
At Kappa Data we see more and more interest at customer sites for Managed Detection and Response because of the complexity of the network, lack of resources in specialized IT security personnel and variety of used of technology.
Even the use of End Detection and Response (EDR) as sole solution is no longer enough when breaches in the network can occur by a less protected device that is connected with the company network. When endpoints are combined with the use of a variety of solutions in the cloud, OT & IoT devices, backup systems, Identity platforms, legacy applications, etc…, company management can no longer expect from their IT department to have control over possible vulnerabilities of all connected devices.
Mark Van Tiggel - Telenet (Source : The Status of Cybersecurity Management in Belgium)
Predictions for the incident response landscape in Belgium
For the larger enterprises we see the use of Security Operation Centers (SOC) more and more present of their own or delivered by the larger System Integrators.
For the mid-size entities, more challenges are expected since they have less resources for building their own SOC or even finding qualified personnel to have 24×7 monitoring detection and incident response. Therefore, we expect that Managed Detection and Response services offered by suppliers will be become more and more important.
The use of performant XDR tools that can collect a wide range of data, give context around this data with the help of Artificial Intelligence and provide Security teams the wright priorities on vulnerabilities and a root cause analysis will help them to prevent and respond to incidents.
Since hackers are always searching for new ways to have access to the network, IT departments will have the challenge to have systems and procedures on board that are flexible and scalable with their own environment and can evolve with the new cyber attack trends.
Frequently asked questions
Here you can find a list off the most common questions and answers for Incident Response. If you don't see your question, do not hesitate to contact us.
What is Managed Detection and Response (MDR)?
Managed Detection and Response (MDR) is a cybersecurity service that provides continuous monitoring, threat detection, and incident response. It combines advanced technology with human expertise to identify and mitigate security threats quickly and effectively.
How does MDR differ from traditional managed security services?
Unlike traditional managed security services, which focus primarily on monitoring and alerting, MDR includes proactive threat hunting, detailed forensic analysis, and active incident response. MDR services are designed to detect and respond to threats in real-time, minimizing the impact of security incidents.
Why might an organization without a dedicated monitoring team need MDR?
Organizations without a dedicated monitoring team need MDR to ensure continuous security coverage. MDR provides expert monitoring and response capabilities, which are critical for detecting and mitigating threats that internal teams might miss due to limited resources or expertise.
Can MDR services be beneficial for organizations with an existing monitoring team?
Yes, MDR services can complement existing monitoring teams by providing additional expertise, advanced threat detection tools, and 24/7 coverage. This partnership can enhance the overall security posture and ensure quicker and more effective incident response.
What are the key components of an MDR service?
Key components of an MDR service include:
- Continuous monitoring: 24/7 surveillance of network and endpoints.
- Threat detection: Use of advanced analytics and threat intelligence to identify potential threats.
- Incident response: Rapid investigation and containment of identified threats.
- Threat hunting: Proactive search for hidden threats within the environment.
- Reporting and analysis: Detailed reports on security incidents and recommendations for improvements.
How does MDR handle incident response?
MDR handles incident response by quickly identifying and analyzing the threat, containing the affected systems, eradicating the threat, and recovering normal operations. The MDR team also provides a detailed post-incident analysis to prevent future occurrences.
What should an organization consider when choosing an MDR provider?
When choosing an MDR provider, organizations should consider the provider’s:
- Expertise and reputation: Experience in handling similar threats and incidents.
- Technology stack: Use of advanced tools and technologies for threat detection and response.
- Response time: Ability to quickly detect and respond to incidents.
- Customization: Capability to tailor services to the organization’s specific needs.
- Integration: Ease of integration with existing security infrastructure and processes.
How does MDR integrate with existing security tools and processes?
MDR integrates with existing security tools and processes by leveraging APIs and connectors to gather data from various sources, such as SIEM systems, firewalls, and endpoint protection tools. This integration ensures a seamless flow of information and enhances the effectiveness of the overall security strategy.
What are the benefits of having MDR for small and medium-sized businesses (SMBs)?
Benefits of MDR for SMBs include:
- Access to expertise: Gain access to top-tier cybersecurity experts without the need to hire in-house.
- Cost-effectiveness: Avoid the high costs of building and maintaining a dedicated security team.
- Enhanced security: Benefit from advanced threat detection and response capabilities.
- Scalability: Easily scale security services as the business grows.
How does MDR contribute to compliance and regulatory requirements?
MDR contributes to compliance and regulatory requirements by providing continuous monitoring, detailed logging, and comprehensive reporting. These services help organizations meet standards such as NIS2, GDPR, HIPAA, and PCI DSS by ensuring that security measures are in place to detect, respond to, and report on security incidents.
