DNS Protection
DNS Protection is an important measure for securing the use of webapplications, which is more and more common today. DNS Protection blocks access to malicious DNS servers as a user. Within the supply chain, cybercrime is often setup with the use of malicious DNS Servers. On this page you will learn, why DNS Protection is an important asset for your organization.
Ask for a demo
Protect the gray zone of unkown domains with Whalebone DNS Protection
DNS protection has become an essential security measure for protection users from malicious and unknown DNS domains or in short the “gray zone”.
These are the uncharted territories of the internet where potential threats lurk, unrecognized by conventional security systems until it’s too late. Enter Whalebone Immunity – a groundbreaking solution designed to fortify your defenses against these unseen perils.
Whalebone Immunity leverages advanced AI-driven threat intelligence and real-time domain analysis to provide robust protection against the myriad dangers that populate the gray zone. Unlike traditional antivirus and firewall solutions that rely heavily on known signatures and pre-defined threat databases, Whalebone Immunity operates on the cutting edge, identifying and neutralizing threats from unknown domains before they can cause harm.
90% of cyberattacks happens via DNS
You might think that firewalls can be enough for protecting users accessing malicious domains on the internet, but unfortunately they aren’t.
Traditional security tools are often reactive, depending on updates and patches to recognize and mitigate threats. They rely heavily on a database of known threats, which means new or evolving threats can slip through the cracks until they are identified and added to the database. This lag time can be exploited by cybercriminals to cause significant damage.
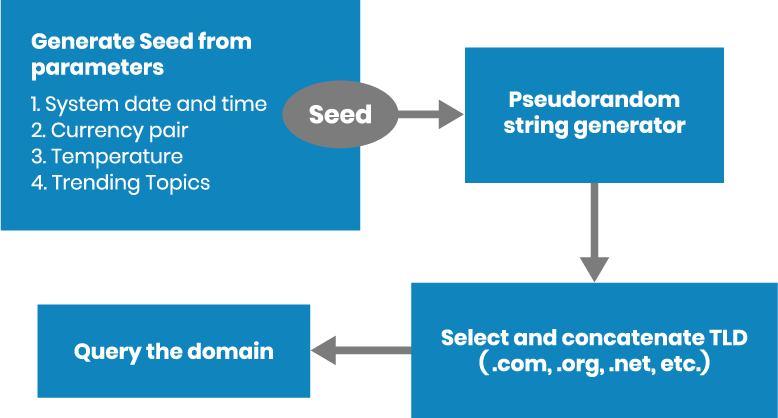
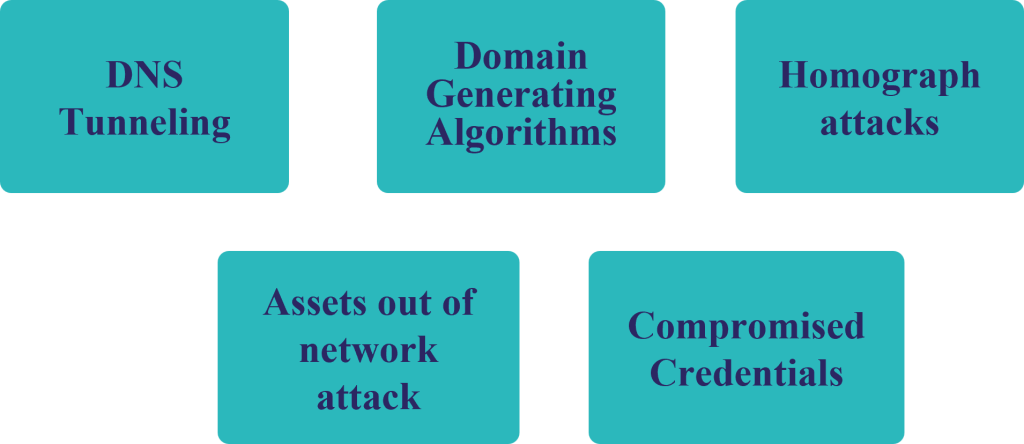
Cybercriminals often use Domain Generating Algorithms (DGA) that generate a large number of Domains in seconds, in order to frequently change the domains they use to launch malware attacks.
Domain Generating Algorithms (DGA)
The domains act as a meeting point for malware C&C servers. The generators have to deliver domains that are predictable for the two communicating entities. But for security researchers, these domains should be as unpredictable as possible.
The domain generation algorithms follow the three element structure:
- A base element called a seed. It can be a phrase or a number that hackers can change when they need it. The seed must be
known to both sides of communication: client and source. It is important because the threat actors need to know in advance which domain name the malware will use. - An element that changes with time. It will be combined with the seed in an algorithm. The word „time” does not refer to a date or hour, but rather to a certain event of the moment.
- Top Level Domains (TLDs). The ”body” constituted from the seed and the time element is combined with available TLDs.
Homograph spoofing

Domains can be registered in multiple alphabets and character sets. Homograph Spoofing is when a bad actor registers a domain which will look similar to a known domain by using a different alphabet or replacing a letter with a similar one.
Try copy and paste: www.gооgle.com
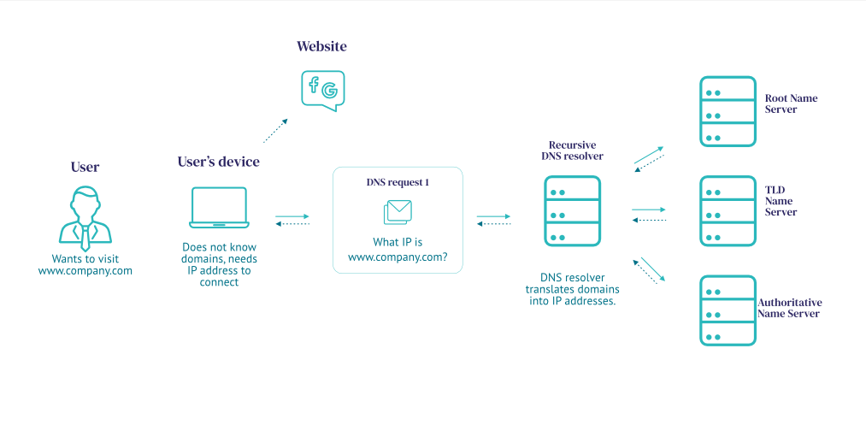
How it works?
- The bad actor has a server running malware and he points a domain to it.
- The bad actor infects a host malware to query for the attacker-controlled domain.
- When the DNS resolver routes the query, it creates a tunnel from the attacker to their target, allowing them to get data, remotely control the host, or otherwise take the next step in the attack chain.
Assets out of Network Attacks
Company owned and managed devices now move between many networks. Hybrid workers, workers in field, travelling workers, point their DNS traffic to their ISP or public wifi. Companies lose control over the security of the DNS traffic on these devices
How it affects you?
- Public wifi networks are ideal for dropping malware and man-in-the-middle attacks.
- Employees working from home rely on their ISP. ISPs have typically don’t filter DNS traffic because it results in customer call in.
- These devices come back into your network and infect your network
Compromised Credentials
Companies often don’t have credential policies in place. Users reuse the same password across multiple sites. The dark web is full of sites offering login details and personal data.
How it affects you?
-
A bad actor can gain access to your network via a stolen login and password.
-
Leaked personal data of your customers, employees, patients, etc., naturally results in financial and reputational damages
Protective DNS Protection
Protective DNS (PDNS) is a security service that analyzes DNS queries to stop threats, using the existing DNS system. It blocks access to malware, ransomware, phishing attacks, viruses, harmful websites, and spyware at the source, making your network more secure.
PDNS uses Response Policy Zone (RPZ) functionality, a policy-driven DNS resolver that responds based on set criteria. It checks both domain name queries and returned IP addresses against threat intelligence, using real-time data from public and private sources to compile a list of sites with known malicious content. The DNS resolver then blocks connections to these dangerous sites.
When PDNS encounters a malicious or suspicious query, it can respond in various ways. It may block access to the requested domain by returning an NXDOMAIN response, indicating no IP address for the domain. It can also redirect the request to an alternative page that informs the user that the original domain has been blocked. Additionally, PDNS can “sinkhole” the domain, providing a custom response and preventing or delaying further cyber threats like ransomware or command-and-control protocols. This approach allows cybersecurity teams to investigate and respond to threats while they are still active.
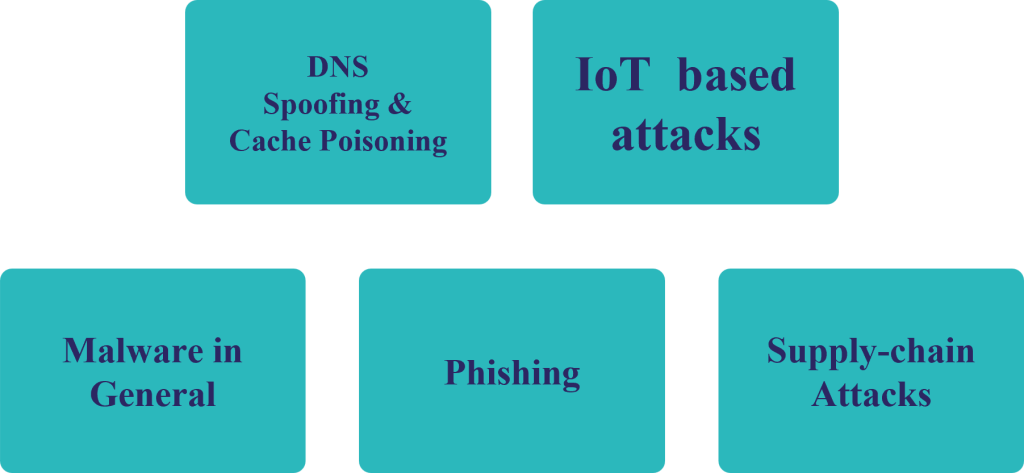
DNS Spoofing
DNS Spoofing refers to any type of malicious activity that alters DNS records returned to the user and thus point him/her to a malicious domain. These typically include DNS hijacking, cache poisoning, and man in the middle attacks.
DNS hijacking happens when a user’s query is improperly resolved and sends the user to a malicious domain instead of the domain they wanted.
Cache Poisoning is when a bad actor alters the DNS record to send the user to a malicious site that resembles the legitimate site. This is used a lot for login pages and stealing login credentials.
Man-in-the-middle is when a bad actor inserts himself into communication between two parties, impersonates both of them, and gains access to the information the two parties are sharing.
How it works?
Typically, there are 3 steps:
- Recon – MAC address, software version and know vulnerabilities, communication protocols, encryption algorithms, DNSSEC being used.
- Access – Bad actor accesses DNS recursive server and adds fake DNS entries to reroute DNS queries to his server.
- Attack – clients now start going to the fake login page for their bank and the bad actor has just stolen your login credentials and starts emptying your account.
IoT based attacks
Printers, cameras, servers, medical equipment, industrial machines — anything connected to the internet is both vulnerable and a vulnerability for the network.
How it works?
In vast majority of cases, you can’t install an end-point protection to them, which is often abused by hackers, adding the devices to C&C network for DDoS attacks or using their embedded legacy software for a supply-chain attack.
Malware in General
Malware is any malicious software
How it works?
Malware is any malicious software. It needs to infiltrate the network, gain a foothold, spread, and then take some action — no attack is a simple process and a successful attack means that network’s security measures failed on multiple occasions.
Adding a DNS layer to the security perimeter means that if malware falls through the standard security stack, there still a chance to stop it from spreading and causing damage.
Phishing
Using fake messages, websites, banners, etc. to scam users, often to make them disclose their credentials or to download malware.
How it works?
To launch a phishing attack, the attackers need a domain — and if it pops up in any of Whalebone databases, if any user tries to access it for example through an e-mail which looks like it came from HR, they are stopped immediately.
Supply Chain Attacks
Using a vulnerability of a trusted 3rd-party software to sneak behind the security perimeter to gain foothold in the target network, spread malware, etc.
How it works?
The attackers find a vulnerability in a software which is widely used and use it to smuggle malicious payload into the network. Unfortunately, given that the trusted software is trusted by security measures, there is little anyone can do to prevent the drop. Nevertheless, it is possible to stop the consequence via severing the communication of the payload with the attacker.
Whalebone Immunity Solution as DNS Protection
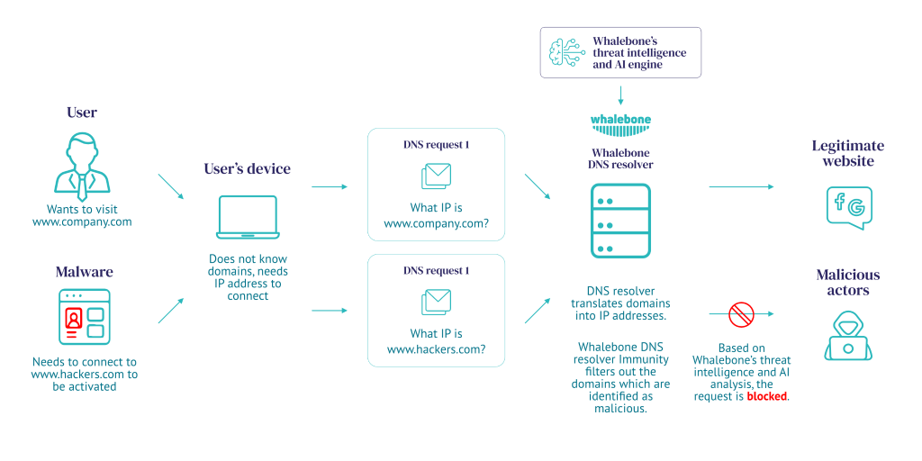
DNS Protection with Sophos Firewalls
Since beginning of this year, Sophos launched DNS protection as part in their Xstream protection license of their XGS Firewalls.
Sophos DNS Protection adds an important value for existing or renewing firewall customers who get this added protection at no extra charge. It enables them to potentially consolidate and save from using another 3rd party DNS provider or start using a great DNS Protection solution without having to pay extra.
What adds DNS Protection to XGS Firewalls?
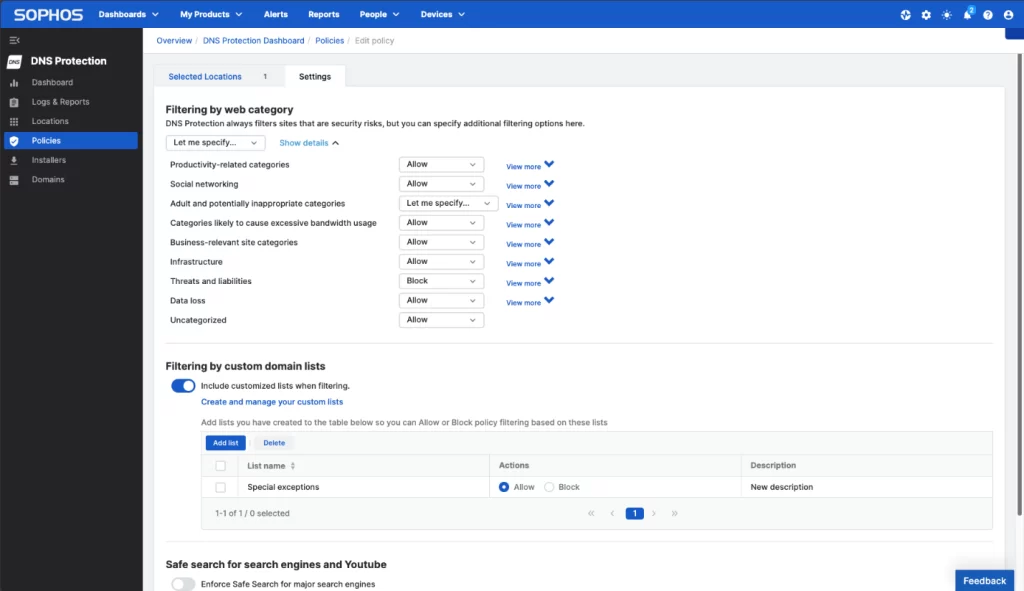
Sophos DNS Protection adds an extra layer of security to your network by blocking access to dangerous and unwanted domains across all ports, protocols, and applications instantly, whether from managed or unmanaged devices. It seamlessly complements and enhances your current network security measures and policy enforcement tools, and can be set up in just a few minutes.
Sophos DNS Protection offers a globally accessible domain name resolution service with integrated policy controls and reporting within Sophos Central. It leverages AI-powered threat intelligence from SophosLabs, providing real-time protection from high-risk domains worldwide. When a malicious domain is detected, it is immediately shared across all users, ensuring instant protection for everyone. By using Sophos DNS Protection instead of your existing public DNS resolver, you can prevent any device on your network from accessing domains associated with security threats and unwanted websites, all managed through policy controls.
Protection networks with Sophos DNS Protection
Access to the Sophos DNS Resolver is based on the originating public IPv4 address of the DNS queries. Hence, protecting individual devices for remote workers that move from network to network (or site to site) is not viable at this time.
Dynamic IP addresses are supported when used with a DynamicDNS provider.
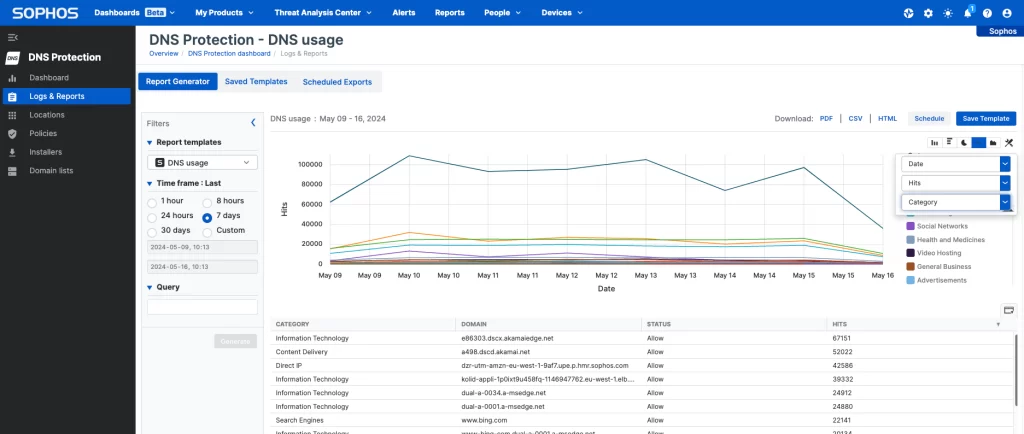
Integrated Dashboarding and Reporting
Sophos DNS Protection also provides in-depth visibility into the domains visited from your network with comprehensive dashboarding and reporting.
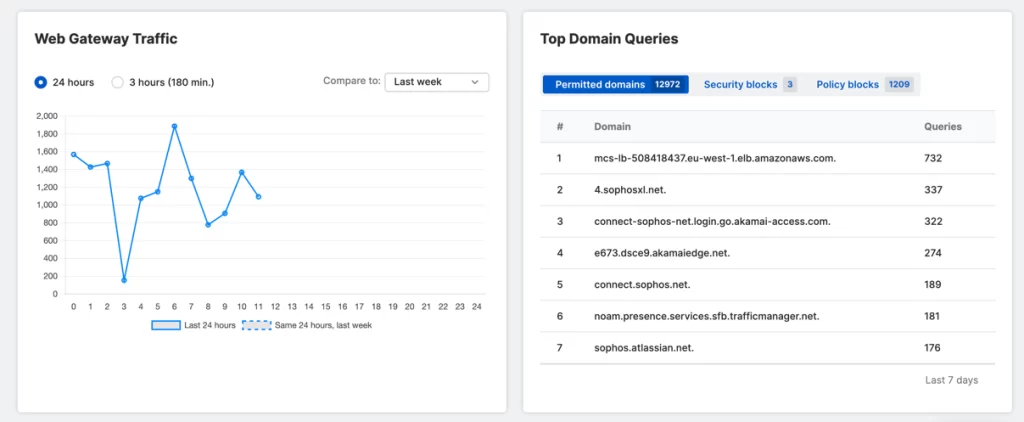
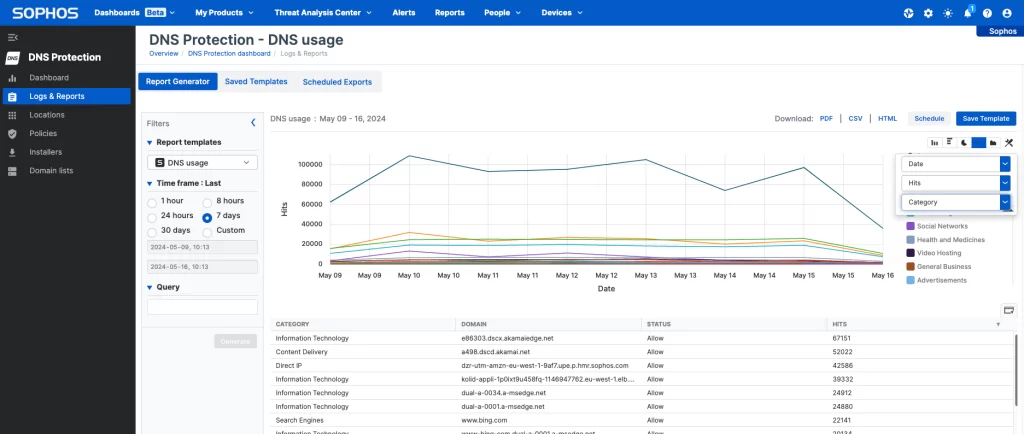
Cross product integration
Sophos DNS Protection’s log data and intelligence are also shared with the Sophos data lake for Sophos XDR and MDR threat-hunting analysts to help detect active adversaries and threats operating on the network.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow can DNS protection solutions like Whalebone Immunity and Sophos DNS Protection increase overall cybersecurity?
DNS protection solutions increase overall cybersecurity by:
- Preventing access to malicious sites: Blocking harmful domains at the DNS level stops threats before they can reach the network.
- Reducing the risk of infections: By intercepting and blocking malware and ransomware domains, DNS protection reduces the likelihood of endpoint infections.
- Protecting against phishing attacks: Blocking access to phishing sites prevents users from inadvertently disclosing sensitive information.
- Enhancing visibility: Providing detailed reports on DNS requests helps organizations identify and respond to suspicious activities.
- Simplifying management: Centralized management and policy enforcement make it easier to maintain consistent security across the organization.
How does Sophos DNS Protection work to safeguard organizations?
Sophos DNS Protection works by intercepting DNS requests and comparing them against a continuously updated list of known malicious domains. When a user attempts to access a harmful site, the request is blocked, and the user is redirected to a safe page. This proactive approach prevents threats from reaching the network and protects users from phishing, malware, and other cyber attacks.
How does Whalebone Immunity enhance network security?
Whalebone Immunity enhances network security by continuously monitoring and filtering DNS traffic to block access to known malicious domains. It uses threat intelligence and real-time data analysis to identify and prevent cyber threats, ensuring that users cannot inadvertently access harmful websites.
What are the key features of Sophos DNS Protection?
Key features of Sophos DNS Protection include:
- Advanced threat intelligence: Utilizes SophosLabs’ threat intelligence to block malicious domains.
- Content filtering: Blocks access to inappropriate or harmful content based on customizable categories.
- Phishing and malware protection: Prevents access to phishing sites and malware distribution points.
- User and device visibility: Provides detailed reporting and visibility into DNS requests from users and devices.
- Integration with Sophos Central: Offers centralized management and reporting through the Sophos Central platform.
What are the key features of Whalebone Immunity?
Key features of Whalebone Immunity include:
- Real-time threat intelligence: Uses up-to-date threat data to block malicious domains.
- Comprehensive DNS filtering: Monitors and filters all DNS traffic to protect against cyber threats.
- Customizable policies: Allows organizations to set policies for different user groups and customize blocking rules.
- Detailed reporting: Provides insights into blocked threats and DNS traffic patterns.
- Easy integration: Can be easily integrated into existing network infrastructure without requiring significant changes.
What is Sophos DNS Protection?
Sophos DNS Protection is a security service that safeguards organizations by preventing access to malicious websites and blocking harmful content at the DNS level. It integrates with Sophos Central to provide comprehensive protection against internet-based threats, including phishing, malware, and ransomware.
What is Whalebone Immunity?
Whalebone Immunity is a DNS-based cybersecurity solution designed to protect networks from cyber threats by blocking malicious domains and preventing users from accessing harmful websites. It operates at the DNS level to filter traffic and protect against phishing, malware, ransomware, and other cyber threats.
Which types of organizations would benefit the most from using DNS protection solutions like Whalebone Immunity and Sophos DNS Protection?
Organizations of all sizes and industries can benefit from DNS protection solutions, especially those that:
- Handle sensitive data: Such as financial institutions, healthcare providers, and government agencies.
- Have distributed workforces: Including remote and hybrid work environments.
- Require strong regulatory compliance: Organizations needing to comply with standards like GDPR, HIPAA, and PCI DSS.
- Face high volumes of web traffic: E-commerce, educational institutions, and large enterprises.
Why is DNS protection important for cybersecurity?
DNS protection is crucial for cybersecurity because it acts as the first line of defense against internet-based threats. By filtering DNS requests and blocking access to malicious domains, DNS protection prevents threats from reaching the network, reducing the risk of infections and data breaches.
Why should an organization consider implementing Whalebone Immunity or Sophos DNS Protection?
An organization should consider implementing Whalebone Immunity or Sophos DNS Protection to:
- Enhance threat prevention: Stop threats before they reach the network and compromise systems.
- Improve security posture: Strengthen overall cybersecurity defenses by adding a critical layer of protection.
- Simplify security management: Centralized policies and reporting streamline security operations.
- Reduce the impact of cyber attacks: Proactively blocking threats minimizes the potential damage from cyber incidents.
- Ensure compliance: Meet regulatory requirements for protecting sensitive data and maintaining secure network operations.
Contact us for a demo
Are you curious to learn how Whalebone and Sophos can help you in having an extra security layer in the Supply Chain? Contact us for a demo via the below button.