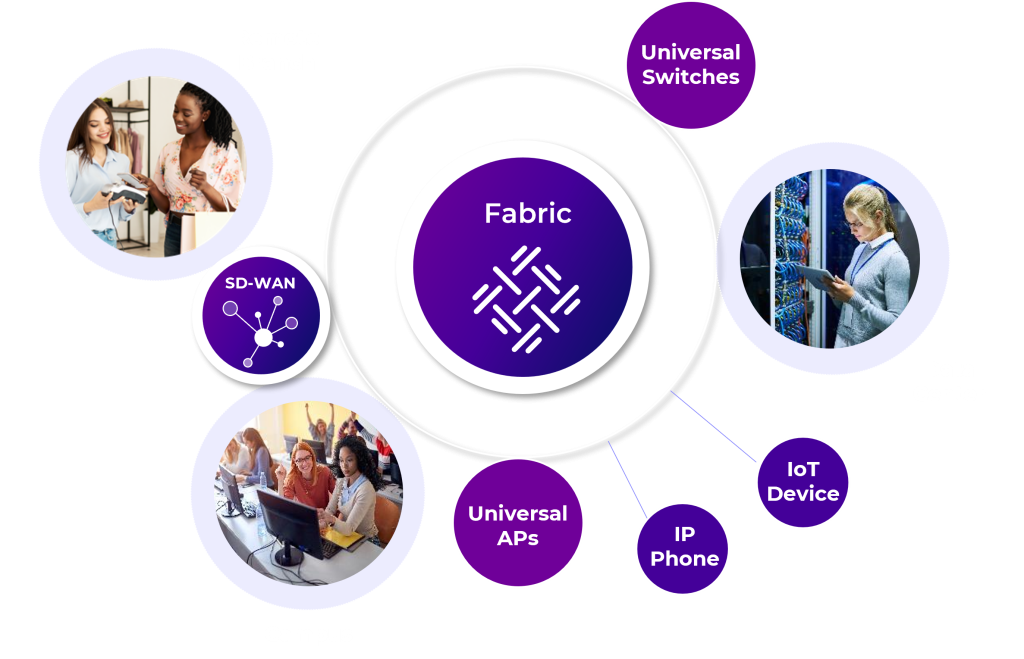
Fabric Network
Extreme Fabric Connect provides a Unified, Automated, and Secure network solution that extends across multiple locations and device types, as well as streamlining deployments while isolating threats.
Traditional networking
Fabric networking is different from traditional networking. That’s for sure. But where di did it all start?
Let’s take a look at traditional networking… We come from far.
- Shared Media Networks: Early networks relied on shared media, where all devices competed for access. This led to collisions and inefficiencies.
- Hub-Based Networks: Hubs acted as multiport repeaters, operating at Layer 1 (physical layer), but lacked intelligent traffic management. These networks suffered from congestion and limited scalability.
- Switched Networks: Layer 2 switches were introduced, operating at the data link layer and enabling more efficient data transfer by forwarding frames based on MAC addresses. This reduced collision domains and improved network performance.
- VLANs: Virtual LANs were introduced to logically segment networks, providing enhanced security, manageability, and traffic control within a single physical infrastructure.
Actually it’s great. We now have switched networks, and we can use VLANs. But still… There is a lot that’s ugly about the traditional technologies. One of the drawbacks that gives a lot of engineers headaches is Spanning Tree. It gives us a lot of limitations.
STP is crucial for preventing loops in redundant network topologies, but has limitations in scalability and convergence time, limiting the scale and agility of networks.
As networks grow larger, and are more complex, managing them becomes increasingly challenging, with configuration issues, scalability limitations, and longer convergence times.
Traditional networks, based on hierarchical designs, have scalability limitations due to these spanning tree protocols, VLAN constraints, and manual configurations. As networks grow, managing them becomes complex and resource utilization is inefficient due to rigid architectures and manual provisioning.
Legacy networks often require manual configurations which are time-consuming and prone to errors, hindering agility and rapid deployment of services.
Also troubleshooting network issues becomes intricate and time-intensive due to complexity of configurations and limited visibility into network behaviour.
That’s where fabric networking kicks in. The Fabric Connect infrastructure is based on SPB (Shortest Path Bridging). SPB is standardized under IEEE 802.1aq, aimed to simplify large Ethernet networks by utilizing shortest path forwarding, supporting massive Layer 2 topologies, and enhancing network scalability.
It started by stepping back and taking a fresh look into what is good, bad and ugly about Ethernet and MPLS.
What’s good and what’s bad about Ethernet?
- Good: Simplicity of L2 forwarding
- Bad: Limitations of 802.1Q VLAN tags for virtualization
- Ugly: Dependence upon STP
What’s good and what’s bad about MPLS?
- Good: Scalability of solution, network virtualization capabilities
- Bad: Complexity – using a series of protocols to transport L2 Ethernet and L3 IP
- Ugly: Proliferation of additional protocols required.
Let’s take the good things from Ethernet and MPLS, and introduce it in this Fabric technology. Wouldn’t that be great?
Fabric Networking
When we take all the goodies from Ethernet and MPLS and introduce it to the Fabric technology, we can get the following results :
- A new simplified way to design, build and manage networks
- All the network services you need with just a single technology
- Multiple independent L2/3 cloud-based networks deployed with ease and scale
- Field proven across the globe, in every vertical industry
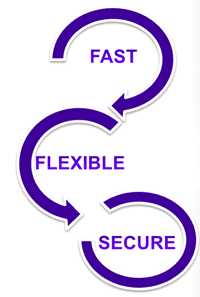
Fabric is all about value. And the value proposition of the technology revolves around 3 key concepts.
Fabric is FAST!
- 11x Faster time to service; provision at the “edge”, the core is automatically provisioned
- 7x Faster mean time to repair
- 2500x Faster reconvergence
Fabric is FLEXIBLE!
- Extend services anywhere seamlessly
- 4-10 protocols to 1; L2, L3, VRFs
- 28x better multicast scaling
Fabric is SECURE!
- Isolates traffic end to end with ease and scale
- Contains breaches; prevents lateral movements
- Network invisibility to users
And it really is. Let’s take a look at the comparison between the complex protocol stack we already know, and how Fabric Connect looks like. All these protocols are combined into just one.
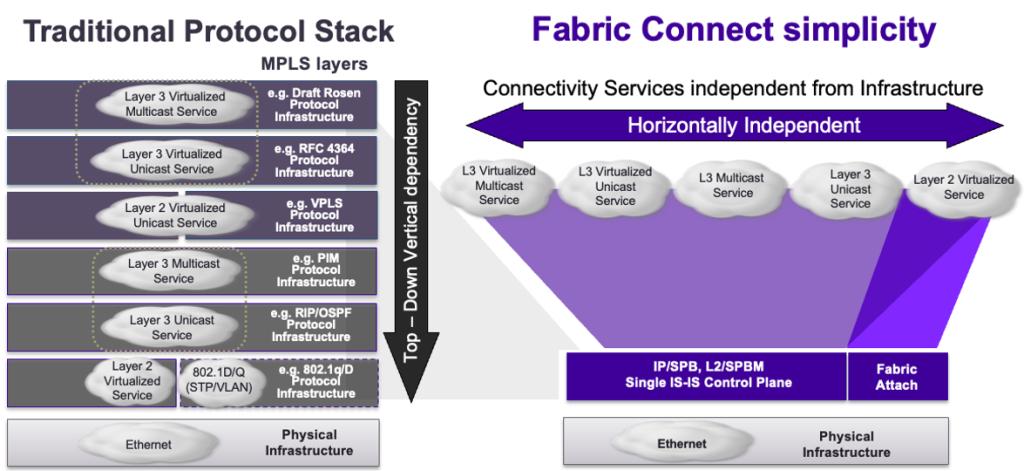
Fabric isn’t a magic thing. Well, it looks like magic, but it is fundamentally built on existing concepts. As everything else, it is also using science and mathematics. Remember the Dijkstra algorithm? Well, that’s one of the key fundamental items of Fabric Connect.
Esger W Dijkstra was a pioneering computer scientist from the Netherlands, known for his significant contributions to the field of computer science. He studied theoretical physics at Leiden University but later shifted his focus to computer science. He worked at the mathematical Center in Amsterdam, where he developed many of his early ideas. He held academic positions at several institutions, including the Eindhoven University of Technology and the University of Texas at Austin.
Dijkstra made numerous contributions to computer science, including work on algorithms, programming languages and software engineering. One of his key contributions is the Dijkstra’s algorithm which also is one of the major fundamentals of Fabric Connect.
Dijkstra’s algorithm is a graph search algorithm that solves the single-source shortest path problem for a graph with non-negative edge weights. In short, you always find the shortest path from A to B. In a switching network, there are redundant paths and possible loops. It’s necessary to always use the shortest path (cable length, interface speed, loops,…) to have a stable, flexible and fast switching network. As Fabric Connect is completely built on top of this graph algorithm, this results in a fast, stable and redundant switching network without the complexity of configuring STP.
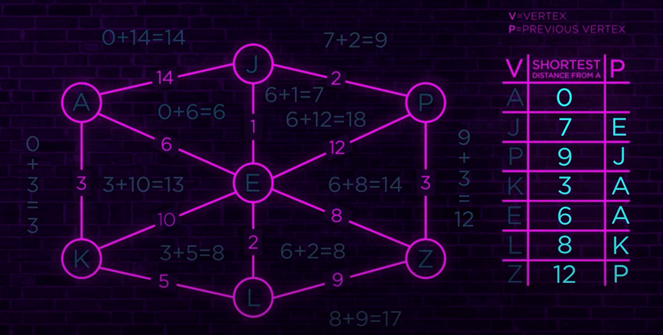
When you read about Fabric Connect, you will see SPBM and not only SPB. SPBM stands for Shortest Path Bridging / MAC-in-MAC. This means that Fabric Connect uses a combination of Shortest Path Bridging with MAC-in-MAC encapsulation, which means that every packet that enters the Fabric will use the MAC address of the switch where it enters the fabric.
MAC-in-MAC encapsulation is designed to address the scalability issues of traditional Ethernet networks by encapsulating customer MAC addresses with provider MAC addresses. This helps in reducing the size of the forwarding tables in the provider network and isolates customer traffic.
Besides the scalability benefit, there is also a security benefit of using MAC-in-MAC encapsulation. By encapsulating customer frames within provider frames, MAC-in-MAC effectively isolates customer traffic. This means that traffic from different customers is kept separate, reducing the risk of data leakage or unauthorized access between customers.
The encapsulation also hides the customer MAC addresses from the provider network, preventing potential attacks on the provider’s infrastructure that could exploit customer MAC addresses. In the core, you are not able to see any customer MAC addresses when you try to inspect the traffic. This enhances privacy and makes it more difficult for attackers to gather information about the customer network.
When talking about Fabric Connect, we always talk about two types of switches. We have the BCB switches (Backbone Core Bridge) and BEB switches (Backbone Edge Bridge).
- The BCB is only concerned with routing. It’s job (along with the other BCB’s in the fabric) is to make sure that all the traffic between the services is routed in the most efficient way possible (by using SBPM)
- Fabric Connect uses the IS-IS routing protocol to communicate with each other in order to determine the best route for data through the network
- This is not only automatically done, it’s also self-healing. If a BCB runs into issues, the other BCBs will simply route around it to keep the network running.
Let’s take a look at the following figure
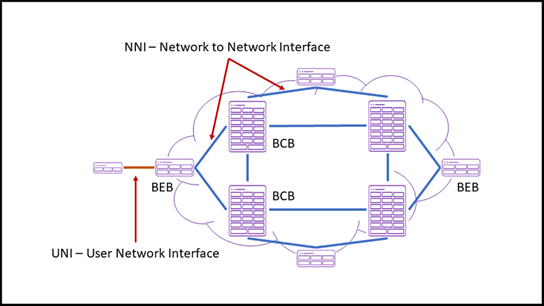
- Each BCB is told about the links it has directly to other BCBs. These links are called “Network to Network Interfaces” or NNIs
- It is important to note that each BCB is only configured with the NNIs directly attached. This prevents the configuration complexity growing every time a new BCB is added
- Each additional BCB only affects the configuration of its direct peers. The new BCB will “learn” about all the other core switches through IS-IS
- With every additional BCB and every additional NNI, the Fabric Connect network grows and more importantly becomes more resilient
- While Fabric networks can support the same topologies as the traditional networking, the topology becomes generally less much of an issue anyway
- When service traffic is presented to the core network, Fabric Connect automatically calculates the most efficient path through the network (by using SPBM). You can add additional paths or remove paths (deliberately or due to failure) and the core network will automatically work its way around it.
Like in every switching network, there’s more than the core. Actually the switches where end-devices are connecting on, are the edge switches or access switches. Within the Fabric Connect network, we are talking about BEBs or Backbone Edge Bridges.
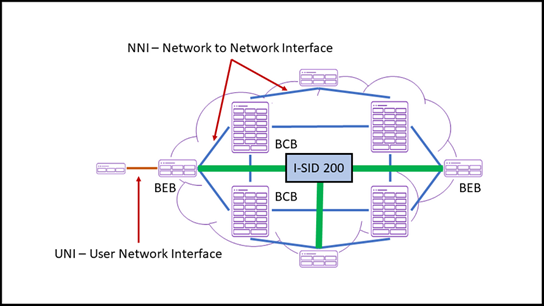
- The BEB is concerned with services and routing. The simplest way to visualize a service is to consider a distinct Layer 2 network which automatically connects between two or more BEBs. Each service is uniquely identified by an I-SID (Service Identifier) and Extreme’s Fabric Connect supports more than 16 million services per network. Remember the limit of around 4000 VLANs? That’s a lot more!
- Since or routing is encapsulated by the BCBs, the core network can be considered as a bubble. BEBs are placed around the edges of the bubble and then services are connections between the BEBs.
One of the main advantages of Fabric Connect is that all communication via an I-SID is tunneled through the core-network. So, each ‘elastic’ layer 2 network is private, making it much harder for would-be hackers to move laterally across the network.
The same advantages are true for Layer 3 as well. If you would run some tools like traceroute from a workstation, your network topology would be completely invisible. This is often called “hyper-segmentation” as each of the 16 million services are automatically segmented from one-another, and the tunnels only exist for as long as the service is in use. So, Fabric Connect is not only easier to manage, but also far more secure by design.
Talking about easy to manage, Fabric Connect also has a concept called “Auto-sense” which works together with the “Zero-touch-provisioning”.
Zero-touch fabric-infrastructure is a major enhancement. There are three components to this
- Zero-touch on-boarding of Fabric Engine devices
- Zero-touch provisioning of Fabric Connect Network to Network Interfaces (NNIs)
- Zero-touch Fabric Attach
Auto-sense ports can be thought of as intelligent ports that are able to detect what is being plugged into them and then can apply the right configuration dynamically. If there is a seed switch in the network, the Fabric infrastructure can self-form and self-provision without any manual intervention. And this can happen whether you have 5 new switches, 50 new switches or even 500 new switches.
Auto-sense ports also detect when a Fabric Attach enabled device (switch, AP, SD-WAN appliance or any other Fabric Attach capable device) is connected and enables Fabric Attach Server functionality dynamically.
When none of the above is the case, auto-sense mode will start using EAP against a Network Access Control solution so that your client connects via RADIUS towards the correct I-SID.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow does Extreme fabric Connect differ from traditional networking?
Extreme Fabric Connect differs from traditional networking by using a mesh-like architecture that allows for more efficient and direct communication between devices. This reduces latency, improves redundancy, and simplifies network management compared to traditional hierarchical networking models that rely on a more rigid, tree-like structure.
How does Extreme Fabric Connect enhance network performance?
Extreme Fabric Connect enhances network performance by:
- Reducing latency: Direct paths between devices minimize the number of hops and delays.
- Increasing throughput: Efficient data routing and load balancing improve overall bandwidth utilization.
- Optimizing traffic flows: Intelligent routing algorithms ensure optimal paths for data transmission.
How does Extreme Fabric Connect improve network resilience and reliability?
Extreme Fabric Connect improves network resilience and reliability by:
- Providing redundancy: Multiple paths between devices ensure continuous connectivity even if one path fails.
- Enabling fast failover: Automated failover mechanisms quickly reroute traffic in case of link or device failures.
- Supporting load balancing: Distributes traffic evenly across available paths, preventing congestion and bottlenecks.
How does Extreme Fabric Connect simplify network scalability?
Extreme Fabric Connect simplifies network scalability by allowing for easy addition or removal of devices and links without significant disruptions. Its mesh-like architecture supports horizontal scaling, enabling organizations to expand their network capacity seamlessly as their needs grow. Automated configuration and provisioning further facilitate rapid scaling.
What are the key benefits of using Extreme Fabric Connect for organizations?
Key benefits of using Extreme Fabric Connect for organizations include:
- Improved performance: Lower latency and higher throughput due to direct communication paths.
- Enhanced flexibility: Easy to scale and reconfigure network topology without major disruptions.
- Greater resilience: Built-in redundancy and automated failover capabilities.
- Simplified management: Centralized control and automated configuration reduce operational complexity.
- Better security: Segmentation and isolation capabilities enhance network security.
What are the security advantages of using Extreme Fabric Connect?
Security advantages of using Extreme Fabric Connect include:
- Network segmentation: Isolates different segments of the network to contain security breaches and limit their impact.
- Enhanced visibility: Centralized monitoring and management provide better insights into network activities.
- Policy enforcement: Consistent security policies can be applied across the network to ensure compliance and protect sensitive data.
What is Extreme Fabric Connect?
Extreme Fabric Connect is a high-performance networking architecture that leverages fabric technology to provide scalable, flexible, and resilient connectivity across an organization’s network. It uses advanced protocols to create a mesh-like structure that simplifies network management and enhances performance.
What role does automation play in Extreme Fabric Connect?
Automation in Extreme Fabric Connect plays a critical role in simplifying network management. It enables automated provisioning, configuration, and maintenance of network devices, reducing the need for manual intervention. Automation also helps in quickly adapting to changing network demands and ensures consistent policy enforcement across the network.
Why is Level 2 communication between switches essential for the flexibility of a network?
Level 2 communication between switches, also known as Layer 2 communication, is essential for network flexibility because it allows devices to communicate directly within the same broadcast domain. This enables seamless and efficient data flow, simplifies network design, and allows for dynamic reconfiguration and scaling without significant changes to the underlying infrastructure.
Why should organizations consider adopting Extreme Fabric Connect over traditional network architectures?
Organizations should consider adopting Extreme Fabric Connect over traditional network architectures because it offers numerous advantages, including:
- Higher performance: Reduced latency and improved throughput enhance overall network efficiency.
- Greater flexibility: Simplified scalability and reconfiguration meet evolving business needs.
- Increased resilience: Built-in redundancy and automated failover ensure continuous network availability.
- Enhanced security: Advanced segmentation and centralized management bolster network security.
- Reduced complexity: Automation and centralized control streamline network operations and reduce management overhead.
Contact us for a demo
Are you curious to learn how Extreme Fabric can help you to automate network management and increase the performance of your network? Contact us for a demo via the below button.
