Data Protection
Data protection at rest or in transit are requirements within NIS2. Data protection can apply for a variety of applications, like database, network data, device data or application data. On this page we will highlight the different type of solutions that are interesting to consider

The importance of data protection
Data Protection for data-at rest
Barracuda Backup

Both IoT and OT systems can be a potential danger for a network. Unpatched and unsecured systems can give hackers access to the network and allow them to use the zombie system as a jumping off point. Some of these assets are cloud ma
Identity and Access Management
In an era where data breaches and unauthorized access are increasingly common, protecting data-at-rest is essential for maintaining the confidentiality and security of sensitive information. One Identity’s Identity and Access Management (IAM) solutions provide a robust approach to safeguarding data-at-rest by ensuring that only authorized users can access critical data stored within your organization.
With One Identity IAM, organizations can implement precise access controls, enforce strong authentication protocols, and manage user permissions with ease. This comprehensive approach not only prevents unauthorized access to data-at-rest but also helps organizations maintain compliance with regulatory standards. By leveraging One Identity’s IAM solutions, businesses can secure their sensitive data, reduce the risk of insider threats, and confidently protect their valuable assets in today’s complex digital landscape.
Onespan Digital Identity and Authentication
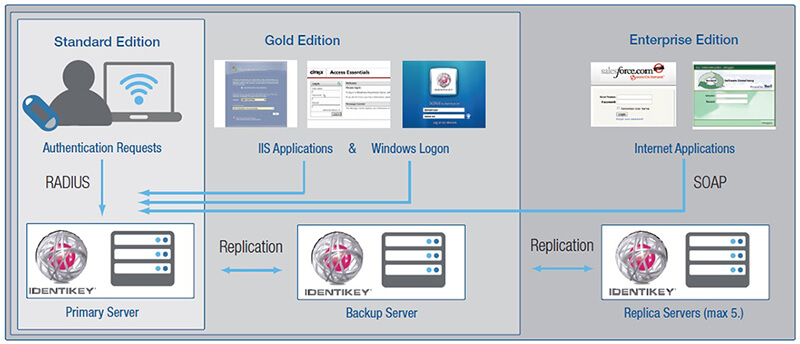
Securing data-at-rest is a fundamental aspect of protecting an organization’s sensitive information from unauthorized access and potential breaches. Onespan’s Digital Identity and Authentication solutions offer a powerful way to safeguard data-at-rest by ensuring that only verified and authenticated users can access critical stored data.
Onespan’s solutions utilize advanced authentication methods, such as multi-factor authentication (MFA), to create strong barriers against unauthorized access. By securing user identities and verifying access attempts, Onespan helps organizations protect their data-at-rest, ensuring that even if data is physically accessed, it remains secure and inaccessible to unauthorized parties. With Onespan, businesses can confidently protect their sensitive data, comply with regulatory requirements, and mitigate the risks associated with unauthorized access in a rapidly evolving digital environment.
The latest generation of Authentication goes with their new solution Digipass FX1 Bio that offers passwordless authentication.
Sophos Device Encryption
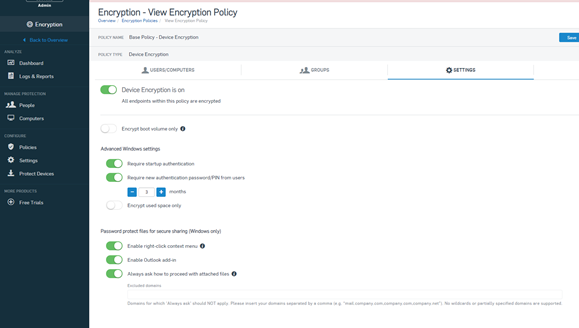
Data-at-rest is vulnerable to unauthorized access, especially if devices fall into the wrong hands. Sophos Device Encryption safeguards this data by encrypting the entire disk or selected files, making the information unreadable without the correct decryption key. This level of protection is crucial for preventing data breaches, maintaining regulatory compliance, and ensuring the confidentiality of sensitive information.
Main Advantages for Administrators Using Sophos Device Encryption:
-
Centralized Management:
- Sophos Device Encryption integrates seamlessly with Sophos Central, allowing administrators to manage encryption policies, monitor compliance, and oversee all encrypted devices from a single, intuitive dashboard. This centralized management reduces complexity and ensures consistent application of security policies across the organization.
-
Compliance and Reporting:
- With built-in reporting tools, administrators can easily demonstrate compliance with regulatory standards such as GDPR, HIPAA, and others that require encryption of sensitive data. Sophos provides detailed audit logs and reports that are essential for compliance audits and risk management.
-
User-Friendly Experience:
- Sophos Device Encryption is designed with both administrators and end-users in mind. The encryption process is transparent to users, with minimal impact on device performance. This ensures that security measures do not disrupt productivity while still providing strong protection.
-
Enhanced Security Features:
- The solution includes additional security features such as multi-factor authentication (MFA) and integration with Sophos’ broader security ecosystem. This layered approach strengthens overall data protection by combining encryption with other security measures.
-
Scalability:
- Whether managing a small business or a large enterprise, Sophos Device Encryption scales to meet the needs of any organization. Administrators can easily add new devices, apply policies, and ensure that all data-at-rest across the organization remains protected.
In summary, Sophos Device Encryption is an essential tool for any organization seeking to protect its data-at-rest. By encrypting sensitive information and providing powerful management tools, it allows administrators to effectively secure their data, comply with regulations, and minimize the risk of data breaches, all while maintaining a user-friendly experience for employees.
Data Protection for data-in transit
Barracuda Email Protection
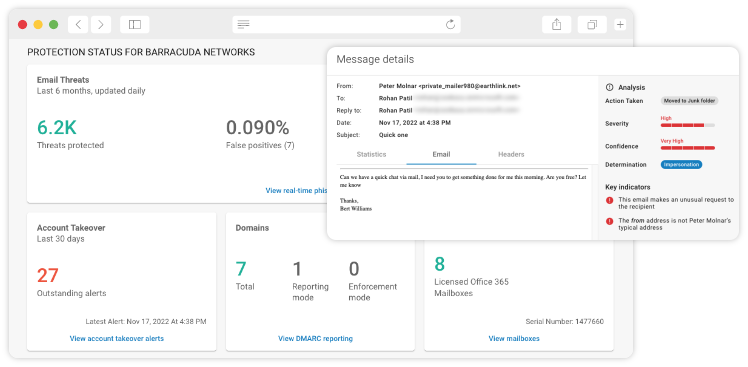
Email remains a primary communication tool for businesses, but it is also a significant vector for cyber threats, including phishing, malware, and ransomware attacks. Protecting the sensitive data exchanged through email is crucial to maintaining security and compliance. Barracuda offers industry-leading email protection solutions designed to safeguard your organization’s email communications from these evolving threats.
Barracuda’s email protection suite provides advanced security features such as real-time threat detection, email encryption, and comprehensive filtering, ensuring that sensitive data is protected both in transit and at rest. By blocking malicious content before it reaches your inbox and securing emails with strong encryption, Barracuda helps prevent data breaches and unauthorized access to confidential information.
With Barracuda’s email protection, you can confidently protect your organization’s data, maintain regulatory compliance, and ensure that your email communications remain secure and reliable.
Barracuda Web Application Firewall (WAF)

Data in transit is particularly vulnerable to attacks such as man-in-the-middle (MitM), cross-site scripting (XSS), and SQL injection, where attackers attempt to intercept, modify, or steal information as it moves between users and web applications.
The Barracuda Web Application Firewall mitigates these risks by enforcing SSL/TLS encryption, which secures the communication channel and ensures that data remains protected from eavesdropping and tampering. Additionally, the WAF provides real-time protection against a wide range of application-layer threats, preventing malicious actors from exploiting vulnerabilities in web applications to access or compromise sensitive data.
Main Advantages for an Organization Using Barracuda Web Application Firewall:
-
Comprehensive Security for Web Applications:
- Barracuda WAF provides robust defense against OWASP Top 10 threats, including SQL injection, cross-site scripting, and other common vulnerabilities. This ensures that your web applications and the data they handle are protected from the most prevalent and dangerous attacks.
-
SSL/TLS Encryption Enforcement:
- The WAF enforces strong SSL/TLS encryption for all data in transit, ensuring that communication between users and applications is secure. This protects sensitive information, such as login credentials and financial data, from being intercepted or tampered with by unauthorized parties.
-
DDoS Protection:
- Barracuda WAF includes built-in DDoS protection to safeguard your applications from Distributed Denial of Service attacks that can overwhelm your servers and disrupt access to critical data and services. This ensures business continuity and availability, even during an attack.
-
Granular Access Controls:
- With Barracuda WAF, organizations can implement granular access controls, ensuring that only authorized users can access specific parts of the application or certain types of data. This minimizes the risk of unauthorized access to sensitive information.
-
Real-Time Threat Intelligence:
- The WAF is integrated with Barracuda’s global threat intelligence network, providing real-time updates and protection against emerging threats. This proactive approach helps organizations stay ahead of cyber threats, ensuring that data in transit remains secure.
-
Ease of Deployment and Management:
- Barracuda WAF is designed for easy deployment and management, whether on-premises, in the cloud, or as a hybrid solution. Its intuitive interface and automated security updates reduce the administrative burden, allowing IT teams to focus on other critical tasks.
Therefore, we can conclude that Barracuda Web Application Firewall is a crucial tool for protecting data in transit, ensuring that web applications remain secure and resilient against cyber threats. By providing robust encryption, real-time threat protection, and comprehensive security controls, Barracuda WAF helps organizations safeguard their sensitive data, maintain regulatory compliance, and protect their reputation in an increasingly hostile digital environment.
Cato Networks SASE
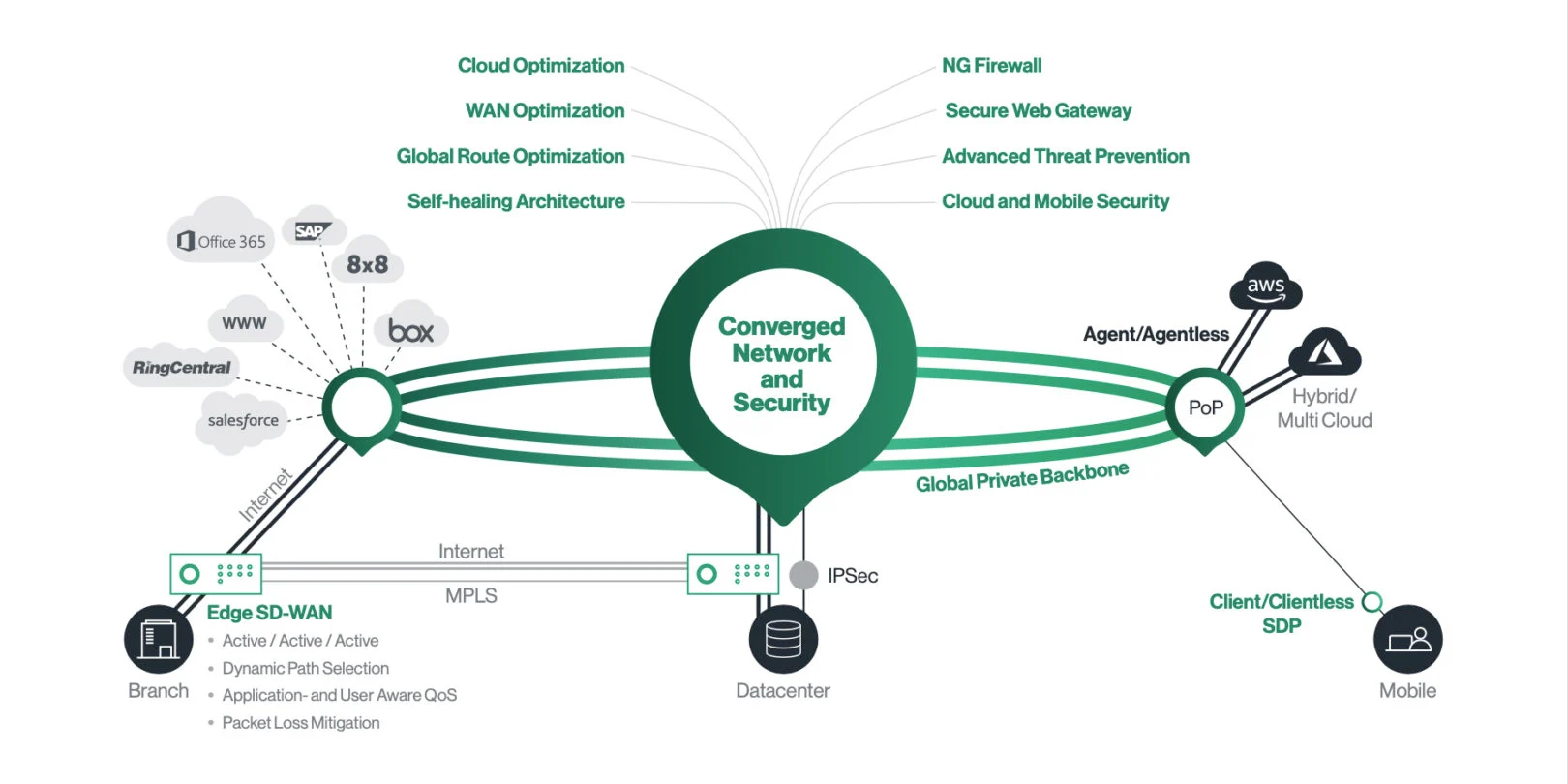
In an era where cloud adoption and remote work are becoming the norm, ensuring the security of data in transit has never been more critical. As organizations expand their digital footprints, data is constantly moving across various networks, making it vulnerable to interception, breaches, and other cyber threats. Cato Networks’ Secure Access Service Edge (SASE) solution provides a comprehensive approach to protecting data in transit, combining advanced security features with high-performance networking.
Cato’s SASE platform integrates secure SD-WAN with robust security services, including secure web gateways, next-generation firewalls, and zero-trust network access. This unified approach ensures that data is encrypted and protected as it travels between users, data centers, and cloud applications, regardless of location. With Cato Networks’ SASE solution, organizations can confidently secure their data in transit, ensuring that it remains safe from unauthorized access and tampering while maintaining the speed and reliability needed for modern business operations.
Secure Network Solutions with Extreme Networks
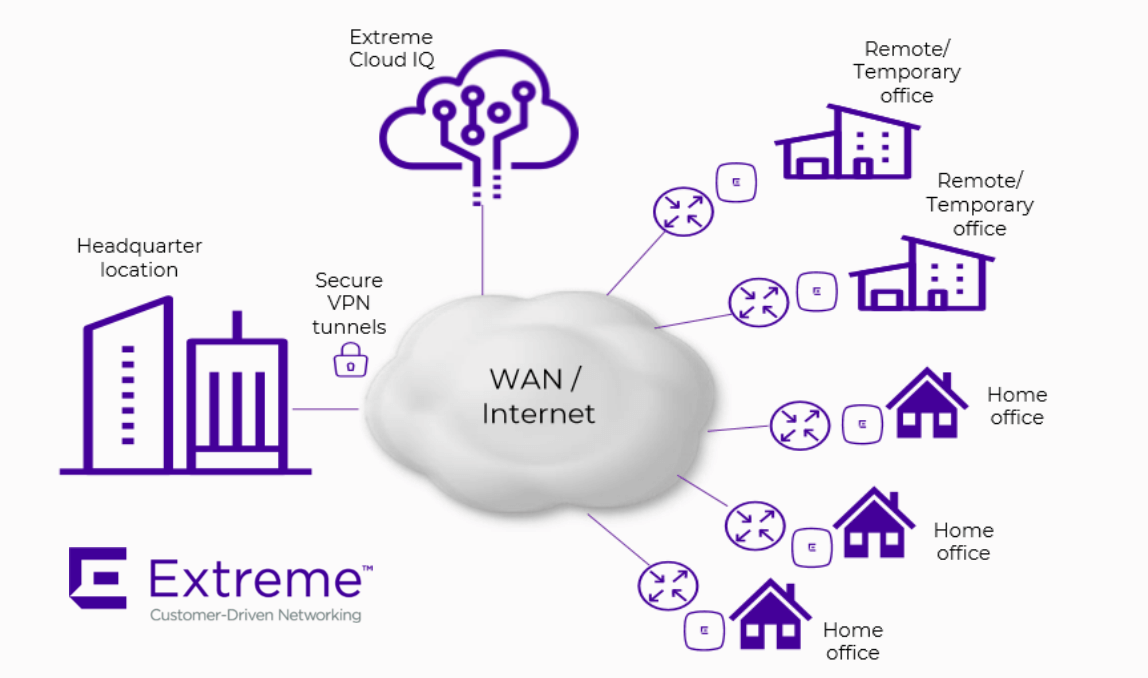
Securing Data in Transit with Extreme Networks: A Comprehensive Approach
In today’s interconnected world, securing data in transit is paramount for any organization that values the confidentiality, integrity, and availability of its information. As data moves across wireless networks, wired connections, and various endpoints, it becomes vulnerable to a range of cyber threats, including interception, unauthorized access, and tampering.
Extreme Networks offers a suite of products designed to protect data in transit, providing organizations with the robust security they need to defend against these evolving risks. This article explores how Extreme Networks’ solutions—including Wi-Fi, Wired, Network Access Control (NAC), Zero Trust Network Access (ZTNA), and Universal Zero Trust Network Access (UZTNA)—work together to ensure data in transit remains secure.
Extreme Networks Wi-Fi: Secure Wireless Connectivity
Wireless networks are an essential component of modern business infrastructure, but they also present significant security challenges. Data transmitted over Wi-Fi is particularly susceptible to eavesdropping, man-in-the-middle attacks, and unauthorized access. Extreme Networks’ Wi-Fi solutions offer advanced security features to protect data in transit:
- Encryption: Extreme Wi-Fi solutions support the latest encryption standards, such as WPA3, ensuring that all data transmitted over the wireless network is encrypted and secure from interception.
- Authentication: With strong authentication protocols, Extreme Wi-Fi ensures that only authorized devices and users can access the network, reducing the risk of unauthorized data interception.
- Role-Based Access: Extreme allows for granular control over network access, ensuring that users can only access the data and resources they are authorized to use, thereby minimizing the exposure of sensitive information.
Extreme Networks Wired: Secure Data Transmission Over Wired Connections
While wired networks are inherently more secure than wireless ones, they are not immune to threats. Extreme Networks’ wired solutions provide robust security to protect data in transit across physical network connections:
- MACsec Encryption: Extreme’s wired solutions support MACsec (Media Access Control Security), which encrypts data at Layer 2, ensuring that even if data is intercepted, it remains unreadable without the correct decryption keys.
- Secure Segmentation: Through VLANs (Virtual LANs) and other segmentation techniques, Extreme ensures that sensitive data is isolated within the network, reducing the risk of unauthorized access and lateral movement by attackers.
- Advanced Threat Protection: Extreme’s wired solutions integrate with security tools to monitor and protect against threats in real-time, ensuring that any malicious activity is detected and mitigated quickly.
Network Access Control (NAC): Ensuring Authorized Access
Extreme Networks’ NAC solutions play a crucial role in securing data in transit by controlling who and what can access the network:
- Device Authentication: NAC ensures that only trusted devices can connect to the network, protecting data in transit from unauthorized or compromised devices.
- Compliance Enforcement: Extreme NAC checks devices for compliance with security policies before allowing them access, ensuring that only secure, up-to-date devices can transmit data over the network.
- Real-Time Monitoring: Continuous monitoring of all network connections allows NAC to detect and respond to suspicious activity, protecting data in transit from emerging threats.
Zero Trust Network Access (ZTNA): Never Trust, Always Verify
The Zero Trust security model, implemented through Extreme’s ZTNA solution, is critical for protecting data in transit, especially in today’s decentralized networks:
- Strict Access Controls: Extreme ZTNA requires verification of each user and device before granting access to any network resources, ensuring that only authenticated and authorized entities can transmit or receive data.
- Micro-Segmentation: By segmenting the network into smaller, secure zones, ZTNA ensures that even if one part of the network is compromised, the attacker cannot easily access other areas, protecting data in transit from widespread breaches.
- Continuous Monitoring: ZTNA continuously monitors user activity and network traffic, providing real-time protection and ensuring that any anomalies or threats are quickly identified and mitigated.
Universal Zero Trust Network Access (UZTNA): A Unified Approach
Extreme Networks’ UZTNA takes Zero Trust security to the next level by providing a unified approach to securing data in transit across all network environments, including cloud, on-premises, and hybrid environments:
- Comprehensive Protection: UZTNA applies Zero Trust principles universally across the entire network, ensuring that data in transit is protected regardless of where it’s being transmitted or accessed.
- Seamless Integration: UZTNA integrates with existing Extreme security solutions, providing a cohesive security strategy that covers all aspects of the network, from Wi-Fi and wired connections to remote access and cloud resources.
- Adaptive Security: With UZTNA, security policies adapt in real-time based on the context of the access request, ensuring that data in transit is always protected by the most appropriate security measures.
Securing data in transit is a critical component of any organization’s overall cybersecurity strategy. Extreme Networks offers a comprehensive suite of solutions—encompassing Wi-Fi, wired networks, NAC, ZTNA, and UZTNA—that work together to provide robust protection for data as it moves across the network. By leveraging these solutions, organizations can ensure that their data remains confidential, secure, and protected from the ever-growing array of cyber threats, helping to maintain the integrity and reliability of their business operations.
Securing Data in Transit with Juniper-Mist Products: A Comprehensive Approach
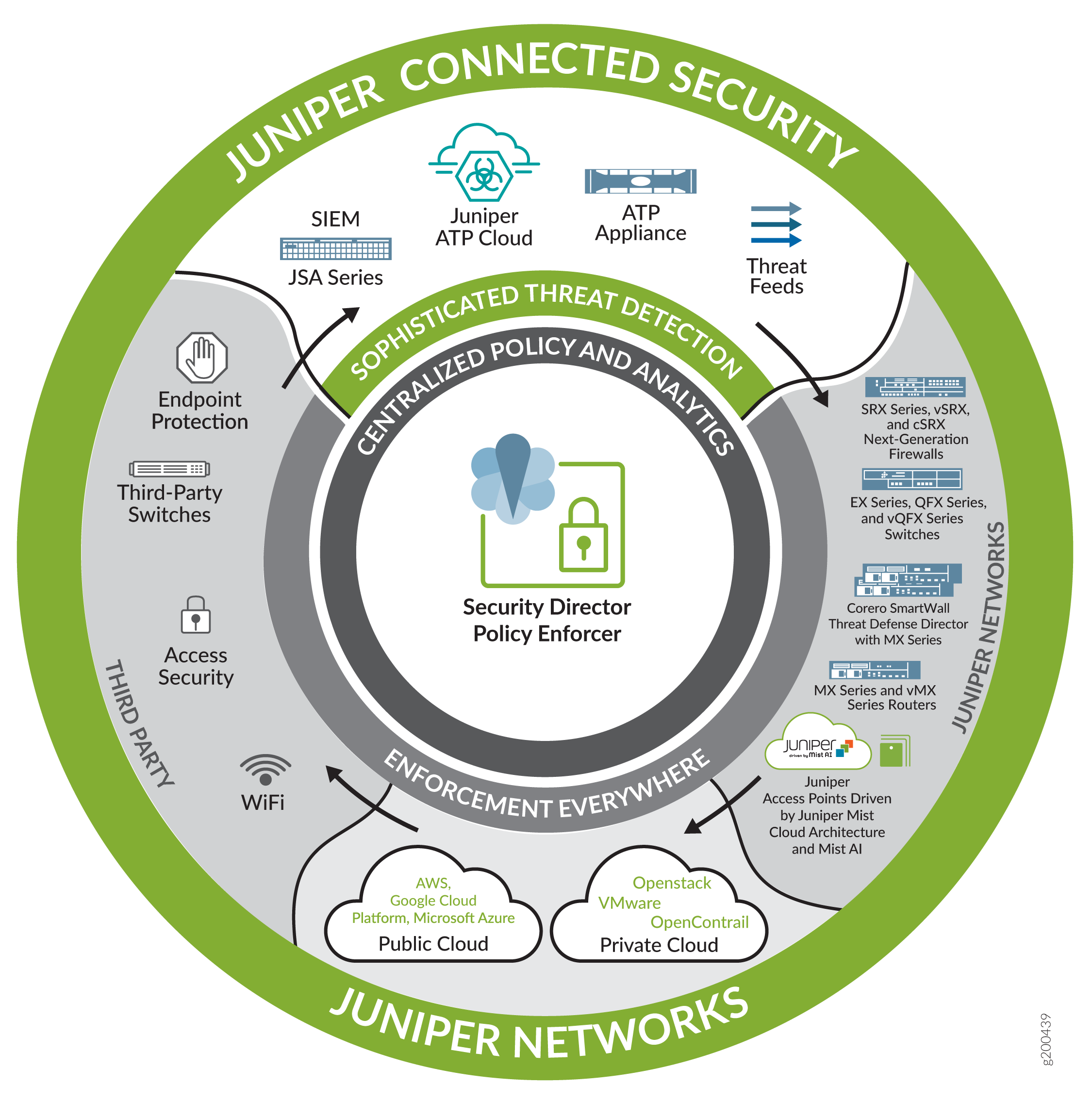
Data is constantly on the move, traveling across networks, between devices, and through various communication channels. As data in transit is particularly vulnerable to cyber threats such as interception, unauthorized access, and tampering, ensuring its protection is crucial for maintaining the confidentiality, integrity, and security of sensitive information.
Juniper Networks, in partnership with Mist Systems, offers a robust suite of products designed to protect data in transit across wireless, wired, and wide-area network (WAN) environments. This article explores how Juniper-Mist’s solutions, including Wireless, Wired, SD-WAN, Network Access Control (NAC), and other security products, work together to secure data in transit.
Juniper-Mist Wireless: Secure Connectivity for Mobile Data
Wireless networks are a critical component of modern IT infrastructure, enabling seamless mobility and connectivity. However, they also present unique security challenges. Juniper-Mist’s wireless solutions are designed to provide strong security for data in transit over Wi-Fi networks:
- WPA3 Encryption: Juniper-Mist wireless solutions support WPA3, the latest Wi-Fi security standard, ensuring that all data transmitted over the wireless network is encrypted and protected from eavesdropping and unauthorized access.
- AI-Driven Security: Mist’s AI-driven platform continuously monitors the wireless environment for threats, anomalies, and performance issues, enabling proactive security measures to protect data in transit.
- Secure Access Service: Juniper-Mist offers role-based access control and dynamic policies, ensuring that only authorized users and devices can access the network, thereby safeguarding sensitive data as it moves across the wireless infrastructure.
Juniper Wired: Protecting Data Across Physical Networks
While wired networks are generally considered more secure than wireless ones, they are not immune to threats. Juniper’s wired solutions provide robust security features to protect data in transit across physical network connections:
- MACsec Encryption: Juniper’s wired solutions support MACsec (Media Access Control Security), which encrypts data at the Layer 2 level, ensuring that any intercepted data remains unreadable without the correct decryption keys.
- Secure Segmentation: Juniper’s wired infrastructure allows for granular network segmentation, which isolates sensitive data and reduces the risk of unauthorized access and lateral movement by potential attackers.
- Advanced Threat Detection: Juniper’s wired solutions integrate with security tools like Juniper Advanced Threat Prevention (ATP) to detect and respond to threats in real-time, ensuring that data in transit remains secure.
Juniper SD-WAN: Secure and Reliable Wide-Area Networking
As organizations increasingly rely on distributed networks and cloud-based applications, securing data in transit across wide-area networks (WAN) becomes critical. Juniper’s SD-WAN solutions provide secure, high-performance connectivity for data in transit:
- IPsec VPN Encryption: Juniper SD-WAN solutions utilize IPsec VPN tunnels to encrypt data as it travels across public and private networks, ensuring that sensitive information is protected from interception and tampering.
- Zero Trust Security: Juniper SD-WAN implements Zero Trust principles, requiring continuous verification of users and devices before granting access to the network, thereby protecting data in transit from unauthorized access.
- Application-Aware Security: Juniper’s SD-WAN provides application-aware security, prioritizing and securing critical data flows to ensure that data in transit is not only secure but also delivered with optimal performance.
Network Access Control (NAC): Ensuring Secure Network Access
Juniper’s Network Access Control (NAC) solutions are integral to securing data in transit by managing and controlling access to the network:
- Endpoint Authentication: Juniper NAC ensures that only authorized and compliant devices can access the network, preventing unauthorized devices from transmitting or receiving data.
- Policy Enforcement: NAC enforces security policies based on the device’s role, location, and compliance status, ensuring that data in transit is handled according to the organization’s security requirements.
- Continuous Monitoring: Juniper NAC continuously monitors network traffic for suspicious behavior, allowing for real-time detection and mitigation of threats that could compromise data in transit.
Other Juniper Security Products: Enhancing Data Protection
Juniper Networks offers a range of additional security products that work in tandem with their wired, wireless, and SD-WAN solutions to provide comprehensive protection for data in transit:
- Juniper Advanced Threat Prevention (ATP): ATP provides real-time threat detection and prevention for data in transit, leveraging machine learning and threat intelligence to identify and block malicious activity.
- Juniper Secure Edge: Part of Juniper’s SASE (Secure Access Service Edge) architecture, Secure Edge protects data in transit by extending security controls to the network edge, ensuring that data remains secure as it moves between the cloud, on-premises environments, and remote users.
- Juniper Mist AI: Mist AI enhances security by providing visibility and insights into network traffic patterns, enabling proactive measures to protect data in transit from emerging threats.
Securing data in transit is a fundamental requirement for any organization aiming to protect its sensitive information from the ever-present threats in today’s digital world. Juniper Networks, in partnership with Mist Systems, offers a comprehensive suite of solutions that cover wireless, wired, SD-WAN, NAC, and other security needs. These solutions work together to provide robust encryption, access control, threat detection, and real-time monitoring, ensuring that data in transit remains secure at every stage of its journey. By deploying Juniper-Mist products, organizations can confidently protect their data, maintain compliance with regulatory standards, and ensure the integrity and security of their network operations.
Data Protection for Data in Transit with Sophos Network Products
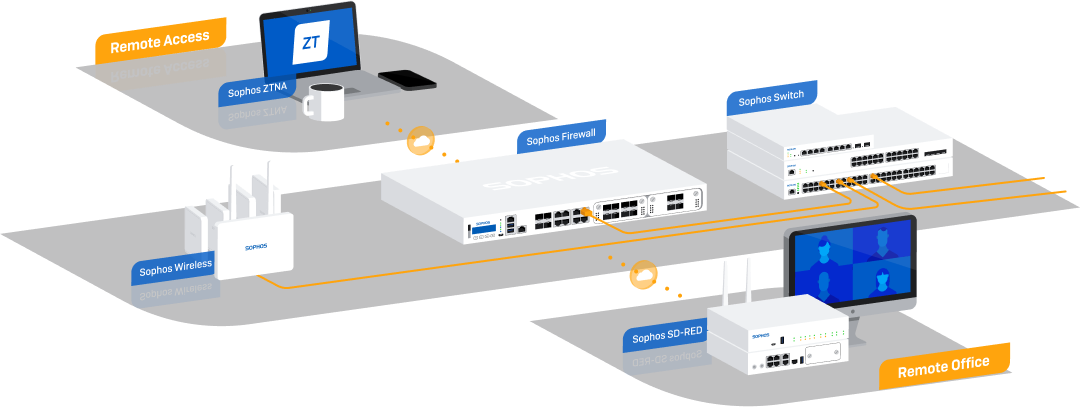
In an time where data is continuously exchanged across networks, devices, and cloud environments, ensuring the security of data in transit is paramount. Cyber threats targeting data as it moves from one point to another—whether across a corporate network, through wireless connections, or between cloud environments—can lead to significant breaches and data loss.
Sophos offers a robust suite of network security solutions, including the XGS Firewall, Zero Trust Network Access (ZTNA), cloud security, endpoint protection, switches, and wireless products, all designed to provide comprehensive protection for data in transit.
Sophos XGS Firewall: The Core of Network Security
At the heart of Sophos’ network security offerings is the XGS Firewall, which provides advanced protection for data in transit across your network.
-
Deep Packet Inspection (DPI): The XGS Firewall uses deep packet inspection to scrutinize every data packet traveling across the network, identifying and mitigating threats before they can compromise data in transit. This ensures that sensitive information is protected against a wide range of cyberattacks.
-
SSL/TLS Inspection: In today’s security landscape, much of the data in transit is encrypted. The XGS Firewall’s ability to perform SSL/TLS inspection allows it to decrypt, inspect, and re-encrypt traffic, ensuring that encrypted data is free from hidden threats without compromising its confidentiality.
-
Secure VPNs: The firewall supports secure VPN tunnels (IPsec and SSL VPNs), ensuring that data transmitted between remote users and the corporate network remains encrypted and secure, even when traversing public or less secure networks.
Sophos ZTNA: Zero Trust for Ultimate Data Security
Sophos’ Zero Trust Network Access (ZTNA) solution complements the XGS Firewall by ensuring that only authenticated users and devices can access network resources, thereby protecting data in transit:
-
Granular Access Control: ZTNA enforces strict access controls based on the principle of “never trust, always verify.” This means that even when data is in transit, access is granted only after continuous verification, significantly reducing the risk of unauthorized access.
-
Seamless Integration with Sophos Central: Sophos ZTNA integrates with the Sophos Central platform, providing a unified security framework that ensures consistent policies and protection across the entire network, whether data is in transit within a corporate environment or being accessed remotely.
Sophos Cloud Security: Protecting Data in Transit to and from the Cloud
As organizations increasingly rely on cloud services, securing data in transit to and from the cloud becomes critical. Sophos Cloud Security solutions offer:
-
Secure Cloud Gateways: Sophos Cloud Optix and other cloud security tools ensure that data moving between on-premises environments and the cloud is encrypted and protected from interception and unauthorized access.
-
Compliance and Visibility: Sophos cloud security solutions provide full visibility into data traffic between cloud environments, ensuring that data in transit is compliant with industry regulations and protected against potential breaches.
Sophos Endpoint Protection: Safeguarding Devices Handling Data
Sophos Endpoint Protection extends data in transit security to the devices that transmit and receive data:
-
Data Loss Prevention (DLP): Endpoint protection includes DLP capabilities that prevent sensitive data from being transmitted to unauthorized locations, ensuring that data in transit is handled according to security policies.
-
Intercept X: This endpoint protection solution uses advanced machine learning and behavioral analysis to detect and block threats targeting data in transit, ensuring that data exchanged between endpoints and the network remains secure.
Sophos Switches: Ensuring Secure Data Flow Across Networks
Sophos Switches provide the backbone for secure data transmission across wired networks:
-
VLAN Segmentation: Sophos Switches support VLAN segmentation, which isolates different types of traffic, ensuring that sensitive data in transit is restricted to secure network segments and protected from unauthorized access.
-
Network Monitoring and Control: Sophos Switches offer integrated network monitoring and control features, allowing administrators to track data flows, identify potential threats, and apply security policies that protect data in transit across the network.
Sophos Wireless: Secure and Reliable Wireless Data Transmission
Sophos Wireless solutions ensure that data in transit over Wi-Fi networks is protected from the unique threats posed by wireless environments:
-
WPA3 Encryption: Sophos Wireless supports WPA3, the latest Wi-Fi security standard, which provides strong encryption for data in transit over wireless networks, protecting it from interception and unauthorized access.
-
Rogue Access Point Detection: Sophos Wireless solutions can detect and mitigate rogue access points, ensuring that data in transit is not hijacked or intercepted by unauthorized wireless devices.
-
Synchronized Security: By integrating wireless security with other Sophos products through Sophos Central, organizations can achieve synchronized security across all network layers, ensuring consistent protection for data in transit.
Why Sophos is Essential for Protecting Data in Transit
Sophos offers a comprehensive and integrated approach to securing data in transit, ensuring that sensitive information remains protected as it moves across networks, devices, and cloud environments. By leveraging Sophos XGS Firewall, ZTNA, cloud security, endpoint protection, switches, and wireless solutions, organizations can:
-
Encrypt and Secure Data Across All Channels: Sophos ensures that data in transit is encrypted and secure, whether it’s moving through wired or wireless networks, across the cloud, or between endpoints.
-
Prevent Unauthorized Access: With ZTNA and granular access controls, Sophos enforces strict policies that prevent unauthorized access to data in transit, reducing the risk of data breaches.
-
Enhance Visibility and Control: Sophos provides centralized management and monitoring through Sophos Central, giving administrators full visibility and control over data flows, ensuring that security policies are consistently applied and that data in transit is protected at all times.
Sophos’ network security products provide a multi-layered defense strategy that secures data in transit at every stage, from the endpoint to the cloud, ensuring that organizations can confidently protect their sensitive information against the ever-evolving landscape of cyber threats.
Whalebone Immunity: Robust Data Protection for Data in Transit
Data is constantly being transmitted across networks, ensuring the security of data in transit is essential. Cyber threats such as phishing, malware, and man-in-the-middle attacks pose significant risks to sensitive information as it moves between users, devices, and applications.
Whalebone Immunity offers a powerful solution designed to protect data in transit by providing advanced DNS-based security that safeguards against these evolving threats. By leveraging real-time threat intelligence and comprehensive protection mechanisms, Whalebone Immunity ensures that your data remains secure and uncompromised as it traverses the internet, enabling your organization to maintain the highest levels of data integrity and security.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow do Juniper, Sophos, and Whalebone contribute to the protection of data in transit?
Juniper secures data in transit with its SRX Series Firewalls and SSL VPN solutions, which encrypt network traffic and ensure secure remote access, protecting data as it travels across the internet or between corporate networks.
Sophos offers Sophos XG Firewall and Sophos Central, which include features like VPN encryption and secure web gateway capabilities to encrypt and protect data in transit, preventing interception and ensuring secure communications.
Whalebone enhances DNS security by protecting DNS queries and responses with encryption and advanced filtering, ensuring that data in transit within the DNS layer is secure from threats like DNS hijacking and phishing.
How does Barracuda help protect data at rest?
Barracuda protects data at rest by offering encrypted backup and storage solutions that ensure sensitive data remains secure even if storage media are lost or stolen. Barracuda Backup encrypts data before it is written to disk and keeps it encrypted both on-premises and in the cloud, safeguarding against unauthorized access.
How does Barracuda help secure data in transit?
Barracuda secures data in transit through its email security and cloud security solutions, such as Barracuda Email Security Gateway and Barracuda CloudGen Firewall. These solutions encrypt email communications and secure network traffic, ensuring that sensitive information remains protected as it travels across the internet or internal networks.
How does Extreme Networks enhance the security of data in transit?
Extreme Networks enhances the security of data in transit with its comprehensive network security solutions, including secure wireless and wired network infrastructure. By employing advanced encryption protocols and secure network segmentation, Extreme Networks ensures that data moving through the network is protected from unauthorized access and eavesdropping.
How does OneSpan contribute to the security of data at rest?
OneSpan contributes to the security of data at rest by providing secure identity verification and digital signature solutions. These technologies ensure that only verified users can access and modify sensitive data, maintaining the integrity and confidentiality of stored information.
In what ways does Sophos enhance the protection of data at rest?
Sophos enhances the protection of data at rest through its encryption solutions, such as Sophos Device Encryption, which encrypts files and drives automatically. This ensures that sensitive data remains secure and unreadable even if it falls into the wrong hands, providing robust protection for stored data.
What role does One Identity play in securing data at rest?
One Identity secures data at rest by enforcing strict access controls and identity management. By ensuring that only authorized users have access to sensitive data, One Identity’s solutions help prevent unauthorized access and data breaches, thereby protecting stored information from internal and external threats.
What solutions does Cato Networks provide for protecting data in transit?
Cato Networks provides a secure, cloud-native network with built-in encryption for data in transit through its SASE (Secure Access Service Edge) platform. This solution ensures that all traffic between users, devices, and applications is encrypted, protecting sensitive data from interception and attacks while in transit.
Why is data protection for data at rest crucial for organizations?
Data protection for data at rest is crucial because it ensures that sensitive information stored on servers, databases, and devices is secure from unauthorized access, theft, and breaches. Encrypting data at-rest helps maintain confidentiality and compliance with regulations, reducing the risk of data exposure.
Why is protecting data in transit essential for maintaining cybersecurity?
Protecting data in transit is essential because data transmitted across networks is vulnerable to interception, tampering, and unauthorized access. Encrypting data in transit ensures that even if the data is intercepted, it cannot be read or altered, maintaining the confidentiality and integrity of the communication.
Contact us for a demo
Are you curious to learn whether our solutions can help you to fit the technological requirements of NIS 2? Contact us for a demo via the below button.
