Stronger Security
Reduces enterprise attack surface by automating and simplifying the process of granting privileged credentials resulting in a secured enterprise and new level of functionality for privileged users
Privileged Access Management empowers organizations to strengthen security, protect valuable assets, and simplify privileged access management in today's digital environment.

Privileged Access Management (PAM) replaces the need for manual password management and access control with seamless automation, stronger security and continuous oversight.
Still, too many companies rely on spreadsheets to keep track of passwords and attempt to govern privileged access manually. They count on the users to remember their passwords and adhere to access security policies. Needless to say, but these type of practices are inefficient and are impossible to scale.
As NIS2 directives will be communicated from the 18th of October in Belgium, Privileged Access Management will be required for many organizations. Users can no longer have administrator rights and access management need to organized differently.
One Identity Privileged Access Management (PAM) Essentials is a SaaS-based solution that prioritizes security, manageability and compliance via a native cloud environment. Therefore, you don’t need to install anything and can be considered as a straightforward and seamless deployment.
With this SaaS application, a user-centric experience is provided by making it easy for your team to embrace and utilize the PAM tools effectively.
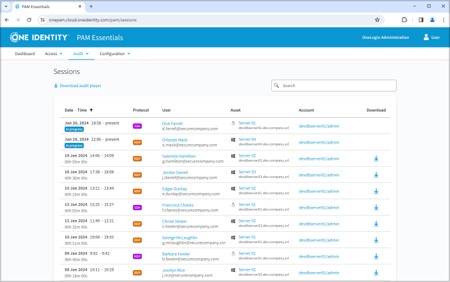
PAM Essentials provides privileged sessions and access controls which helps you to mitigate heightened risks associated with unauthorized users.
With One Identity Privileged Access Management Essentials, organizations can meet compliancy with industry-specific standards and meet the cyber insurance requirements, like NIS2.
Companies seeking a PAM solution that’s intuitive and user-friendly without compromising on functionality or security.
*For OneLogin customers, it is plug and play.
Organizations looking to optimize their security infrastructure without substantial additional expenses.
Companies aiming for quick deployment and adoption without a significant learning curve for administrators.
Enterprises interested in migrating to Software as a Service (SaaS) models for scalability, accessibility, and reduced infrastructure management.
User authentication is as well an important part in the NIS2 directives. Multi-factor Authentication (MFA) is a recommended use within the authentication process. Although, credentials can be comprised in the past. How to check credentials?
Workforce Identity Management provides an Advanced and Professional bundle which contains several applications. This One login authentication solution can be integrated with the One Identity PAM Essential solution, mentioned above.







Are you curious to learn whether Armis can help you with searching of assets in the network and how to protect these assets? Contact us for a demo via the below button.
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usPAM Essentials enhances visibility into privileged activities by:
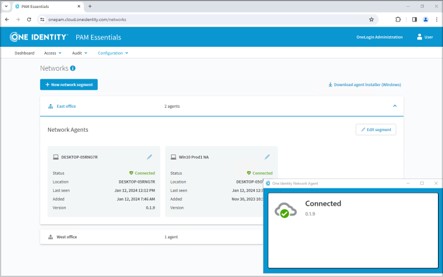
PAM Essentials secures privileged accounts by:
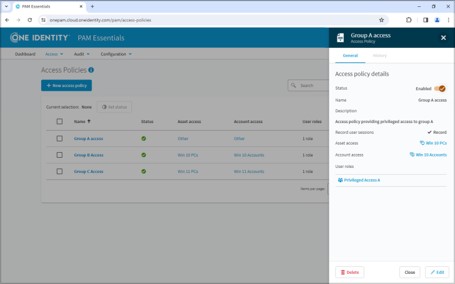
PAM Essentials helps organizations comply with the NIS 2 directives by:
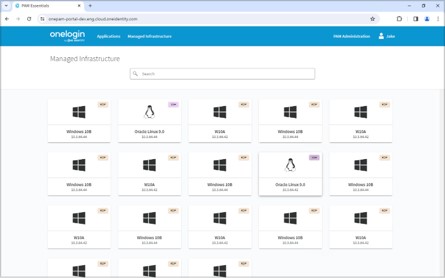
Key features of One Identity’s PAM Essentials include:
Privileged Access Management (PAM) Essentials from One Identity is a solution designed to secure, control, and monitor access to critical systems and sensitive information by privileged users. It helps organizations manage and audit the activities of users with elevated privileges to prevent unauthorized access and mitigate security risks.
PAM plays a crucial role in the overall security strategy of an organization by:
It is important for organizations to manage and monitor privileged access to prevent the misuse of elevated privileges, which can lead to significant security incidents. By controlling and auditing privileged access, organizations can detect and respond to suspicious activities, ensure compliance with regulations, and protect sensitive information from unauthorized access.
Privileged Access Management is critical for cybersecurity because privileged accounts have elevated access to critical systems and data. If compromised, these accounts can be exploited to cause significant harm, including data breaches, system disruptions, and unauthorized access to sensitive information. PAM mitigates these risks by securing and controlling privileged access.
Organizations should prioritize implementing PAM Essentials in light of the NIS2 directives because:
Are you curious to learn how Kappa Data can help you with Privileged Access Management solutions in your organization? Contact us for a demo via the below button.