Secure Access Service Edge (SASE)
SASE stands for Secure Access Service Edge. It is a network architecture model that integrates wide area networking (WAN) and network security services, such as secure web gateways (SWG), cloud access security brokers (CASB), firewalls as a service (FWaaS), and zero trust network access (ZTNA), into a single, cloud-delivered service model.
Watch "What is SASE" video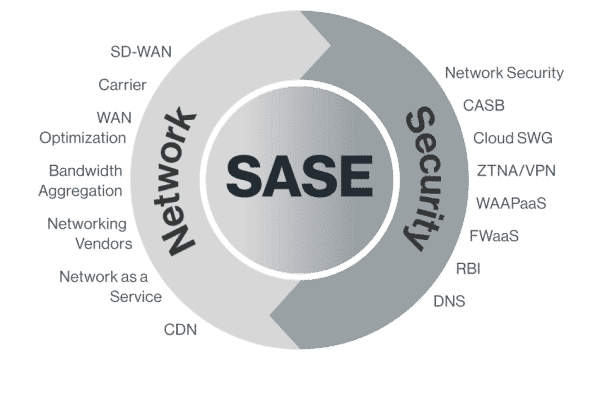
Global Distributed
A Cloud native backbone devided around 100 Points of Presence (POP), where each POP has the network and security infrastructure installed. The companies Local Area Network (LAN) can connect via a Socket or IP-sec towards the nearest POP in his region to access SaaS applications or other applications anywhere in the world. Also for enddevices, like laptops or mobile phones connect towards the nearest POP via a ZTNA client towards the same applications through the Cloud backbone of Cato Networks
Global Security
Security is organized in the same way as the network part. Every security software is as well installed at the POP and access by the endpoint.
At Cato Networks Extensive measures are taken to ensure the security of Cato Cloud. All communications — whether between PoPs or with Cato Sockets or Cato Clients — are secured by AES-256 encrypted tunnels. To minimize the attack surface, only authorized sites and mobile users can connect and send traffic to the backbone. The external IP addresses of the PoPs are protected with specific anti-DDoS measures. Cato service is ISO 27001 certified.
Highly scalable
Because the network & security is both installed at every POP, scalability is one of the top reasons to look at solutions like Cato Networks.
Imagine you need to upgrade the bandwith capacity of the line for a site in Amsterdam from 100Mbps to 200 Mbps. With only activating a new license you get more bandwith! What if you can get a license where you can have the control over the bandwith of multiple sites?
Secure Access Security Edge by Gartner
Gartner is a global research and advisory leader in the technology space dedicated to helping businesses make critical IT decisions. Its Magic Quadrants (MQs) drive many organizations’ acquisition processes as they provide a clear and unbiased evaluation of the relative advantages and disadvantages of various technology solutions.
However, Gartner does not only perform evaluations of existing technology – it also looks to the future and provides organizations with guidance on how to build and secure the networks of the future. Back in 2019, Gartner finally created a name for what Cato Networks had already been doing for 4 years – SASE (Secure Access Service Edge).
Today, SASE has become a priority as many organizations look to adopt what Gartner calls “the future of network security”. Gartner’s recently released Single-Vendor SASE Magic Quadrant provides strong guidance on critical capabilities and vendors to help organizations maximize the value of their SASE investment throughout their journey.
The Components of SASE Architecture
Single-Vendor SASE, according to Gartner, is defined as the global delivery of converged networking and security-as-a-service capabilities such as: SD-WAN, SWG, CASB, FWaaS and ZTNA by a single vendor, supporting all edges (not just branch networks or mobile users). The standard capabilities of a Single-Vendor SASE include:
- Secure Web Access: Protection for users and locations against malware, phishing, policy violations and other threats, regardless of location.
- In-Line SaaS Access Controls: Granular controls based on activity type (upload, download, login, etc.) or risk level for cloud applications.
- Identity, Context and Policy Based Remote Access: Provides access for users or locations based on least-privilege principles with ongoing evaluation on a case-by-case basis.
- An Appliance That Supports Application-Aware Dynamic Traffic Steering: SD-WAN, providing resiliency and optimized routing overs multiple last-mile ISP connections.
- Firewall as a Service (FWaaS): A firewall is the foundation of any network security stack. SASE includes FWaaS to provide strong protection with minimal overhead and management.
Optional security capabilities include:
- Remote Browser Isolation: Delivers additional security to users by allowing them to access unknown Internet resources in an isolated environment.
- Zero-Day & Polymorphic Malware Protection: Evaluates unknown files to make a verdict on malicious intent.
- DNS Protection: Protection from known threats by sink holing queries that refer to malicious destinations.
- API-based Inspection for Cloud Applications: Known as API-based CASB, this service integrates with common cloud applications to scan for malware, data leakage and unintended over-sharing of data.
Optional networking capabilities include:
- Global Private Backbone: A global private backbone overcomes the unpredictability of the public Internet, by leveraging reliable, consistent transport that favors performance over cost savings.
- Enhanced Internet: Network optimization capabilities such as TCP proxy and QoS that improve and ensure performance for critical applications.
Gartner also defines the term “SASE alternatives” to describe solutions that check the boxes of SASE features without achieving the full convergence required by SASE. These solutions – often called “dual-vendor” or multivendor SASE – link point security products via APIs and service chaining. While these may have the same capabilities as SASE, they have poorer performance and are more difficult to manage than a true SASE solution.
Gartner’s SASE Guidance Report
Since defining the term SASE in 2019, Gartner has included a SASE category in its Hype Cycle for Enterprise Networking report. Both years, Gartner listed Cato as a “Sample Vendor” in the space, recognizing that Cato SASE Cloud meets the criteria for a true SASE solution.
In addition to its Hype Cycle reports, Gartner has published a number of reports further defining the space and providing guidance to organizations looking to adopt SASE. The SASE Convergence Roadmap 2021 and Market Guide for Single-Vendor SASE 2022 outline the steps that organizations should take when adopting SASE, including short-term and long-term goals for making the transition as well as recommendations for selecting a SASE vendor.
Finally, Gartner launched the first-ever single-vendor SASE Magic Quadrant, positioning Cato among the top vendors in the space.
Difference between SASE and SSE
In 2021, Gartner introduced SSE, which focuses more on security capabilities and less on network connectivity and infrastructure. SSE is like SASE but doesn’t include SD-WAN capabilities. This favors traditional ZTNA, CASB and SWG providers with strong cloud brokering options that don’t come from networking backgrounds.
A strong group of current SSE offerings originated in CASB, ZTNA and SWG products. In some cases, some providers have acquired or expanded into SD-WAN, which could lead to a transition from SSE to SASE in some cases.
The core aspects of SSE include ZTNA, SWG, CASB and network traffic control, also known as firewall as a service (FWaaS).
Zero-trust network access
ZTNA focuses primarily on how end users access cloud and online services and data. It involves policies applied to evaluate who is accessing resources, from what system and whether any behavioral aspects of access are suspicious or malicious.
Key elements of ZTNA include the following:
- Strong authentication and authorization of endpoint systems and user accounts.
- Adaptive access policies that evaluate group membership and privileges, access behaviors and known malicious or suspicious indicators.
- Browser isolation and sandboxing to prevent malware infection and other browser-based threats.
Secure web gateway
SWG functionality includes content filtering and URL-based access controls, as well as some DNS monitoring and browser security controls. Most SWG platforms include content monitoring and data loss prevention policy tools as well. Leading options also offer remote browser isolation tools and capabilities that fortify web browsers with a sandbox designed to protect users when visiting designated sites.
Cloud access security broker
A CASB probes deeply into cloud services — primarily SaaS but also applications and services in PaaS and IaaS environments — to examine API calls and behaviors for unusual activity.
Many cloud applications are complex web services with vast arrays of API calls. CASB services permit a much deeper analysis of specific interactions within the context of a single cloud application.
Network traffic control
Another capability some vendors tout is network traffic control, or FWaaS. FWaaS replaces traditional next-gen firewall controls with a cloud-based model.
SSE can be a valuable feature here to control things such as remote access protocols — for example, SSH and Remote Desktop Protocol — and other malicious nonweb traffic.
SASE vs. SSE: Use SASE for comprehensive coverage
When examining SASE vs. SSE, consider SSE a subset of SASE — encompassing most of the same security control capabilities other than network bandwidth control and WAN optimization.
SASE is a more appropriate brokering option for enterprises that need comprehensive cloud-based connectivity and a security policies application that covers both end users and entire locations moving away from a hub-and-spoke model of network connectivity. For remote users, SSE offers the same security options without layering on SD-WAN and SDN network traffic management options that are largely superfluous.
Most organizations today need what SSE provides: a suite of controls that can shield a remote workforce from malicious activities through the deployment of a zero-trust model governing access control and monitoring, browser and cloud services security, and data protection. Many providers offer both SASE and SSE, with SSE available through a licensing model that enables an organization to upgrade to SASE if appropriate.
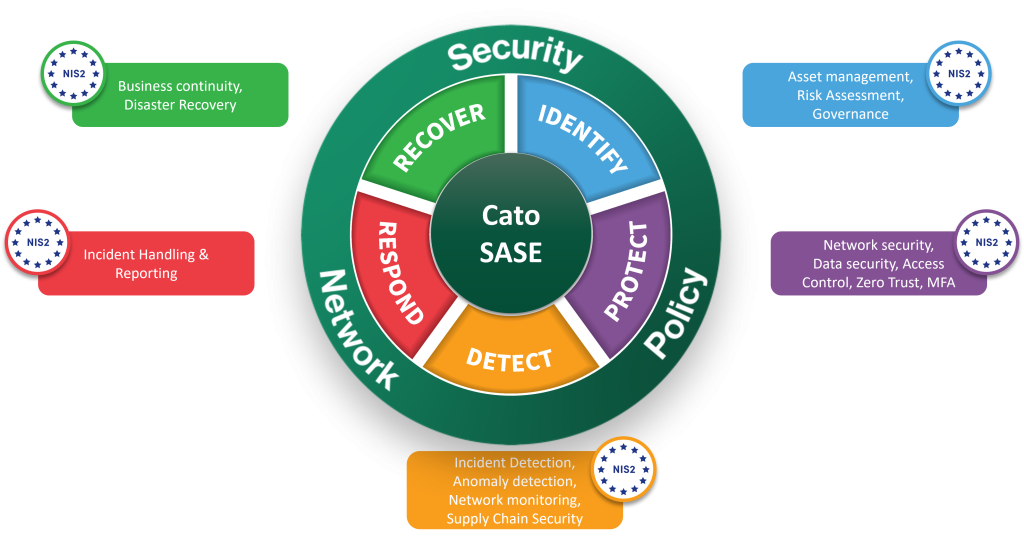
NIS2 compliancy with Cato Networks
NIS2 law publication is coming on the 18th of October in 2024 and organisations are looking to solutions that can help them to fill in the IT requirements within each law that will be communicated.
In this chapter we will explain how Cato Networks with his SASE solution fills in all the gaps within the NIS2 directives.
“Organizations subject to NIS 2 will be obligated to take appropriate and proportionate technical, operational and organizational measures to manage the risks posed to the security of network and information systems which those entities use for their operations or for the provision of their services, and to prevent or minimize the impact of incidents on recipients of their services and on other services.”*
*Courtesy of Armis
NIS2 does not make your life easy

Key obligations :
- Preamble (83) – Outsourcing
- Full accountability of risk-management measures regardless of network and information systems ownership
- Preamble (125) – Competence of Supervisors (for Member States)
- Trained professionals for on-site supervision (including identification of weaknesses in DB, FW, encryption and networks)
- Article 20 – Governance
- Management bodies of essential and important entities must approve the cybersecurity risk-management measures taken by those entities as per art.21 (see later)
- Management bodies are required to follow training, and shall encourage similar training to their employees on a regular basis
- Article 21 – Cybersecurity Risk Management
- Technical, operational and organisational measures to manage the risks posed to the security of network and information system, and to prevent or minimise the impact of incidents on recipients of their services and on other services.
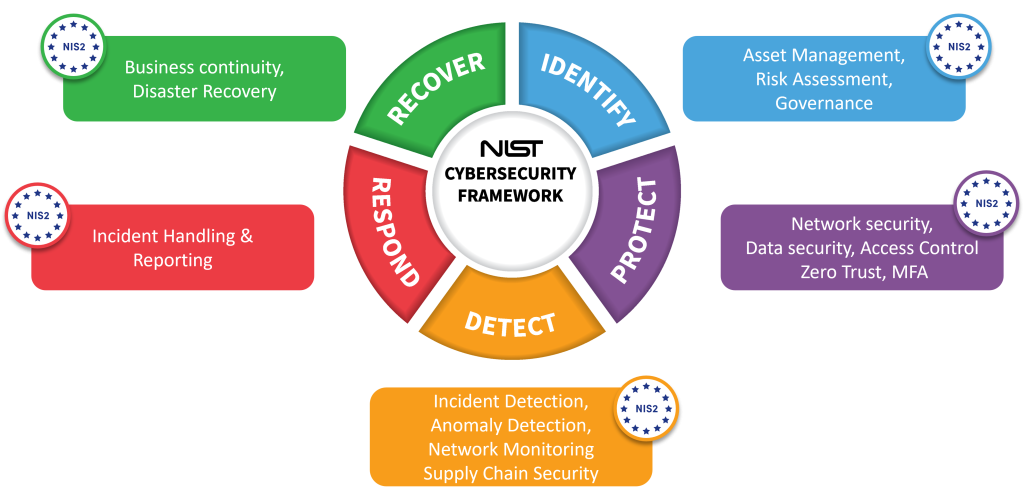
Gaps to NIS2 compliance
Mapping NIS2 directives with Cato SASE Cloud
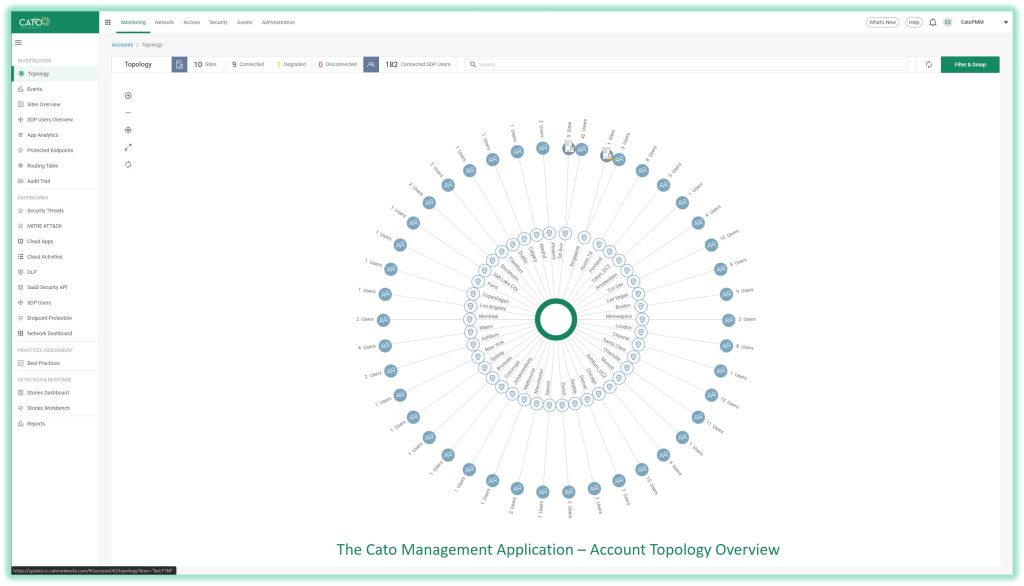
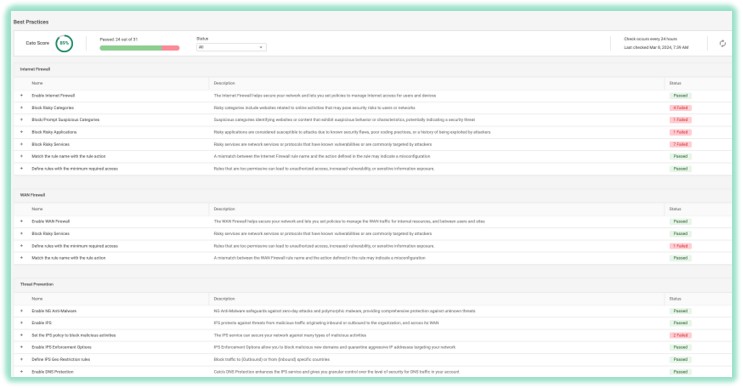
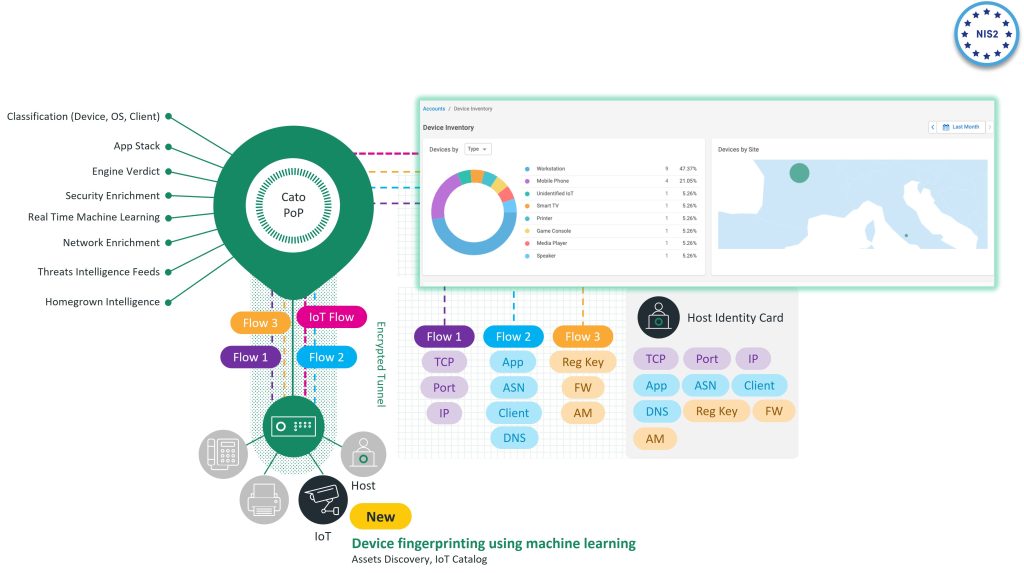
Identify : Asset Management with Cato
Cato Single Shared Context – Complete Asset Visibility of the IT landscape
The first requirement is around Asset management and visibility.
Thanks to the Single Pass Software stack, Cato is able ingest all flows with hundreds of different attributes to allow the platform to provide full visibility of the digital assets inside the organization.
Our platform essentially creates an identity card for hosts, users, IOT and OT devices anything that connect to our cloud.
The automated device inventory dashboard list all discovered devices based on passively scanning the flows that enter our POP locations.
Identify : Risk Assessment with Cato
Protect : Network Security
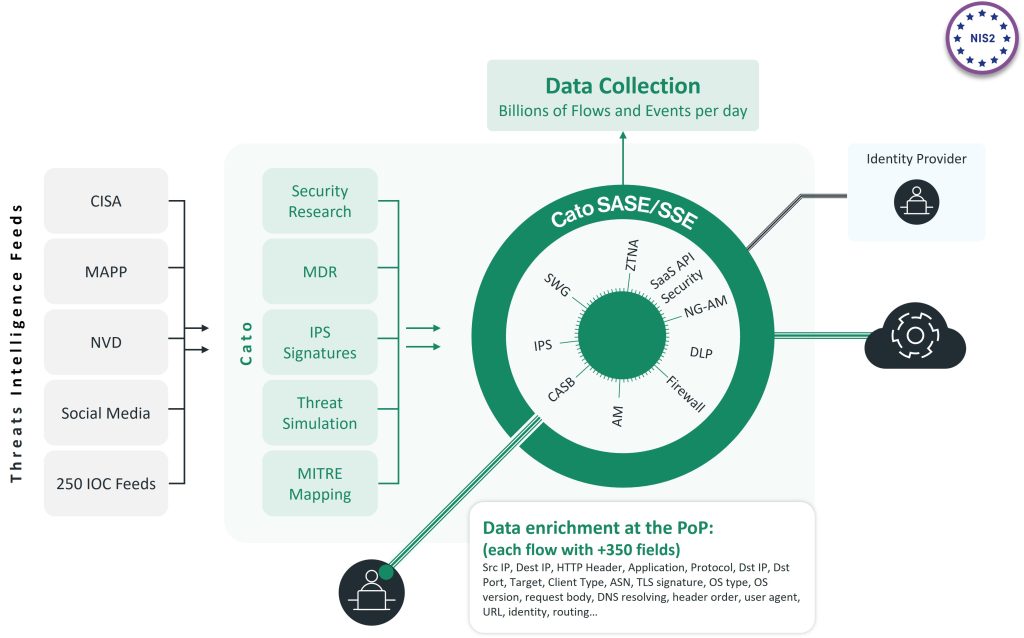
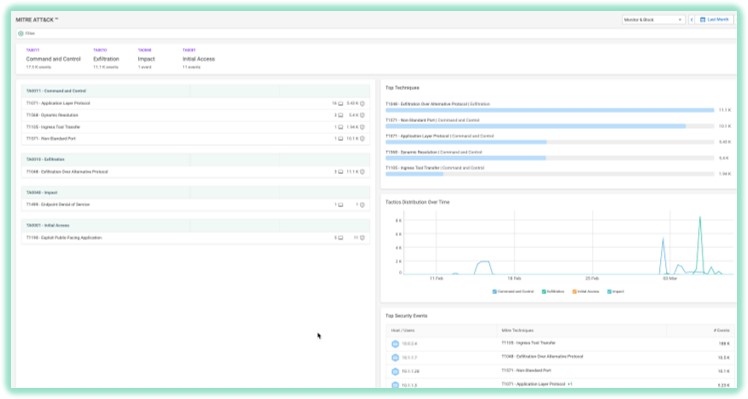
When it comes to network security, the notion of a single context, a single path architecture is something that makes Cato Networks very unique.
Think about all the intelligence Cato Networks is putting into the system.. All the research that Cato Networks is doing on everything, every flow that passes through the system from any devices, any users or any sites or applications will be enriched at the source.
Whenever it reached the pop, Cato Networks is enriching the context it with hundreds of fields around the user, the application, the environment, the location and so it provides you a global context
So in real time, the context is being shared between all Cato Networks security stacks and it allows Cato Networks to develop faster.
Cato Networks doesn’t need to write everything from scratch, at the end it’s the same engine working on the same flow at the same time.
So the shared context is the difference between how Cato Cloud is protecting the data of their customers versus others vendors which are doing service chaining or purchase different companies.
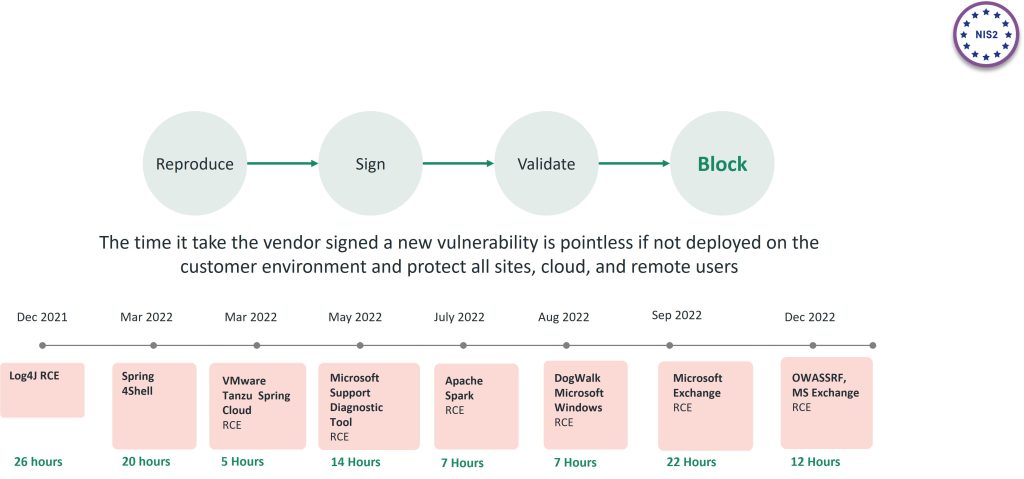
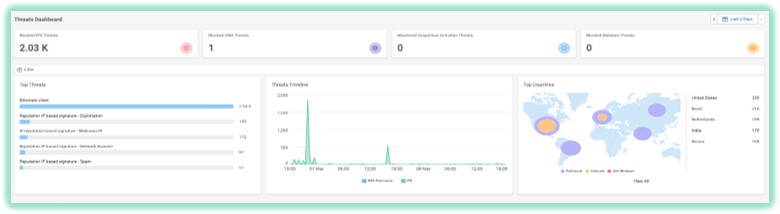
Another unique approach in Cato is to provide an accurate and fast response to vulnerabilities. When a new vulnerability is discovered Cato reproduces it, create a signature for it, validate it and moving it to block automatically.
Cato Networks is not sending it to the customer to use it and to configure themselves. They are just notified about it.
Here are the facts, if you look at the last year most known vulnerabilities, it took Cato Networks a few hours to develop a signature and apply it in prevent mode to all of their POP locations, therefore protecting immediately all of our customers.
Cato is not just developing a signature, but also testing it in a controlled environment and automatically implementing in all their POP’s in prevent mode. Cato makes sure that even after deploying it, they are monitoring the behavior of their customers environment to ensure no disruption is introduced
And that’s what Cato is calling “IPS as a Service”
************************
952 distinct signatures triggered our IPS globally since Jan 1st 2022
Feb. 2021: VMWare VCenter RCE Cato response time: 48 hours
Mar. 2021: MS Exchange SSRF Cato response time: 3 days
Mar. 2021: F5 Vulnerability Cato response time: 2 days
May 2021: vSphere Client (HTML5) Remote Code Execution Cato response time: 6 days.
Jul 2021: PrintNightmare Spooler RCE Vulnerability Cato response time: 3 days
August 2021: VMware vCenter RCE Cato response time: 24 hours
September 2021 Microsoft Exchange Autodiscover Credentials Leak. Cato response time: 24 hours
November 2021: Protect against urgent exploits identified by CISA – on time
Dec 2021: Log4J RCE (CVE-2021-44228). Cato response time: 26 hours
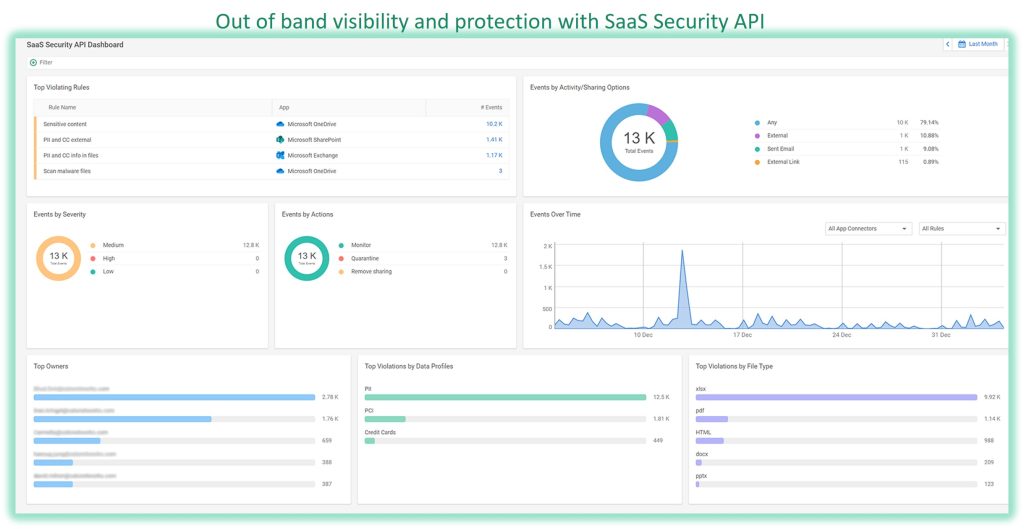
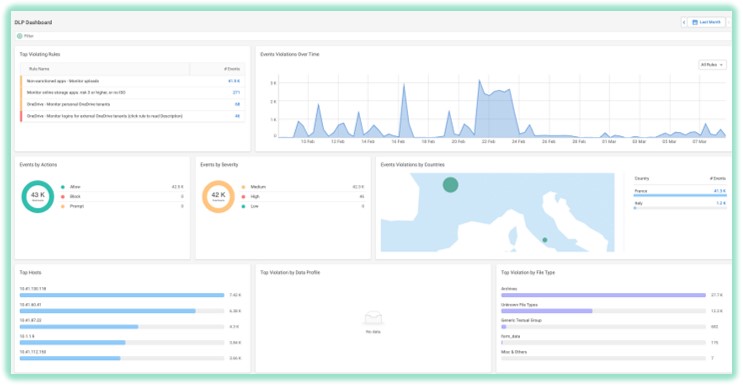
Protect : Data Security
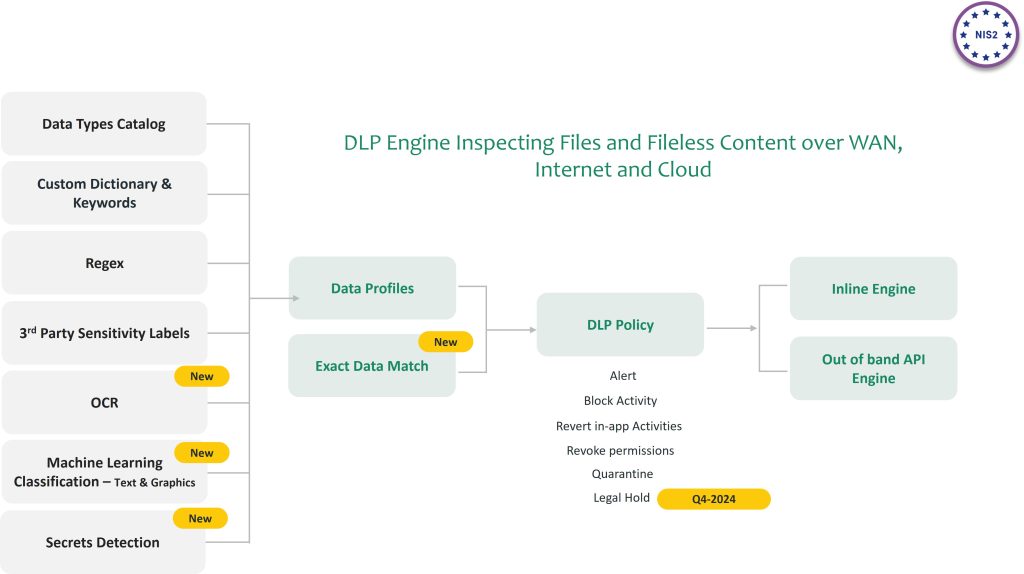
NIS 2 calls for data security protection as well. Cato Networks continue to improve their CASB and DLP solutions to be best-in-class with more ways to define data types, use ML-based classifiers model, OCR and EDM techniques and integrations with 3rd party services.

Another unique approach in Cato is to provide an accurate and fast response to vulnerabilities. When a new vulnerability is discovered Cato reproduces it, create a signature for it, validate it and moving it to block automatically.
Cato Networks is not sending it to the customer to use it and to configure themselves. They are just notified about it.
Here are the facts, if you look at the last year most known vulnerabilities, it took Cato Networks a few hours to develop a signature and apply it in prevent mode to all of their POP locations, therefore protecting immediately all of our customers.
Cato is not just developing a signature, but also testing it in a controlled environment and automatically implementing in all their POP’s in prevent mode. Cato makes sure that even after deploying it, they are monitoring the behavior of their customers environment to ensure no disruption is introduced
And that’s what Cato is calling “IPS as a Service”
************************
952 distinct signatures triggered our IPS globally since Jan 1st 2022
Feb. 2021: VMWare VCenter RCE Cato response time: 48 hours
Mar. 2021: MS Exchange SSRF Cato response time: 3 days
Mar. 2021: F5 Vulnerability Cato response time: 2 days
May 2021: vSphere Client (HTML5) Remote Code Execution Cato response time: 6 days.
Jul 2021: PrintNightmare Spooler RCE Vulnerability Cato response time: 3 days
August 2021: VMware vCenter RCE Cato response time: 24 hours
September 2021 Microsoft Exchange Autodiscover Credentials Leak. Cato response time: 24 hours
November 2021: Protect against urgent exploits identified by CISA – on time
Dec 2021: Log4J RCE (CVE-2021-44228). Cato response time: 26 hours
Protect : Access Control Zero Trust
Consistent Policy for Users Everywhere
- Identity driven
- Global coverage
ZTNA: Trust but Verify
- Access control with device posture checks
- User Confidence Level with MFA
- Threat prevention (FWaaS, SWG, IPS, AM)
- Sensitive data protection (DLP)
- Risk-based applications access control (CASB)
Another unique approach in Cato is to provide an accurate and fast response to vulnerabilities. When a new vulnerability is discovered Cato reproduces it, create a signature for it, validate it and moving it to block automatically.
Cato Networks is not sending it to the customer to use it and to configure themselves. They are just notified about it.
Here are the facts, if you look at the last year most known vulnerabilities, it took Cato Networks a few hours to develop a signature and apply it in prevent mode to all of their POP locations, therefore protecting immediately all of our customers.
Cato is not just developing a signature, but also testing it in a controlled environment and automatically implementing in all their POP’s in prevent mode. Cato makes sure that even after deploying it, they are monitoring the behavior of their customers environment to ensure no disruption is introduced
And that’s what Cato is calling “IPS as a Service”
************************
952 distinct signatures triggered our IPS globally since Jan 1st 2022
Feb. 2021: VMWare VCenter RCE Cato response time: 48 hours
Mar. 2021: MS Exchange SSRF Cato response time: 3 days
Mar. 2021: F5 Vulnerability Cato response time: 2 days
May 2021: vSphere Client (HTML5) Remote Code Execution Cato response time: 6 days.
Jul 2021: PrintNightmare Spooler RCE Vulnerability Cato response time: 3 days
August 2021: VMware vCenter RCE Cato response time: 24 hours
September 2021 Microsoft Exchange Autodiscover Credentials Leak. Cato response time: 24 hours
November 2021: Protect against urgent exploits identified by CISA – on time
Dec 2021: Log4J RCE (CVE-2021-44228). Cato response time: 26 hours

Detect: Supply Chain Security
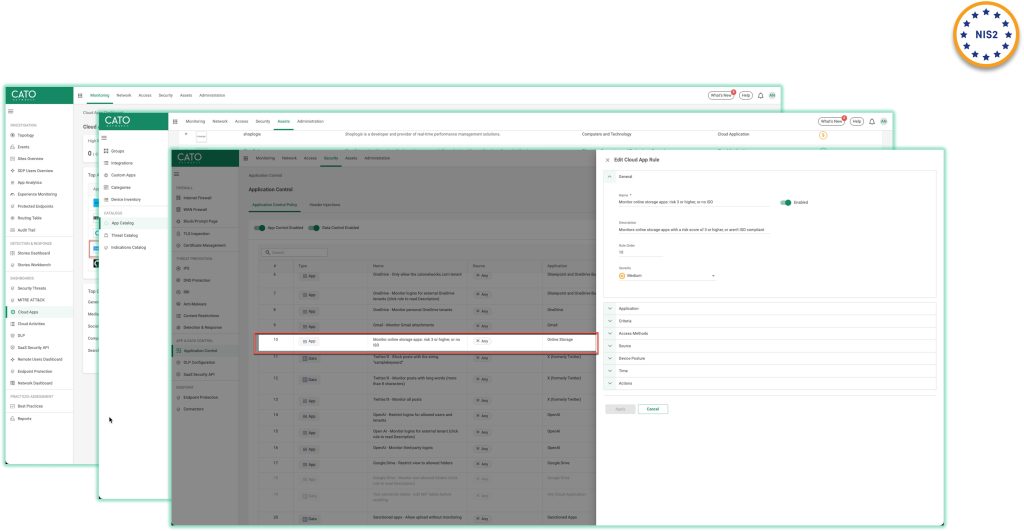
Another big area of focus in NIS 2 is Supply Chain Security. Organizations are responsible for implementing appropriate technical, operational, and organizational measures to ensure the security of their supply chain.
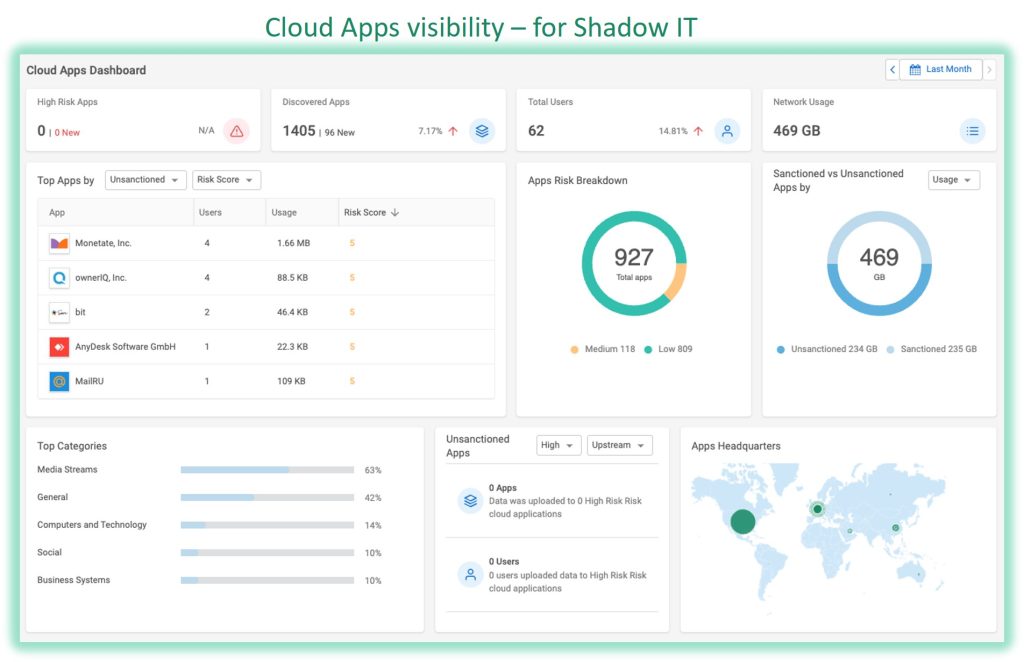
The Cato SASE Cloud helps in identifying security risks in the supply chain, especially for services deployed via the cloud, by evaluating the security posture of ALL of the Cloud applications utilised by the users.
Using the Cato SASE cloud app dashboard administrators can quickly spot unsanctioned applications
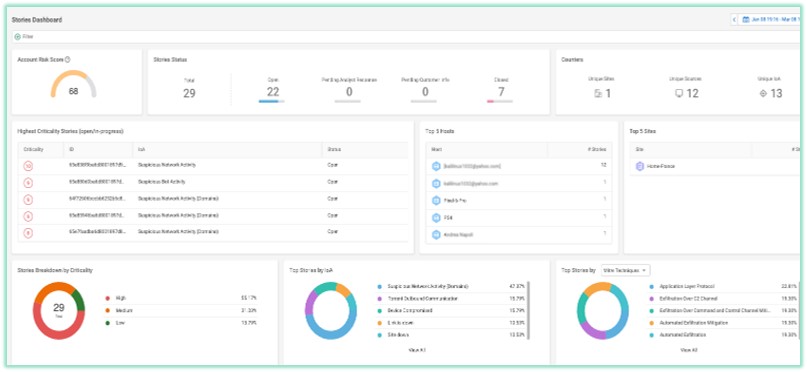
Response: Incident Response and Reporting
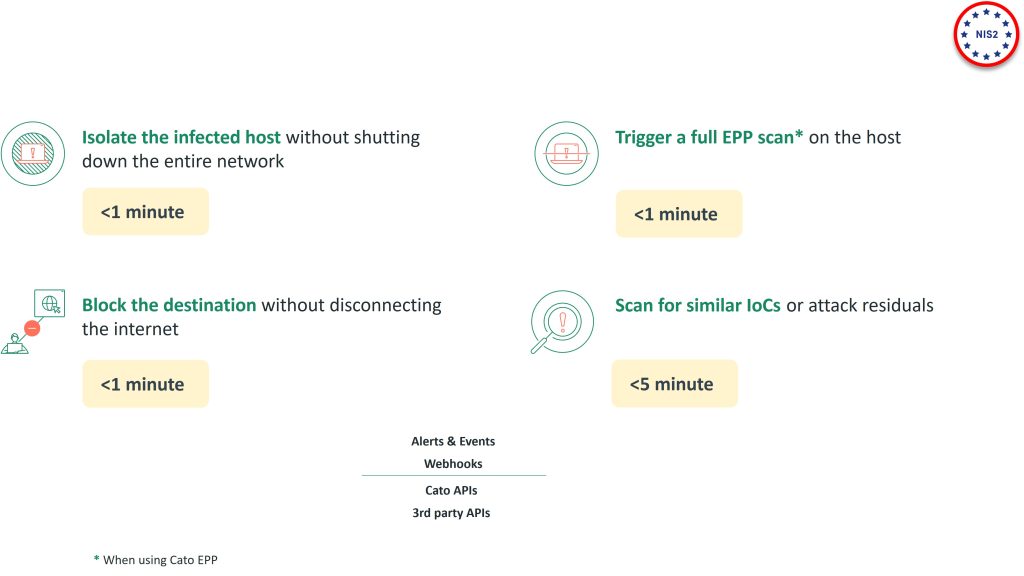
Once an incident is detected, how fast are you able to remediate, and report? this is another key requirement of NIS 2.
Cato XDR enables smooth collaboration between the SOC and the NOC teams to effectively remediate networks and security incidents, via Cato’s unified management console, which consolidates wide variety of engines for mitigation and remediation. No integration needed, all under the same UI.
- upon an incident detection you can maintain business continuity by isolating an infected host or block the malicious destination in less than a minute without shutting down the entire network using a firewall policy to bock the host’s outbound traffic
- Using the Cato Endpoint Protection you can Trigger an EPP to scan all of your endpoits directly from the management console
- or search for similar IoCs again without leaving the UI
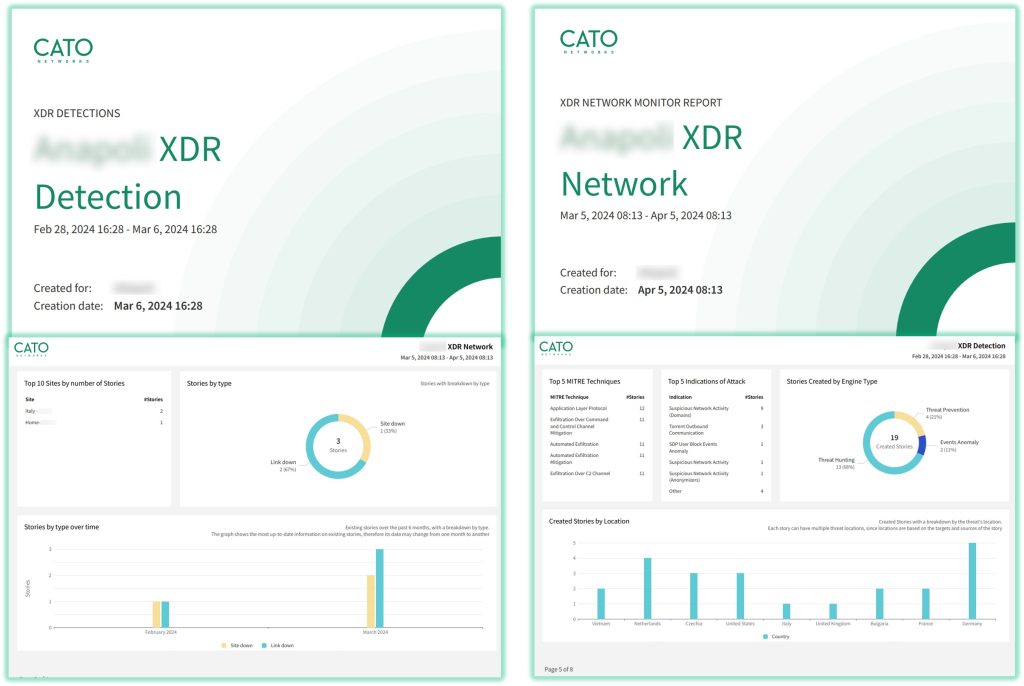
- you can quickly generate Scheduled or on demand Detection and Network reports with a couple of clicks
with Cato’s XDR you have fast path to detection remediation and reporting to meet your NIS 2 obligations in this area
Recover: Business Contuity and Disaster Recovery
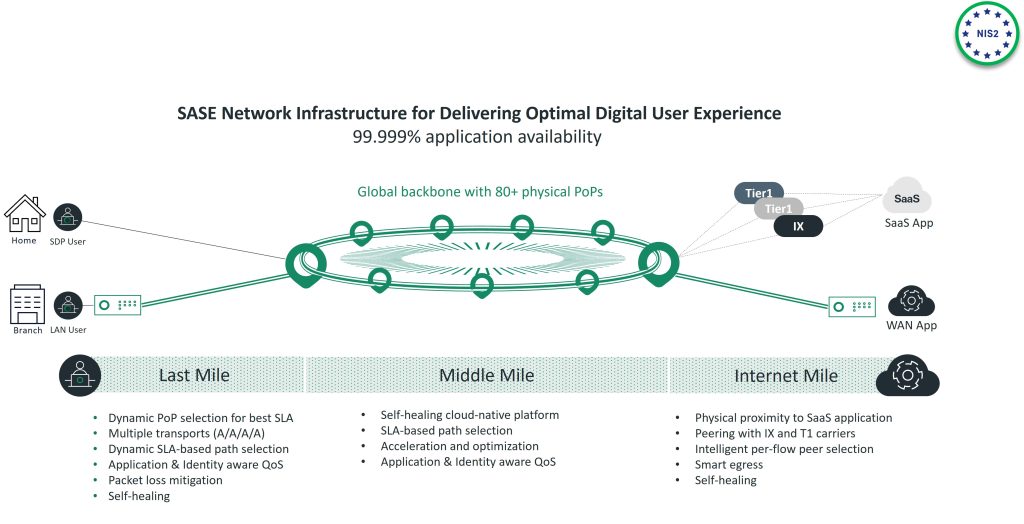
Business Contintuity and Disaster Recovery procedures for organizations delivering ciritcal services are of outmost importance and this is a key requirement for NIS 2.
As you have seen, Cato SASE Cloud is a cloud service that converges networking and security capabilities. A set of architectural design choices makes the Cato SASE Cloud highly available while reducing the need for IT to create a detailed HA design
In essence, Cato delivers HA-as-a-Service and this is why are are able to offer 5 nines application availability SLA
***********************************
- The creation of a single, processing-software engine for routing, optimizing and securing all WAN and Internet traffic.
- The distribution of the processing engine across a cloud-scale, global network points of presence (PoPs)
- The avoidance of a single controller for the processing engines, but rather the creation of a smart distributed data plane at the processing engine level
- The minimization of business logic at the edge to simplify edge HA design
Frequently asked questions
Discover our questions and answers regarding SASE of Cato Networks and the NIS2 directives. Don't hesitate to contact us, when you have other questions.
Contact us for a demo
Are you curious to learn how Cato Networks can help you in to simplify the connectivity and security between several entities and be compliant with NIS2? Contact us for a demo via the below button.