Cloud Security
Many companies use different types of cloud environments for their assets and applications. With this article, we inform you regarding Cloud Security solutions wchich make this assets visible in one central portal and are scanned for threat detection.

Cloud Security with Sophos Cloud Optix
With Sophos Cloud Security posture management you can more easily identify cloud resource vulnerabilities, ensure compliance, and respond to threats faster.
Cloud Security and Cost Optimization Features
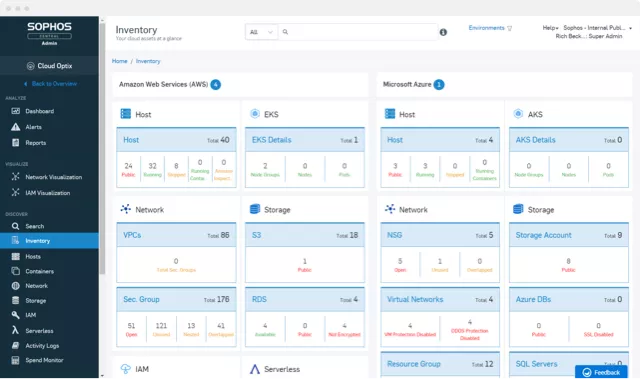
Multi-Cloud Visibility
View inventories and visualizations for AWS, Azure, Google Cloud, and Kubernetes. Continually analyze for security risks, over-privileged access, and spend anomalies.
Fix Security Gaps Fast
Get automatically identify and risk-profile security and compliance risks, with contextual alerts grouping affected resources, detailed remediation steps, and guided response.
Optimize Cloud Costs
Track cloud services side by side on a single screen for improved visibility, receive independent recommendations to reduce spend, and identify indicators of compromise.
Stay Compliant
Automate compliance assessments, save weeks of effort mapping Control IDs from overarching compliance tools to Cloud Optix, and produce audit-ready reports instantly.
Secure Devops
Block vulnerabilities pre-deployment. Seamlessly integrate Sophos security and compliance checks at any stage of the development pipeline to scan container images and IaC templates.
Integrate Seamlessly
Access Cloud Optix features programmatically via a REST API and integrate seamlessly with third-party services, such as SIEM and DevOps tools, to streamline security operations.
Multi-Cloud Visibility
Cloud Optix simplifies tracking assets and network traffic across AWS, Azure, and Google Cloud. It offers clear inventories and on-demand topology maps for multi-cloud environments in one dashboard. This tool continuously checks for security issues, excessive access privileges, and spending irregularities.
Respond to Cloud Security Threats Faster
Cloud Optix simplifies tracking assets and network traffic across AWS, Azure, and Google Cloud. It offers clear inventories and on-demand topology maps for multi-cloud environments in one dashboard. This tool continuously checks for security issues, excessive access privileges, and spending irregularities.
Manage Identities Before They’re Exploited
Cloud Optix analyzes complex, interwoven Identity and Access Management (IAM) roles to visualize relationships, making it simpler to manage access privileges for user, group, and cloud service roles. offering guidance on where to make IAM policy updates with the cloud provider before over-privileged IAM access is exploited.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
How does Sophos Cloud Security help organizations meet the NIS2 directive’s requirements for continuous monitoring?
Sophos Cloud Security helps organizations meet the NIS2 directive’s requirements for continuous monitoring by providing real-time visibility into cloud activities and automated threat detection. Sophos Cloud Optix, for example, continuously scans for vulnerabilities, compliance issues, and suspicious behaviors, allowing organizations to detect and respond to potential threats quickly.
How does Sophos Cloud Security help protect data in cloud environments as required by the NIS2 directive?
Sophos Cloud Security helps protect data in cloud environments by offering encryption, access controls, and data loss prevention (DLP) features that secure sensitive information both at rest and in transit. These protections ensure that data is safeguarded against unauthorized access and breaches, aligning with the NIS2 directive’s requirements for data protection and confidentiality.
How does Sophos Cloud Security integrate threat detection and response to enhance cybersecurity?
Sophos Cloud Security integrates threat detection and response through its advanced analytics and machine learning capabilities, which identify and respond to threats in real-time. By correlating data from various cloud services and deploying automated responses, Sophos Cloud Security minimizes the time to detect and mitigate threats, enhancing overall cybersecurity in line with NIS2 requirements.
What is Sophos Cloud Security, and why is it important for organizations?
Sophos Cloud Security is a comprehensive suite of security solutions designed to protect cloud environments, including infrastructure, applications, and data, from cyber threats. It is important for organizations because it ensures that their cloud assets are secure from breaches, mis-configurations, and other vulnerabilities, which is crucial as more businesses migrate critical workloads to the cloud.
What role does compliance monitoring in Sophos Cloud Security play in aligning with NIS2 directives?
Compliance monitoring in Sophos Cloud Security plays a crucial role in aligning with NIS2 directives by continuously assessing cloud environments against regulatory requirements and security best practices. It provides automated compliance checks, reporting, and alerts, ensuring that organizations can demonstrate adherence to NIS2 mandates and take corrective actions as needed.
Why is automated security important for cloud environments, particularly under the NIS2 directive?
Automated security is important for cloud environments because it ensures that security measures are consistently applied across dynamic and scalable cloud resources. Under the NIS2 directive, organizations are required to maintain high levels of security and quickly address vulnerabilities. Automation helps achieve this by continuously monitoring for risks, applying patches, and enforcing policies without human intervention, reducing the risk of non-compliance and breaches.
Why is cloud security essential for compliance with the NIS2 directive?
Cloud security is essential for compliance with the NIS2 directive because the directive mandates the protection of network and information systems, including those hosted in the cloud. Ensuring robust security measures are in place for cloud environments is crucial to protect critical services and sensitive data, aligning with the NIS2 requirements for cybersecurity.
Why should organizations in Belgium consider implementing Sophos Cloud Security to comply with the NIS2 requirements from CCB Belgium?
Organizations in Belgium should consider implementing Sophos Cloud Security to comply with the NIS2 requirements from CCB Belgium because it provides comprehensive protection for cloud environments, which are increasingly becoming a target for cyber threats. By securing their cloud infrastructure, applications, and data with Sophos Cloud Security, organizations can meet the stringent cybersecurity standards set by the NIS2 directive, ensuring the resilience and security of critical services and infrastructure.
Contact us for a demo
Are you curious to learn how you can protect your cloud assets and detect and respond to threats in the cloud? Contact us for a demo via the below button.
