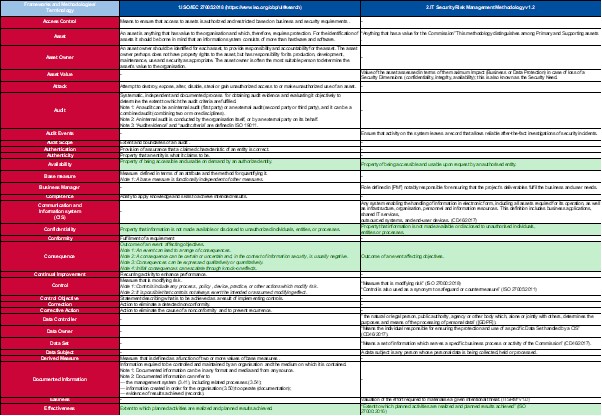
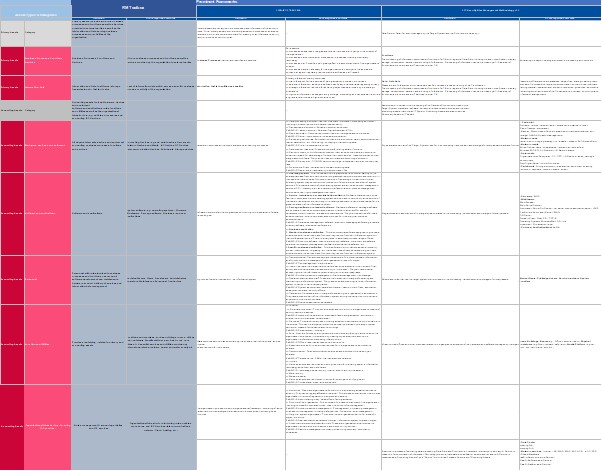
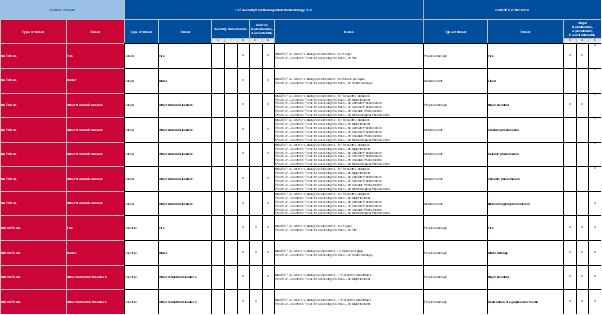
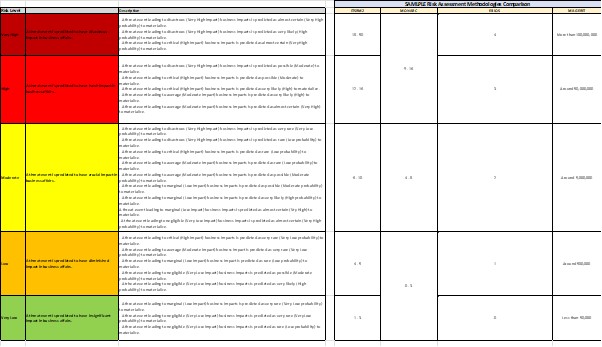
Asset Management
Asset management is an important part for knowing what to protect in our organization. What you can't see, you can't protect. Having a clear overview of the type of assets, the context of these assets and possible risks will be handled on this page.
Importance of Asset Inventory and Risk Management in Cybersecurity
Overview of Cyberfundamentals by CCB Belgium
Free download Asset worksheets
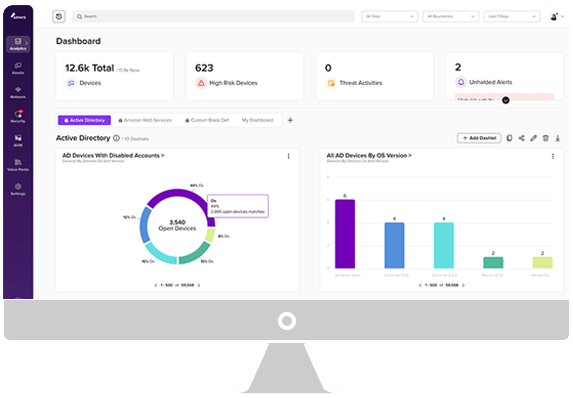
Armis: A Leader in Asset Inventory
Overview of Armis Solutions
Key Features and Capabilities
How Armis Enhances Asset Inventory
Asset Management and security
OT/IOT Security

Medical Device Security

Vulnerability Prioritization and remediation
Asset Management and security
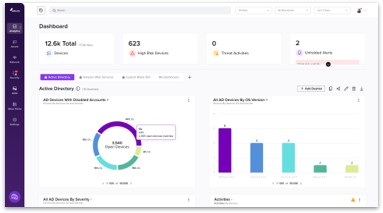
Complete asset inventory of all asset types allowing any organization to see and secure the attack surface
- Full asset inventory and enrich CMDB
IT/IoT/OT/IoMT/IIOT/Cloud/Virtual - Gap analysis and security hygiene
- Internal and external compliance reporting
- Threat detection and response
- Network segmentation and enforcement
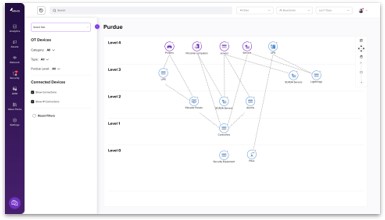
OT/IOT Security
Protect and manage OT/IOT networks and physical assets, ensure uptime and build an effective & comprehensive security strategy
- Deep visibility into all OT/IOT assets
- Visibility into OT/ICS Security hygiene
- Protect OT networks, monitor
connectivity and track behavior - Optimize uptime through Process integrity
- Bridge the IT/OT gap
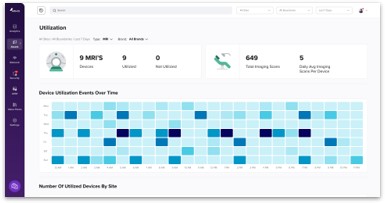
Medical Device Security
Complete visibility and security for all medical devices, clinical assets and the entire healthcare ecosystem
- Visibility and security across
all medical and clinical assets - Monitor asset behavior, utilization and
assess device compliance - Protect patient safety and ensure privacy
- Network segmentation and enforcement
- Manage FDA recalls, security and advisories
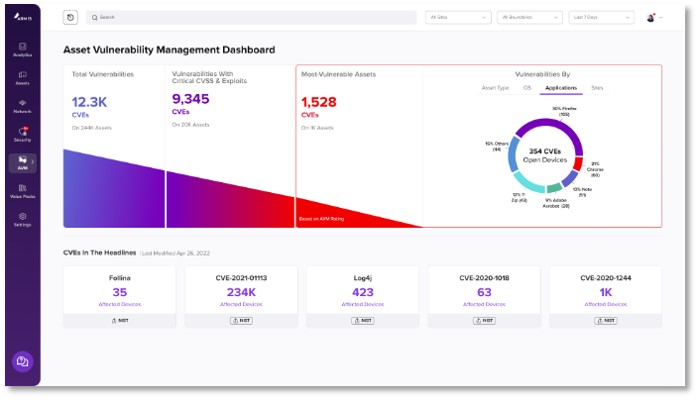
Vulnerability Prioritization and Remediation
Consolidate, prioritize and remediate all vulnerabilities;
improve MTTR with automatic remediation and ticketing workflows
- Fill coverage gaps in vulnerability detection
- Enrich with asset context and recommendations
- Prioritize vulnerabilities based on risk,
asset and business context - Remediate vulnerabilities
- Track progress and manage process
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow does Armis assist in vulnerability management as required by NIS2?
Armis assists in vulnerability management by continuously monitoring all connected devices for known vulnerabilities and providing real-time alerts when a device is found to be at risk. This proactive approach allows organizations to prioritize and remediate vulnerabilities before they can be exploited, aligning with the NIS2 directive’s requirement for effective risk management and mitigation.
How does Armis enhance asset visibility and management?
Armis enhances asset visibility and management by automatically discovering and identifying all connected devices in real-time, including unmanaged and IoT devices. It provides detailed information about each asset, such as its type, location, behavior, and security posture, allowing organizations to manage and secure their entire asset inventory effectively.
How does Armis help organizations comply with the NIS2 directive’s asset management requirements?
Armis helps organizations comply with the NIS2 directive’s asset management requirements by providing comprehensive visibility into all connected devices and ensuring that they are accounted for in the organization’s asset inventory. The NIS2 directive mandates that critical infrastructure operators maintain an accurate inventory of their assets and manage their security, which Armis facilitates through automated asset discovery and continuous monitoring.
How does Armis support the overall security strategy required by the NIS2 directive?
Armis supports the overall security strategy required by the NIS2 directive by providing comprehensive asset visibility, continuous monitoring, and real-time threat detection across all connected devices. This enables organizations to manage their assets effectively, mitigate risks, and ensure compliance with NIS2 requirements, thereby protecting critical infrastructure and maintaining the continuity of essential services.
What benefits does Armis provide in terms of incident response, and how does this relate to NIS2?
Armis provides significant benefits in terms of incident response by offering detailed insights into device behavior and security events, enabling rapid identification and isolation of compromised assets. The NIS2 directive requires organizations to have robust incident response capabilities, and Armis supports this by ensuring that any device-related incidents can be quickly detected, investigated, and resolved.
What is Armis, and how does it relate to asset management?
Armis is a cybersecurity platform specializing in asset visibility and security for managed, unmanaged, and IoT devices. It provides organizations with real-time, comprehensive insights into all connected devices, enabling effective asset management and helping to secure critical infrastructure by identifying vulnerabilities and ensuring compliance with security policies.
What role does Armis play in securing unmanaged and IoT devices?
Armis plays a crucial role in securing unmanaged and IoT devices by identifying these often-overlooked assets, assessing their security posture, and monitoring their behavior for signs of potential threats. As these devices are frequently targets for cyberattacks due to their lack of built-in security, Armis helps mitigate risks by ensuring they are managed and protected in the same way as traditional IT assets.
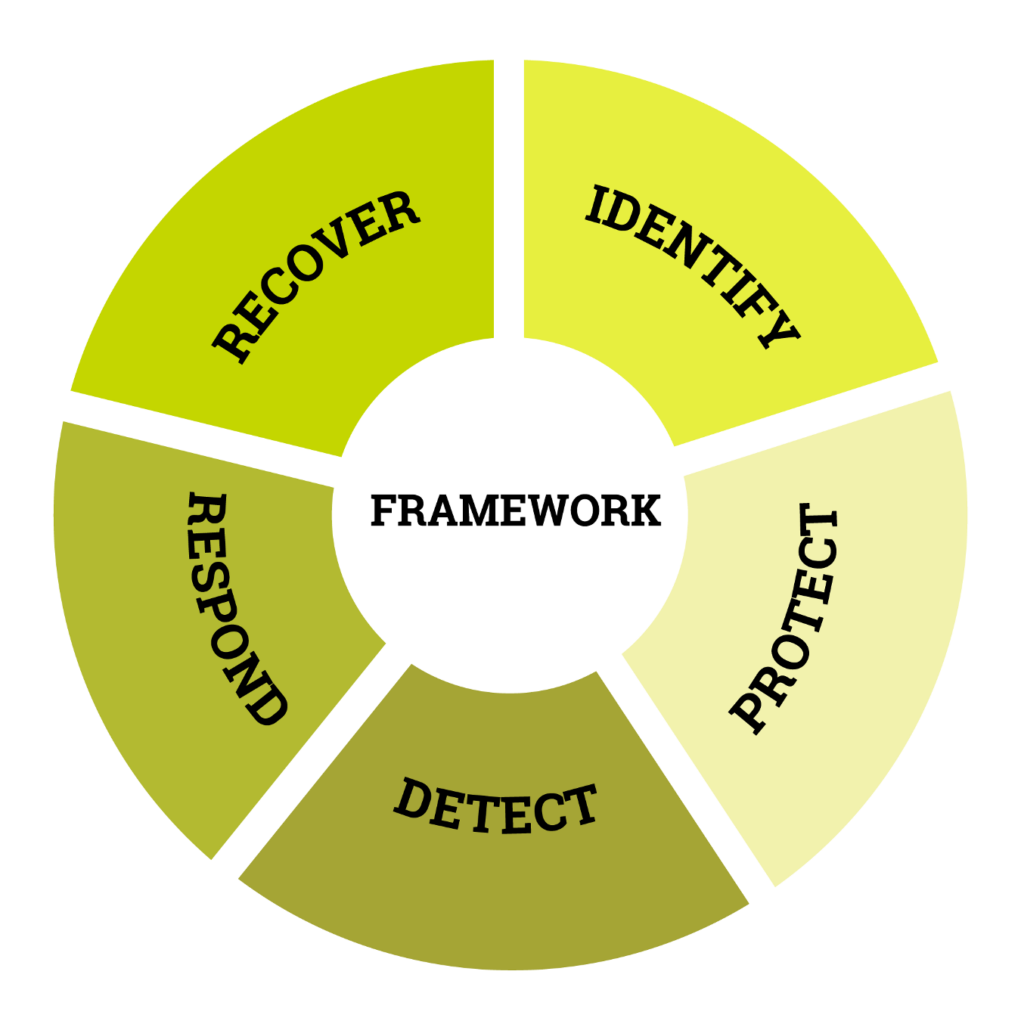
Why is asset management important for cybersecurity?
Asset management is crucial for cybersecurity because it enables organizations to identify, track, and manage all devices and systems connected to their network. Knowing what assets are present allows for effective vulnerability management, ensures that security policies are enforced consistently, and reduces the risk of unauthorized devices accessing the network.
Why is continuous asset discovery and inventory management critical for NIS2 compliance?
Continuous asset discovery and inventory management are critical for NIS2 compliance because they ensure that the organization’s asset inventory is always accurate and up-to-date. This is crucial for identifying unauthorized devices, assessing security risks, and implementing effective controls to protect critical infrastructure, all of which are mandated by the NIS2 directive.
Why is real-time asset monitoring essential for compliance with the NIS2 directive?
Real-time asset monitoring is essential for compliance with the NIS2 directive because it ensures that any changes in the network environment, such as the addition of new devices or changes in device behavior, are immediately detected and addressed. The NIS2 directive emphasizes the importance of maintaining an up-to-date view of the network and its assets to respond quickly to potential security incidents.
Contact us for a demo
Are you curious to learn whether Armis can help you with searching of assets in the network and how to protect these assets? Contact us for a demo via the below button.