Jumpcloud Identity Management & device management
JumpCloud offers one central Cloud platform that collects and simplifies the management of User Identities and a variety of devices that are used within an organization. JumpCloud ensures that users can access the IT resources from protected devices, no matter from what and where they work.
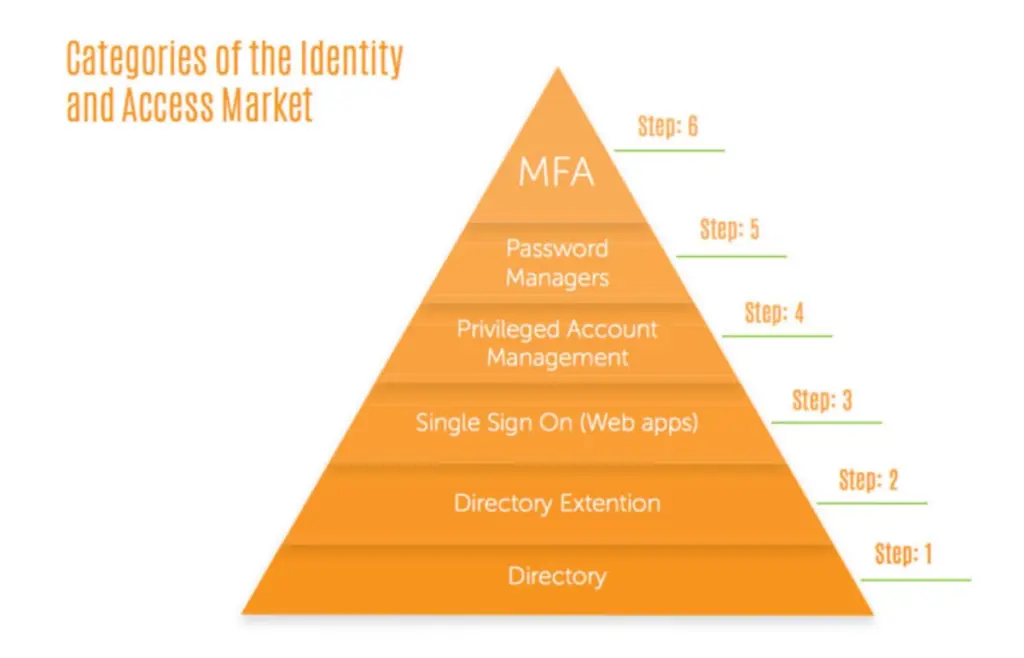
User Identity coming from different sources
What if your users identity need to be managed in different Identity resources, like an local AD server, Microsoft Entra ID or another resource, admins spend more time for on -or offboarding of employees. Especially, when an entity makes an acquisition of another entity, it becomes more difficult to get a general overview on all user identities.
Therefore, JumpCloud offers with its Core Cloud Identity platform a central overview of all users that are need to be connected to your network. With more then 900 API’s towards applications and sources, you can fill in your central directory and make the life of your admins easy with centralized management of users.

Jumpcloud Core Directory for centralized management
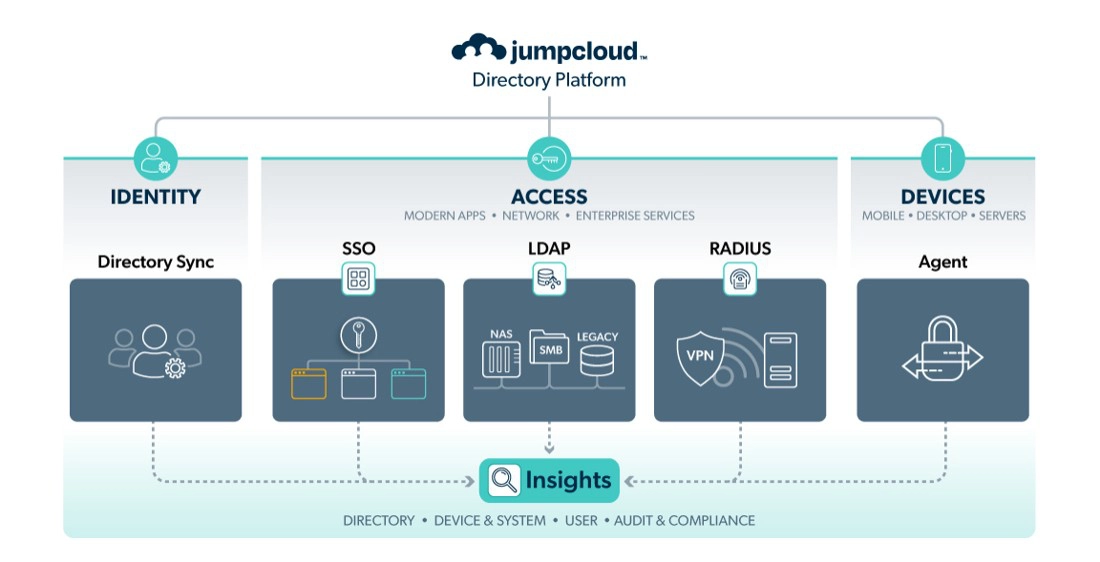
Next to the different Identity resources, the variety of devices into a network can be a challenge to manage. When the environment is basically organized with Windows machines, Linux servers and MAC OS devices need different security policies.
Therefore, the use of JumpCloud Core Directory can come in handy. Next to the Identity groups, devices are grouped into device groups. As shown in the picture above, conditional access can be used for implementing zero trust principles.
JumpCloud additional features
Mobile Device Management
With JumpCloud Mobile Device Management you can manage user access, settings, policies and GPO-like functions for workstations, servers and Smartphones.
More specific information about JumpCloud Mobile Device Management can be found on the page JumpCloud Mobile Device Management.
Automate User Onboarding and offboarding
Complete, efficient, and automated onboarding and offboarding, with robust advanced lifecycle management capabilities and open integrations.
Easily manage and automate identity lifecycle processes with JumpCloud. JumpCloud’s open directory platform centralizes identities from any source and allows for holistic identity, access, and device management under a single platform, unifying access to all resources.
More information can be found on the page Automate User Onboarding and Offboarding .
Password Management
Create, store, and protect user credentials locally on devices, and centrally manage passwords using JumpCloud’s unique decentralized architecture.
Weak, shared, or compromised passwords play a significant role in most data breaches. When end users are empowered to create and store complex passwords in a way that enhances their day-to-day experience, they play an active role in protecting your organization from malicious actors.
More information can be found on our page Jumpcloud Password Management .
Conditional Access
Security policies that adjust the requirements for access based on dynamic and situational properties.
Policies that govern how and to what degree end users can access IT resources are essential to maintain a strong security posture; however, policies built on static rulesets can be exploited or worked around. JumpCloud conditional access policies allow you to control access to resources dynamically, for example, when users aren’t on a trusted network and/or trusted device, or require additional authentication factors at login.
More information can be found on our page Conditional Access with JumpCloud .
JumpCloud Cloud Radius
Centralized authentication to Wi-Fi networks and VPNs with no hardware requirements.
Using the RADIUS protocol traditionally involves building, maintaining, and monitoring physical servers, which adds additional costs on top of expensive hardware and licensing. However, with JumpCloud Cloud RADIUS, support RADIUS throughout your organization to securely authenticate users to Wi-Fi, VPNs, switches, and other network devices with minimal in-house management.
More information can be found on the page JumpCloud Cloud Radius .
JumpCloud Single Sign on
Secure access to all your organizational resources, from anywhere, through one, unified identity.
The more sets of credentials employees have to manage and remember for different resources, the more at-risk your organization is. With JumpCloud, implement and enforce SSO and multi-factor authentication (MFA) across all SAML and OIDC-based applications to ensure access security while simplifying the login process.
More information can be found on the page JumpCloud Single Signon .
Unified Endpoint Management
Manage all your operating systems, including macOS, Windows, Linux, iOS, iPadOS and Android.
JumpCloud Unified Endpoint Management (UEM) seamlessly manages all your desktop and mobile devices, including macOS, Windows, Linux, iOS/iPadOS and Android devices. Integrate security, identity, authentication, and remote access and control into a single console for comprehensive visibility and management. Reduce the total cost of ownership of your stack with a simplified, cloud-based approach to UEM.
More information can be found on the page JumpCloud Unified Endpoint Management.
Automated Patch Management
Simplified, scheduled, and automated patch management and version control for Windows, macOS, Ubuntu Linux, browsers, and applications.
Patch management is an ongoing, high priority task that deserves clear and simple workflows for admins. With JumpCloud, patch management is easier than ever – use it to simplify your patching process, secure your systems, and satisfy ongoing compliance standards.
More information can be found on our page Automated Patch Management.
Cross-OS Device Management
Windows, Mac, and Linux device management to configure, secure, and support endpoint and server infrastructure.
Your ability to ensure end users can Make Work Happen™ shouldn’t be limited by vendors, policies, or protocols. JumpCloud’s open directory platform and cross-OS device management capabilities make it possible to centrally and securely manage every machine in your fleet, from any location, under a common set of policies and standards.
More information can be found on our page: Cross-OS Device Management
Remote Assist
Establish secure, direct connections to troubleshoot devices from anywhere in the world to solve active technical issues.
JumpCloud Remote Access provides a combination of Remote Assist and Background Tools to make secure remote sessions and troubleshoot Windows, Mac, and Linux devices from a single console.
More information about Remote Access for your network admins can be found on : Remote access
Single Sign-on
Secure access to all your organizational resources, from anywhere, through one, unified identity.
The more sets of credentials employees have to manage and remember for different resources, the more at-risk your organization is. With JumpCloud, implement and enforce SSO and multi-factor authentication (MFA) across all SAML and OIDC-based applications to ensure access security while simplifying the login process.
Single sign-on is the idea that a user only has to log in once to access all of their IT resources; they don’t have to type their username and password in over and over, or use multiple, distinct username and password pairs, to get access to everything they need to be successful at work.
Traditional SSO solutions as we generally know them today were meant to bridge the gap between users and web applications back when Microsoft Active Directory (or a similar corollary like OpenLDAP, Red Hat’s Directory 389 or others) was the most common central identity provider (IdP) out there, and physical domain controllers were found in every office to support it.
However, these LDAP-based directories provided the first real method to deliver a “single sign of experience.” In the case of Active Directory (AD), by far the most popular, a user could log in to their Windows device while it was connected to the network, and those credentials would be authenticated via the domain controller. A successful login would result in the user being able to move between Windows resources within the domain without having to log in multiple times as determined by the permissions granted to that user. This eliminated the need for users to remember a variety of passwords in order to access multiple on-prem, Windows-based resources.
However, given that AD was hosted on-prem, within the confines of an organization’s network, it could not facilitate authorization to resources that lived outside of the domain. As such, the growing number of web-based applications that grew in popularity throughout the 2000’s posed challenges to IT admins trying to control and deliver access to them in a similar, secure fashion. So the definition of SSO changed over time as AD and on-prem infrastructure failed to support access to web applications and other non-Windows-based resources that many users needed quick and secure access to.
Now, as the cloud grows even more pervasive, powerful and secure, SSO is often implemented as part of a larger identity access management (IAM) solution, such as a directory service, rather than as a separate add-on, which gives IT admins more control and visibility into what users have access to. SSO solutions that fit into this mold provide users with access to virtually all of their IT resources (networks, devices, apps, file servers, and more) through a single login.
Shadow IT
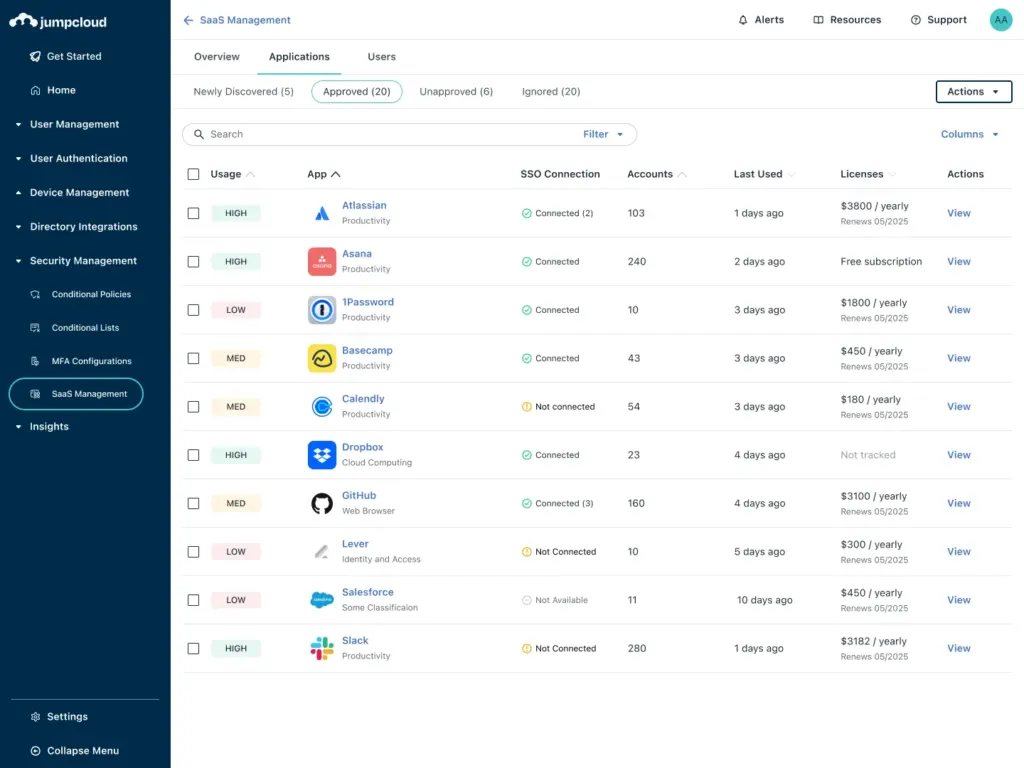
You have enough to deal with when it comes to critical day-to-day operations. Onboarding and offboarding employees and contractors, maintaining networks and shared resources, troubleshooting end user technical issues, combatting security threats… the list goes on and on. So long as you have visibility into the issues at hand, and the tools to react and respond to them, there isn’t much that can keep a well-organized team down.
Unless of course, IT is happening in the shadows.
It may sound like a bad horror movie, but shadow IT is a real phenomenon that happens for (mostly) the right reasons; employees seek solutions that help them be more productive, more efficient, and more reliable. The problem is that they seek out these solutions without IT’s oversight and governance. Since modern shadow IT is largely made up of SaaS applications that exist outside of IT’s organizational boundaries, this can lead to operational inefficiencies, bloated costs, and unknown security vulnerabilities.
To help you and your organization get a better handle on the unsanctioned (and sanctioned) use of SaaS applications across your fleet, JumpCloud is announcing the general availability (GA) of JumpCloud SaaS Management.
Contact us for a demo
Are you curious to learn how JumpCloud can help you to manage the identities and devices in your network? Contact us for a demo via the below button.
