Endpoint Protection
Within Endpoint Protection, Kappa Data can offer you the solutions of Sophos. Intercept X endpoint protection is beign offered in different variations as explained below.

Endpoint protection with Sophos
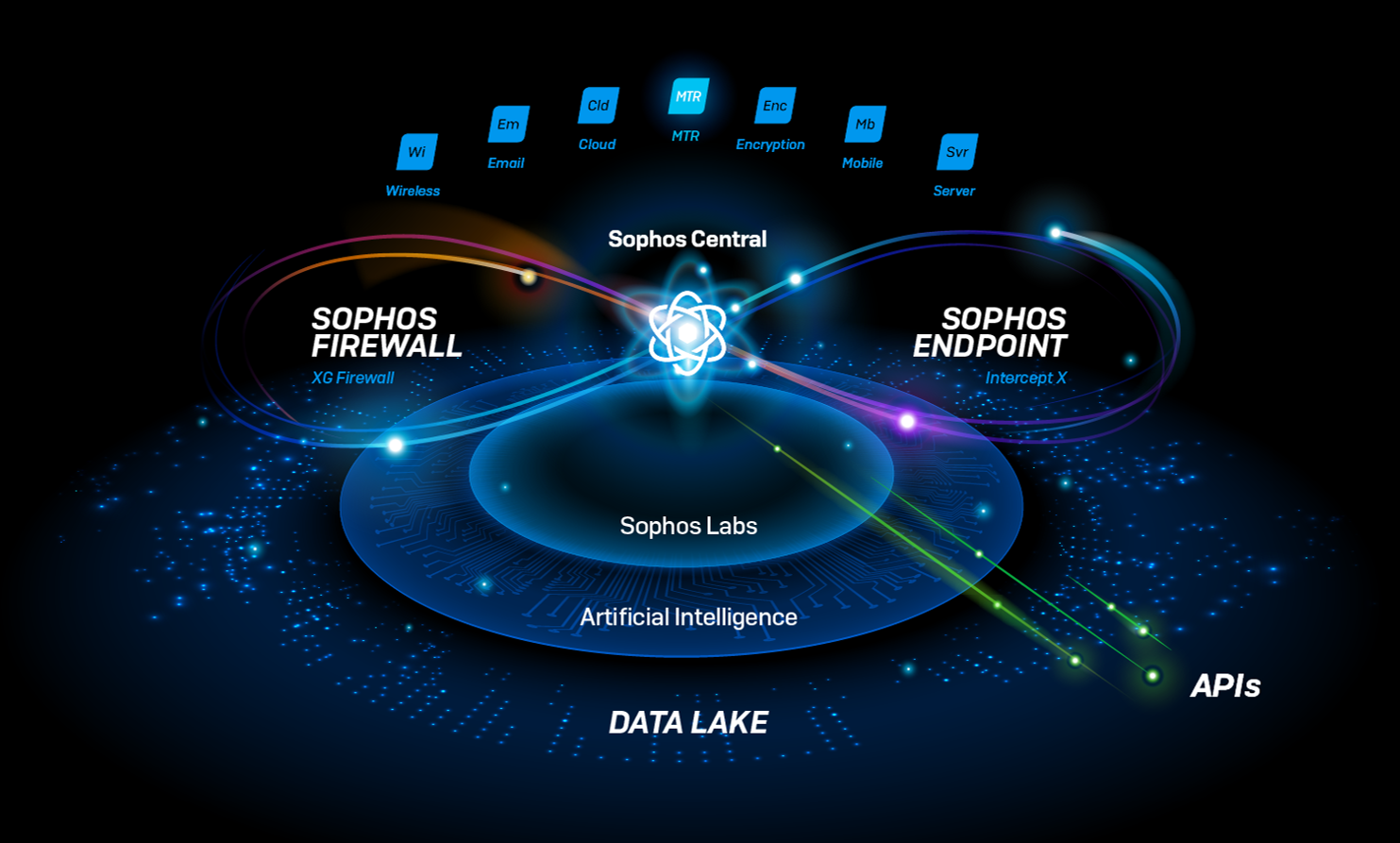
Definition of Endpoints for protection

End protection features
Ransomware protection
Sophos Endpoint’s CryptoGuard technology stops harmful encryption as it happens and automatically restores affected files, reducing business disruption. It uses advanced file content analysis to protect your data from ransomware attacks, whether they come from local or remote sources, including new types.
Sophos Endpoint offers the strongest hands-off protection against remote ransomware.
Anti-exploitation
Right from the start, Sophos Endpoint enhances the basic security in Microsoft Windows with over 60 unique and ready-to-use exploit defenses. It guards against fileless attacks and new, unknown threats by blocking the methods attackers use at every stage of an attack.
Adaptive defenses
One of the special defense mechanisms of Sophos Endpoint Protection is the adaptive defense system. This system automate protection that adapts in response to active adversaries and hands-on-keyboard attacks.
Adaptive attack protection
Adaptive attack protection automatically strengthens security on a device when it detects a direct attack. This stops the attacker from proceeding by reducing vulnerable areas and containing the threat, giving you more time to respond.
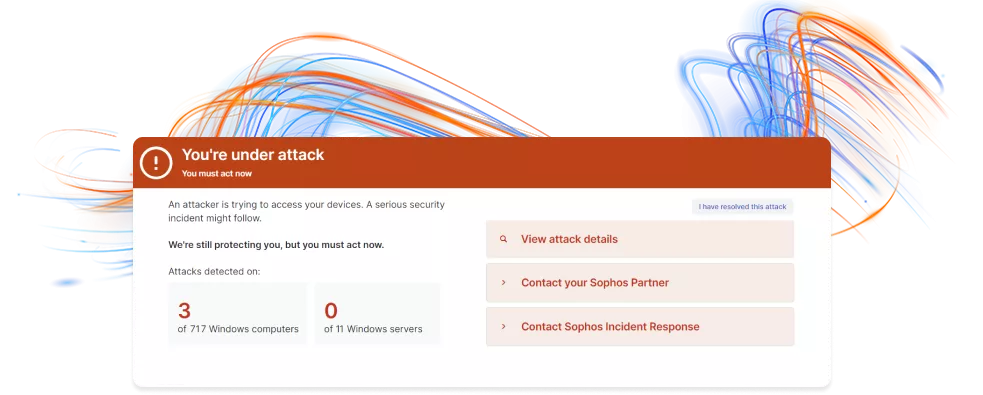
Warning Critical attack
A critical attack warning notifies you if suspicious activity is found on multiple devices or servers. It alerts all administrators in Sophos Central, giving you information about the attack. You can respond with Sophos XDR, get help from your partner, or contact the Sophos Incident Response team.
Protection layers endpoint protection
Endpoint protection solutions of Sophos are managed one central application in the cloud “Sophos Central”.
Sophos Central is a cloud-based platform for managing all Sophos products in one central place. Our recommended protection technologies are enabled by default, so you immediately have the strongest protection settings with no tuning required. Granular control is also available.
Sophos Endpoint is the most robust zero-touch endpoint defense against remote ransomware.
Some vendors including Carbon Black, CrowdStrike and SentinelOne rely solely on pre-trained machine learning models.
Some vendors provide only a limited set of commands through their consoles.
Some vendors including CrowdStrike and Microsoft do not support the use of third-party endpoint technology.
Techical Features Endpoint Protection
| Sophos Endpoint | Intercept X Advanced | Intercept X Advanced with XDR | Intercept X Advanced with MDR Complete |
|---|---|---|---|
Web Protection | |||
Web Control | |||
Download Reputation | |||
Application Control | |||
Peripheral Control | |||
Data Loss Prevention | |||
Server Lockdown (application whitelisting) | |||
Full Disk Encryption | Add-on | Add-on | Add-on |
Ransomware file protection (CryptoGuard) | |||
Remote ransomware protection (CryptoGuard) | |||
Ransomware Master Boot Record (MBR) protection | |||
Context-sensitive Defense: | |||
Context-sensitive Defense: | |||
Deep Learning AI-powered malware prevention | |||
Anti-malware file scanning | |||
Potentially Unwanted App (PUA) blocking | |||
Live Protection cloud-lookups | |||
Behavioral Analysis | |||
Anti-Exploitation (60+ mitigations) | |||
Application Lockdown | |||
Anti-malware Scan Interface (AMSI) | |||
Malicious Traffic Detection | |||
Intrusion Prevention System (IPS) | |||
File Integrity Monitoring (Servers) | |||
Extensive data on-device and in the cloud | - | ||
Cloud data retention | - | 90 days | 90 days |
Additional cloud storage available | - | 1 Year (Add-on) | 1 Year (Add-on) |
Rich on-device data for real-time insights | - | ||
Compatible with non-Sophos solutions | - | ||
Suspicious event detections | - | ||
AI-powered prioritization of detections | - | ||
Automatic MITRE Framework mapping | - | ||
Cross-product event correlation and analysis | - | ||
RCA threat graphs | |||
Automatic and manual case creation | - | ||
Live Discover query tool | - | ||
Scheduled queries | - | ||
Simple (SQL-less) search | - | ||
Forensic data export | - | ||
On-demand Sophos X-Ops threat intelligence | - | ||
Automatic malware cleanup | |||
Automatic ransomware file encryption roll-back | |||
Automatic process termination | |||
Synchronized Security: Automatic device isolation via Sophos Firewall | |||
On-demand device isolation | - | ||
Live Response remote terminal access | - | ||
24/7 threat monitoring and response | - | - | |
Weekly and monthly reporting | - | - | |
Health Check | - | - | |
Expert-led threat hunting | - | - | |
Threat containment | - | - | |
Direct call-in support during active incidents | - | - | |
Full-scale incident response: threats are fully eliminated | - | - | |
Root cause analysis | - | - | |
Dedicated Incident Response Lead | - | - | |
$1M Breach Protection Warranty | - | - |
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow does Sophos Endpoint Protection contribute to overall cybersecurity resilience?
Sophos Endpoint Protection contributes to overall cybersecurity resilience by providing robust defense mechanisms against a wide range of threats. Its advanced threat prevention, detection, and response capabilities ensure that endpoints are protected from malware, ransomware, exploits, and other attacks. By integrating with other security solutions and offering centralized management, it helps organizations maintain a strong security posture, respond to incidents quickly, and minimize the impact of cyberattacks.
How does Sophos Endpoint Protection enhance security in the current cybersecurity landscape?
Sophos Endpoint Protection enhances security by utilizing advanced technologies such as deep learning, artificial intelligence, and behavioral analysis to detect and block sophisticated threats. It offers comprehensive protection against malware, ransomware, and exploits, and includes features like anti-phishing, web protection, and application control to secure endpoints against various attack vectors.
How does Sophos Endpoint Protection integrate with other security tools?
Sophos Endpoint Protection integrates seamlessly with other Sophos security tools through the Sophos Central management platform. This integration allows for centralized management, streamlined policy enforcement, and coordinated response across endpoints, networks, and other security layers. It enhances visibility and control, making it easier to manage and secure the entire IT environment.
How does Sophos Endpoint Protection support threat detection and response?
Sophos Endpoint Protection supports threat detection and response through its EDR and XDR capabilities. These features allow security teams to conduct detailed investigations, hunt for threats, and respond to incidents effectively. They provide visibility into the root cause of attacks, enable remediation actions, and offer automated detection and response to minimize the impact of security incidents.
What are the key features of Sophos Intercept X?
Key features of Sophos Intercept X include:
- Deep Learning Anti-Malware: Uses AI to detect and block malware with high accuracy.
- Exploit Prevention: Protects against zero-day vulnerabilities and exploit-based attacks.
- Ransomware Protection: Detects and blocks ransomware attacks and automatically rolls back encrypted files.
- Active Adversary Mitigations: Protects against advanced threats such as credential theft and lateral movement.
- EDR/XDR Capabilities: Provides enhanced threat hunting, incident response, and extended visibility across the security environment.
What is Sophos Endpoint Protection?
Sophos Endpoint Protection is a comprehensive cybersecurity solution designed to protect endpoint devices, such as laptops, desktops, and servers, from a wide range of cyber threats, including malware, ransomware, exploits, and phishing attacks. It combines advanced threat prevention, detection, and response capabilities to ensure robust security for endpoints.
What role does artificial intelligence play in Sophos Endpoint Protection?
Artificial intelligence (AI) plays a critical role in Sophos Endpoint Protection by enhancing its ability to detect and block threats. AI-driven technologies, such as deep learning, analyze vast amounts of data to identify patterns and anomalies associated with malware, ransomware, and other cyber threats. This enables Sophos Endpoint Protection to detect and respond to both known and unknown threats with high accuracy and speed.
What variations of Sophos Endpoint Protection are available?
Variations of Sophos Endpoint Protection include:
- Sophos Intercept X: Advanced endpoint protection with deep learning anti-malware, exploit prevention, and ransomware protection.
- Sophos Central Endpoint Protection: Cloud-managed endpoint security offering essential protection against malware and other threats.
- Sophos Intercept X with EDR (Endpoint Detection and Response): Combines Intercept X with EDR capabilities for enhanced threat hunting and incident response.
- Sophos Intercept X Advanced with XDR (Extended Detection and Response): Extends EDR to include data from other Sophos products, providing a more comprehensive view of the security landscape.
Why is Sophos Endpoint Protection important for compliance with the NIS2 law in Belgium?
The NIS2 directive in Belgium mandates that organizations managing critical infrastructure and essential services implement robust cybersecurity measures. Sophos Endpoint Protection helps organizations comply with NIS2 by providing advanced threat prevention, detection, and response capabilities, ensuring the security and resilience of their endpoint devices and protecting sensitive data from cyber threats.
Why should an organization consider using Sophos Endpoint Protection?
An organization should consider using Sophos Endpoint Protection to ensure comprehensive security for their endpoint devices. It offers advanced threat prevention, detection, and response capabilities, reducing the risk of data breaches and cyberattacks. Additionally, its integration with other Sophos security products provides a unified security solution that enhances overall protection and operational efficiency.
Contact us for a demo
Are you curious to learn how Sophos can help you with advanced endpoint protection? Contact us for a demo via the below button.
