iOS, Android, Windows 10, macOS
Mobile Protection
Mobile Protection is an important measure for securing the use of smartphones, which is evident today, but often forgotten. Within Mobile Security, you can install an agent that controls the security on the mobile device and managed on a central portal. Within this solution we will addess as well the onboarding and offboarding capabilities
Ask for a demoWhy using Sophos Mobile for your security?
As organizations increasingly rely on mobile devices for daily operations, the security of these devices has become paramount. Mobile devices, such as smartphones and tablets, are often used to access sensitive data, communicate with clients, and manage critical infrastructure. However, they also represent a significant security risk. Cybercriminals are constantly developing new methods to exploit vulnerabilities in mobile devices, making them a prime target for attacks.
Sophos Mobile is a secure Unified Endpoint Management (UEM) solution that helps businesses spend less time and effort to manage and secure traditional and mobile endpoints. The only UEM solution that integrates natively with a leading next-gen endpoint security platform, Sophos Mobile supports management of Windows 10, macOS, iOS, and Android devices.
Productivity
Security
Simplicity
Value
Why Mobile Security is Critical
-
Increased Attack Surface: Mobile devices expand the attack surface of an organization, providing more entry points for cybercriminals. This is particularly concerning in industries covered by NIS2, where the security of critical infrastructure is at stake.
-
Data Breaches: Mobile devices often store or access sensitive data, making them a target for data breaches. A compromised mobile device can lead to unauthorized access to critical systems, resulting in significant financial and reputational damage.
-
Compliance: With NIS2’s stringent cybersecurity requirements, organizations must ensure that all endpoints, including mobile devices, meet the necessary security standards. Failure to secure mobile devices could lead to non-compliance and the associated penalties.
Challenges in Mobile Security
- Diverse Operating Systems: The variety of mobile operating systems (iOS, Android, etc.) makes it challenging to implement uniform security measures across all devices.
- BYOD (Bring Your Own Device): Many organizations allow employees to use their personal devices for work purposes. This introduces additional security risks, as these devices may not be adequately protected.
- Rapidly Evolving Threat Landscape: Mobile threats are constantly evolving, with new vulnerabilities and attack vectors emerging regularly. Organizations must stay ahead of these threats to maintain security.
How Sophos Mobile Management Enhances Security
Key Features of Sophos Mobile Management
-
Unified Endpoint Management (UEM)
Sophos Mobile Management provides a unified platform for managing all mobile devices within an organization, regardless of the operating system. This includes iOS, Android, and Windows devices. UEM allows organizations to enforce security policies consistently across all devices, ensuring that every mobile endpoint meets the necessary security standards.
-
Mobile Threat Defense (MTD)
One of the standout features of Sophos Mobile Management is its Mobile Threat Defense (MTD) capabilities. MTD uses advanced threat detection technologies to identify and mitigate a wide range of mobile threats, including malware, phishing attacks, and network-based threats. By proactively detecting and responding to threats, Sophos MTD helps prevent security incidents before they can cause damage.
-
Compliance Management
Sophos Mobile Management includes robust compliance management tools that help organizations adhere to NIS2 requirements. The platform allows administrators to enforce compliance policies, such as encryption, password requirements, and device restrictions. It also provides detailed reporting and auditing capabilities, making it easier to demonstrate compliance to regulatory authorities.
-
Application Security
With Sophos Mobile Management, organizations can control which applications are installed on mobile devices. This helps prevent the installation of malicious apps and ensures that only approved, secure applications are used. The platform also allows for the management of application permissions, reducing the risk of data leakage through insecure apps.
-
Data Loss Prevention (DLP)
Data Loss Prevention is a critical component of mobile security. Sophos Mobile Management includes DLP features that prevent sensitive data from being transmitted or stored on mobile devices in an insecure manner. This includes controlling access to cloud storage services, blocking unauthorized file transfers, and ensuring that data is encrypted both at rest and in transit.
-
Secure Containerization
For organizations that allow BYOD, secure containerization is an essential feature. Sophos Mobile Management allows for the creation of secure containers on mobile devices, where work-related data and applications are isolated from personal data. This ensures that sensitive information remains protected, even on personal devices.
-
Remote Management and Wipe
In the event of a lost or stolen device, Sophos Mobile Management allows administrators to remotely locate, lock, and wipe the device. This minimizes the risk of data breaches and ensures that sensitive information does not fall into the wrong hands.
-
User-Friendly Interface
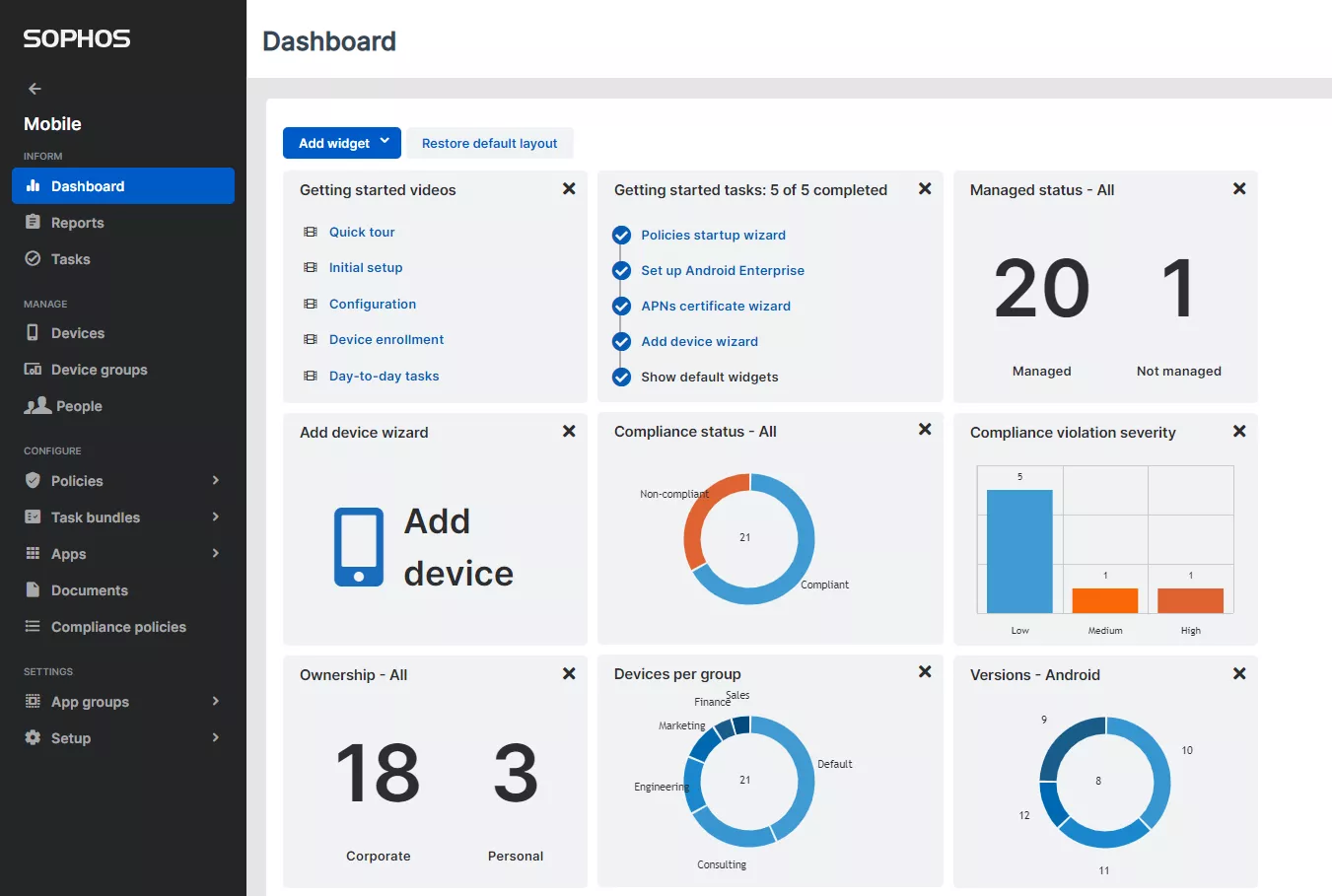
Despite its advanced features, Sophos Mobile Management offers a user-friendly interface that makes it easy for administrators to manage and monitor mobile devices. The platform is designed to be intuitive, with a dashboard that provides real-time insights into the security status of all devices within the organization.
Devices
Apps
Flexible
Security
Intercept X for Mobile
Intercept X for Mobile protects users, their devices, and corporate data from known and never-before-seen mobile threats by leveraging our market leading Intercept X deep learning engine. Managed seamlessly through Sophos Central, alongside Sophos’ entire portfolio of next-generation cybersecurity solutions. Enhance your protection against the most advanced threats with our industry-leading mobile threat defense solution, Intercept X for Mobile.
Extended Detection and Response (XDR)
Expand your organization’s visibility by incorporating Android,iOS and Chrome OS threat and management data into Sophos XDR. Perform detailed threat hunting and IT ops tasks.
- Check devices for vulnerabilities or unwanted apps
- Locate devices that are unpatched or have out of date software
- Investigate and respond across mobile, endpoint, network, email, cloud and server data from a single console
Sophos Central Management
- Full UEM side-by-side with endpoint, network, and server security
- Get started in minutes with no server installation
- Easy-to-use, unified, and web-based admin interface
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow does Sophos Mobile enhance the security of mobile devices in an organization?
Sophos Mobile enhances the security of mobile devices by providing features such as device encryption, remote wipe, anti-malware protection, and secure containerization of corporate data. It also allows administrators to enforce security policies, such as password requirements and app restrictions, ensuring that all mobile devices comply with the organization’s security standards and reduce the risk of data breaches.
How does Sophos Mobile support incident response and compliance with NIS2 requirements?
Sophos Mobile supports incident response by allowing administrators to remotely manage and secure mobile devices in the event of a security incident. For example, if a device is lost or stolen, it can be remotely wiped to prevent unauthorized access to sensitive data. This capability aligns with the NIS2 directive’s requirements for rapid incident response and mitigation, ensuring that mobile devices do not pose a risk to the security of critical infrastructure.
What is Sophos Mobile, and why is it important for managing mobile devices in an organization?
Sophos Mobile is a comprehensive mobile device management (MDM) and mobile security solution that enables organizations to secure, manage, and control mobile devices, applications, and data. It is important for managing mobile devices because it helps protect sensitive information on smartphones, tablets, and other mobile devices from unauthorized access, malware, and other cyber threats, ensuring that mobile devices are compliant with the organization’s security policies.
Why is mobile device security critical for compliance with the NIS2 directive?
Mobile device security is critical for compliance with the NIS2 directive because mobile devices are often used to access sensitive information and critical infrastructure systems. The NIS2 directive requires organizations to implement robust security measures to protect network and information systems, including those accessed via mobile devices. By securing mobile devices with solutions like Sophos Mobile, organizations can ensure that mobile endpoints do not become a weak link in their cybersecurity defenses, thus meeting the requirements of the NIS2 directive.
Why should organizations in Belgium consider implementing Sophos Mobile to align with the NIS2 requirements from CCB Belgium?
Organizations in Belgium should consider implementing Sophos Mobile to align with the NIS2 requirements from CCB Belgium because it provides a comprehensive solution for managing and securing mobile devices. As mobile devices are increasingly used to access critical systems and data, ensuring their security is essential for meeting the stringent cybersecurity standards set by the NIS2 directive. Sophos Mobile helps organizations maintain control over their mobile environments, protect sensitive information, and ensure compliance with NIS2 regulations, ultimately safeguarding their critical infrastructure.
Contact us for a demo
Are you curious to learn how Sophos Mobile can help you in having an extra security layer for your mobile devices? Contact us for a demo via the below button.
