Zero Trust Network Access (ZTNA)
Zero Trust Network Access or ZTNA is a new way to connect your applications in a secure way. Via ZTNA, you control who may access which application(s). ZTNA brings more control on the cybersecurity within organisations. In this article you will learn which ZTNA solutions Kappa Data can offer.

Zero Trust Network Access, what is it?


Verify Every User

Device control
Use of applications

Public applications
Datacenter hosted applications
Internal applications
The location
Zero Trust Network Access solutions at Kappa Data
Zero Trust Network Access of Barracuda Networks
Zero Trust Network Access Cato Networks
Extreme Networks Universal Zero Trust Network Access

Juniper Secure Edge
Sophos Zero Trust Network Access
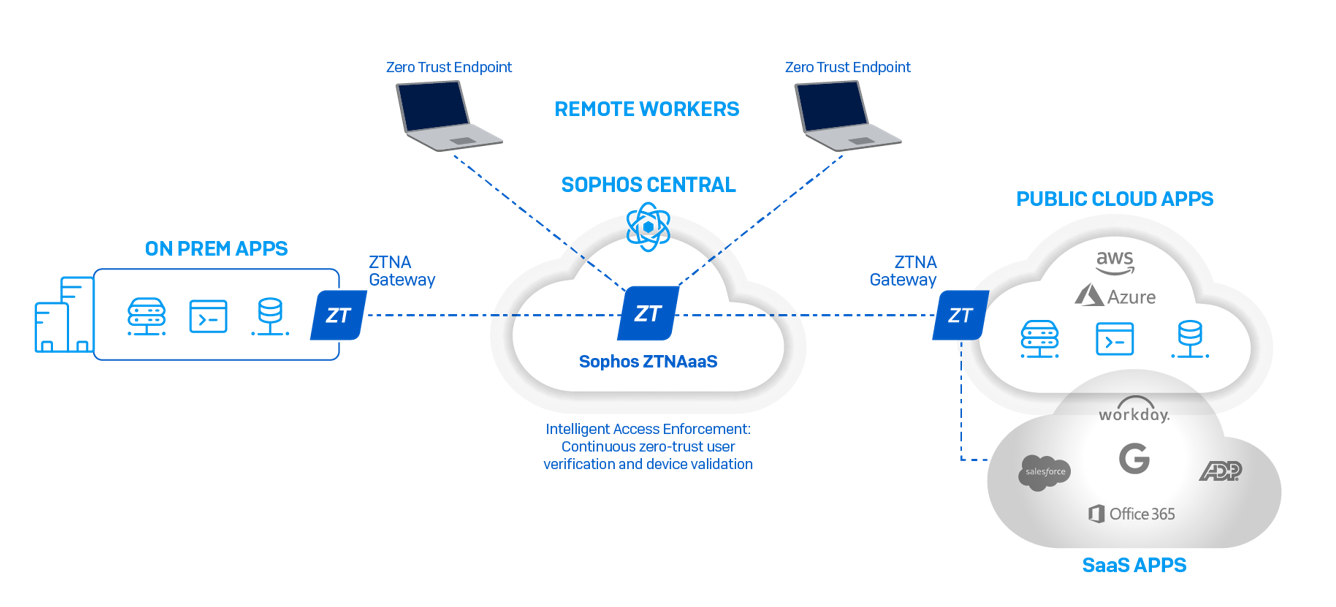
Why choosing for Zero Trust Network Access?
Zero Trust Network Access (ZTNA) is gaining popularity among organizations looking to bolster their cybersecurity defenses. This approach fundamentally shifts the security paradigm to “never trust, always verify,” ensuring that every access request is authenticated, authorized, and encrypted before granting access to resources. This rigorous verification process significantly reduces the risk of unauthorized access and lateral movement within the network.
One of the primary benefits of ZTNA is its ability to minimize the attack surface. By concealing network resources from unauthorized users, ZTNA makes it considerably harder for attackers to discover and exploit vulnerabilities. This ensures that only authenticated and authorized users can see and access sensitive resources, thus enhancing overall security.
ZTNA also offers improved visibility and control over network activities. Detailed logging and monitoring of access requests provide insights into who is accessing what resources and when. This enhanced visibility helps organizations quickly identify and respond to suspicious activities, bolstering their defense mechanisms.
In the era of remote work, traditional perimeter-based security models have become less effective. ZTNA supports secure access to corporate resources from any location and device, ensuring that remote workers can operate securely. This capability is crucial as the workforce becomes increasingly mobile and dispersed.
Another advantage of ZTNA is its granular access control. It enables fine-grained policies based on the user’s identity, device posture, and context of the access request. By ensuring users have only the minimum necessary access, ZTNA reduces the risk of insider threats and unauthorized access to sensitive information.
Implementing ZTNA can also simplify security architecture by eliminating the need for traditional VPNs and complex network segmentation. This simplification can lead to cost savings in terms of infrastructure and management overhead, making ZTNA an economically attractive option.
Compliance and regulatory requirements regarding data protection and access controls are stringent in many industries. ZTNA helps organizations meet these requirements by providing robust access controls and detailed audit logs, which are essential for regulatory compliance.
ZTNA is particularly well-suited for modern IT environments that include cloud services, SaaS applications, and hybrid infrastructures. It provides consistent security policies across on-premises and cloud environments, ensuring comprehensive protection.
By continually verifying access requests and limiting the exposure of sensitive resources, ZTNA enhances resilience against breaches. This approach helps contain threats more effectively and minimizes the potential impact of security incidents.
Finally, ZTNA can improve the user experience by offering seamless and secure access to resources without the need for cumbersome VPN connections. This ease of access ensures that users can efficiently perform their tasks while maintaining robust security measures.
In summary, ZTNA provides a robust, flexible, and scalable approach to network security that aligns well with the evolving threat landscape and modern IT practices. Its comprehensive benefits make it an attractive choice for organizations aiming to enhance their cybersecurity posture.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow does ZTNA differ from traditional VPN connections?
ZTNA differs from traditional VPN connections in several key ways:
- Granular Access Control: ZTNA grants access only to specific applications or resources based on verified user identities and device compliance, rather than providing broad network access like VPNs.
- Continuous Verification: ZTNA continuously verifies user and device credentials during each access attempt, while VPNs typically authenticate users only at the beginning of the session.
- Least Privilege Principle: ZTNA operates on the principle of least privilege, limiting users’ access to only the resources they need, reducing the risk of lateral movement within the network.
- Cloud Readiness: ZTNA is designed to secure access to both on-premises and cloud-based resources, making it more suitable for modern hybrid and multi-cloud environments.
How does ZTNA improve user experience compared to VPN connections?
ZTNA improves user experience in several ways:
- Seamless Access: Provides users with seamless access to applications without the need to establish and manage a separate VPN connection.
- Reduced Latency: Directly connects users to the applications they need, often resulting in lower latency and faster performance.
- Simplified Connectivity: Eliminates the complexity of VPN configurations and maintenance, making it easier for users to connect securely.
- Adaptive Access Policies: Dynamically adjusts access policies based on user context and behavior, providing a more flexible and user-friendly experience.
What are the key components of a ZTNA solution?
Key components of a ZTNA solution include:
- Identity and Access Management (IAM): Ensures user identities are verified and access policies are enforced based on user roles and attributes.
- Device Posture Assessment: Evaluates the security status of devices before granting access to ensure compliance with organizational policies.
- Micro-Segmentation: Divides the network into smaller, isolated segments to apply more precise security controls and limit access.
- Contextual Access Policies: Enforces access policies based on contextual factors such as user location, device type, and behavior.
- Continuous Monitoring: Continuously monitors user and device activity to detect and respond to anomalies in real-time.
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a security model that assumes no user or device, whether inside or outside the network, should be trusted by default. Instead, ZTNA continuously verifies every access request using strict identity verification, device compliance checks, and context-based security policies before granting access to applications and data.
Contact us for a demo
Are you curious to learn how Kappa Data can help you to deliver the right Zero Trust Network Access solution? Contact us for a demo via the below button.
