Universal ZTNA
Universal Zero Trust Network Access of Extreme Networks combines the functions of a Network Access Control (NAC) system with Zero Trust Network Access (ZTNA).
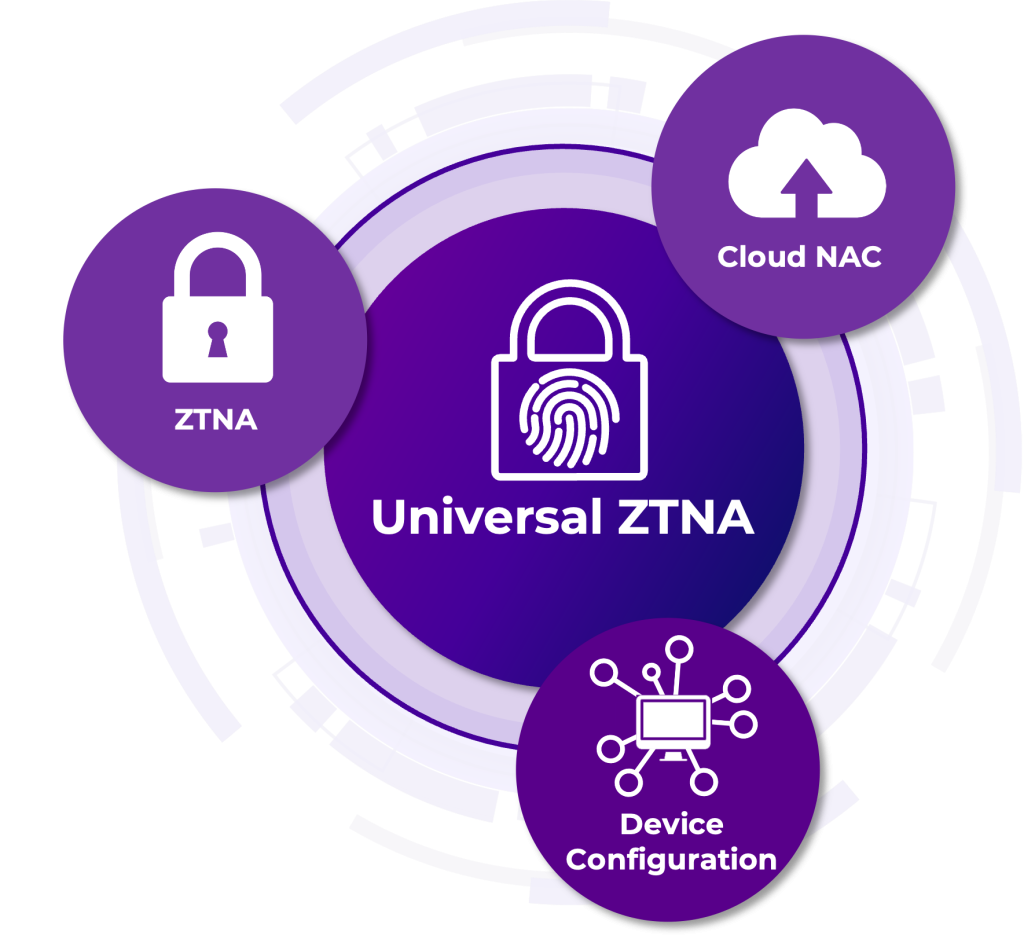
UZTNA, combination of ZTNA and NAC
In this article, we go a step further.
What is if we add Zero Trust Network Access (ZTNA) to a NAC system?
NAC + ZTNA = 3
We are 2024. Cybersecurity has become an integral part of our society. A lot of companies are therefore constantly shifting gears to raise their cybersecurity levels.
This year, NIS2 is also around the corner, which defines various chalk lines within which a company must operate to be compliant with cybersecurity measures imposed by governments.
This creates a big challenge for network/security engineers who have to set up environments so that everyone in the organisation can be connected to the necessary applications in a safe and efficient way, whether they are running on-prem or in the cloud.
Within this connectivity component, you are faced with two challenges. On the one hand: how do I ensure that my users who are on-site connect securely to the network in a connected and authenticated way. On the other hand: how do I ensure that my users in any location (at home, at clients’ premises, at the coffee shop, etc.) can securely connect to the required applications.
Solutions such as Network Access Control and Zero Trust Network Access already exist for the above challenges. The problem lies more in the fact that these are separate products, and there is no way to introduce a unified policy that solves both challenges allowing this to be managed in one place.
As several vendors recognised this problem, a new term was introduced, namely Universal Zero Trust Network Access. Universal ZTNA ensures that 1 policy is introduced for users regardless of where they are located.
Universal ZTNA, however, is a term that is highlighted differently by quite a few vendors. Certain vendors assume that no matter where you are, you set up a client that connects to a central point (full-tunnel) and all network traffic passes through that tunnel.
Centrally, all traffic is inspected and processed according to a set of policies, and your traffic is also routed to the relevant network (IPSec, SaaS,…). Other vendors will instead adopt the principle discussed above, where there is both a Cloud NAC offered and a ZTNA solution for remote workers.
In this article, we discuss Extreme Networks’ solution in more detail.
Extreme Networks recently added Universal ZTNA to its portfolio. This solution combines Cloud NAC for the campus with ZTNA for remote workers. Below in more detail how the different solutions are put together and exactly what the unified policy looks like.
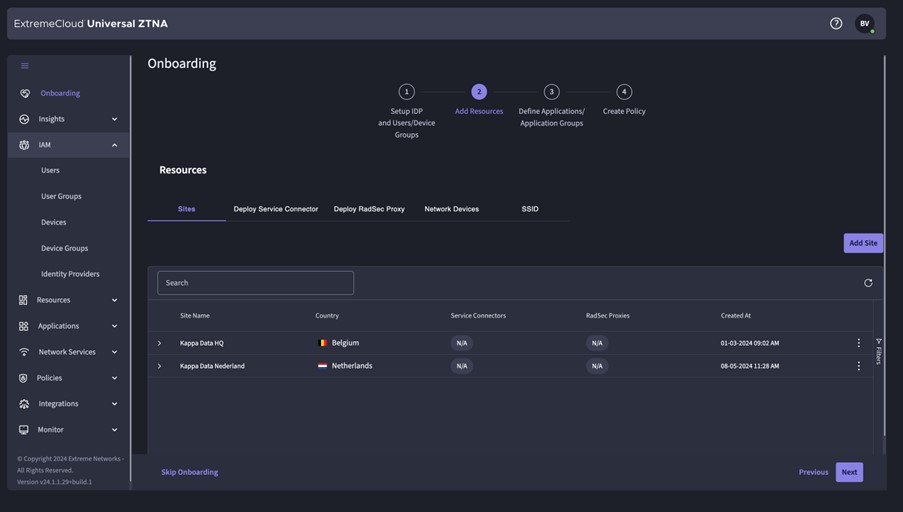
Cloud NAC
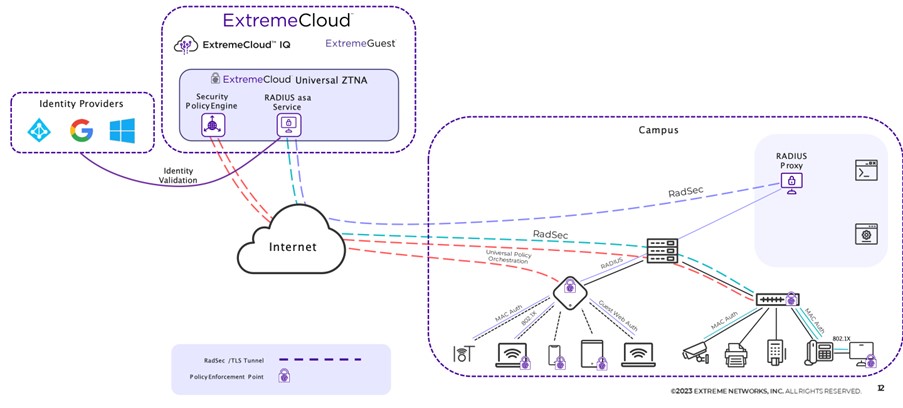
The diagram above shows how the Cloud NAC works correctly and which components are present.
Within the Cloud NAC, there are several components:
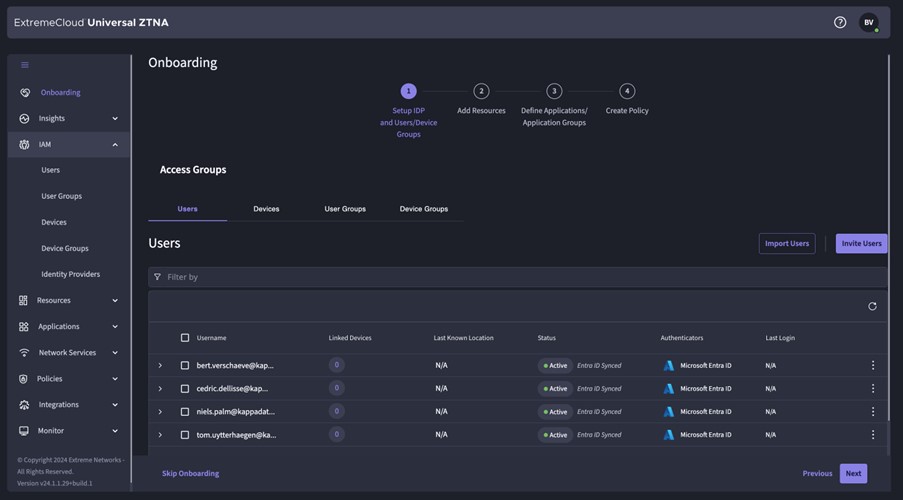
- Identity Providers: An Identity Provider is needed to import the users that will use the UZTNA solution. Within Cloud NAC, these are used as the backend authentication server for 802.1X Radius. A user connecting to the network (whether wireless or wired) is authenticated via the Radius service against the credentials known within the Identity Provider (Entra ID, Google Workspace, Onprem AD).
- ExtremeCloud: within ExtremeCloud, you have two applications:
- ExtremeCloud IQ: Extreme Networks’ SaaS Network Management solution in which switches and access points are managed. For this solution, you configure the link between LAN/WLAN and the UZTNA Cloud NAC within ExtremeCloud IQ
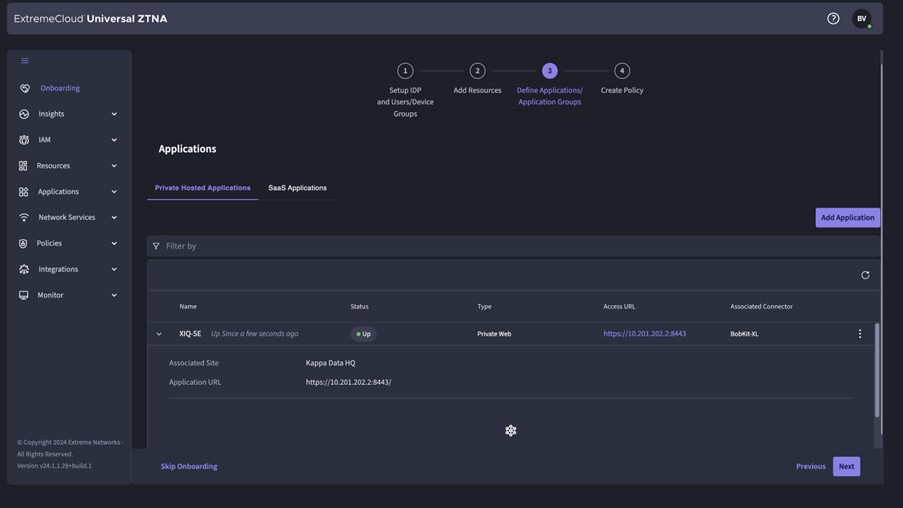
- ExtremeCloud Universal ZTNA: This is the UZTNA application in which you will configure all policies, rules, etc.
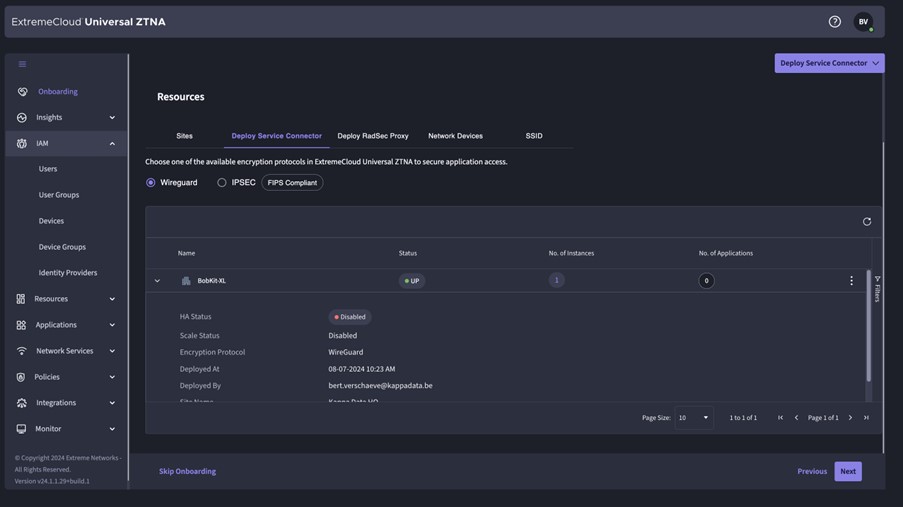
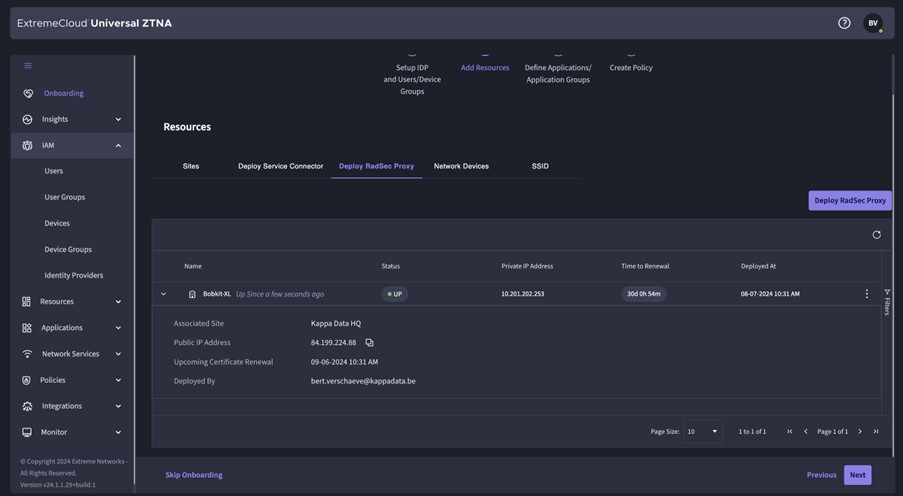
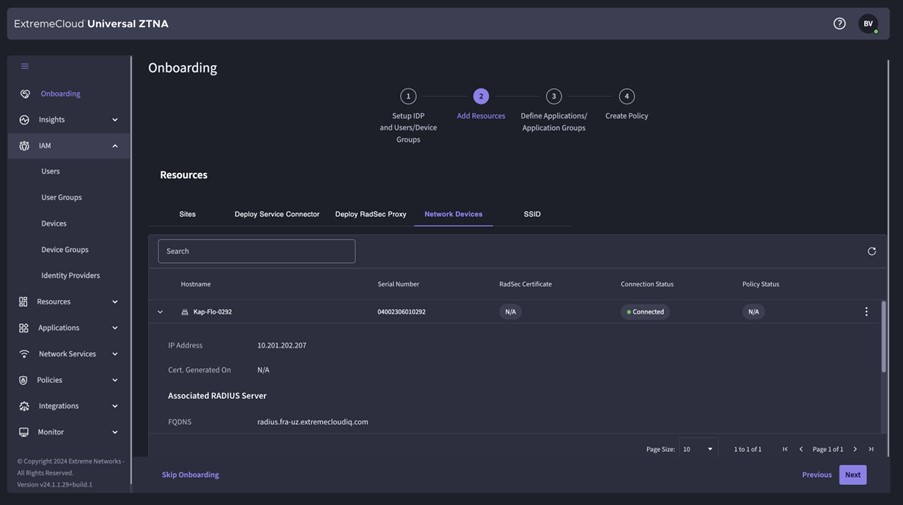
- Campus: Within the campus, the switches and APs run, which create a RADSEC tunnel to ExtremeCloud which then processes the authentication and sends a response back. There are switches and APs that send RADSEC directly to ExtremeCloud, older switches and later 3rd party switches first send Radius to a Radius Proxy that resides locally, which in turn sends RADSEC to ExtremeCloud.
UZTNA - Application Access
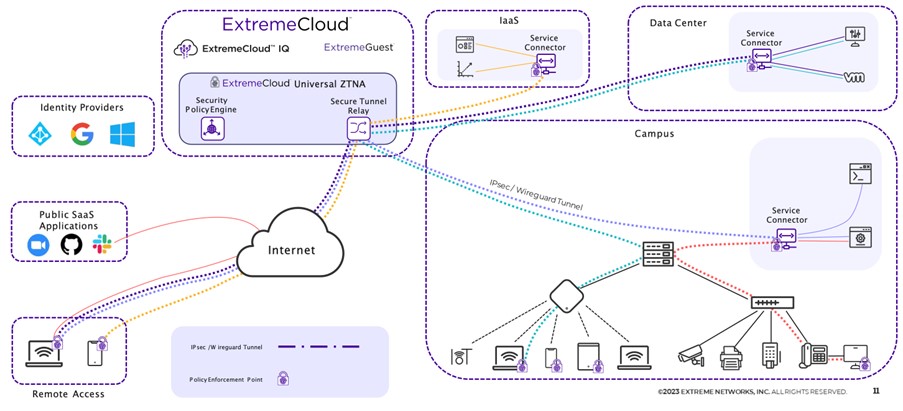
At ExtremeCloud, you have two applications :
- Extreme CloudIQ
- Universal ZTNA
Application Access is as well devided in two parts :
- Identity Provider: this is the same Identity Provider as discussed within Cloud NAC. The Identity Provider contains groups that you can use in policies to make certain applications available to a group of users.
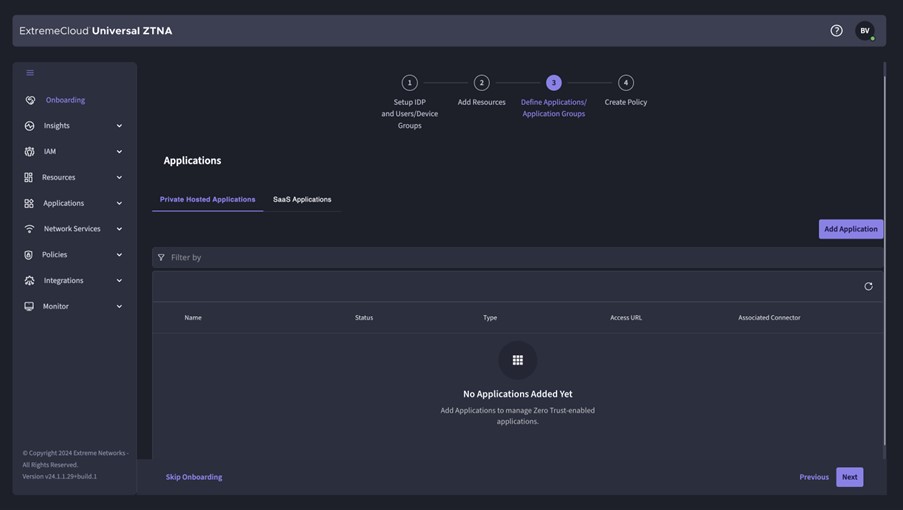
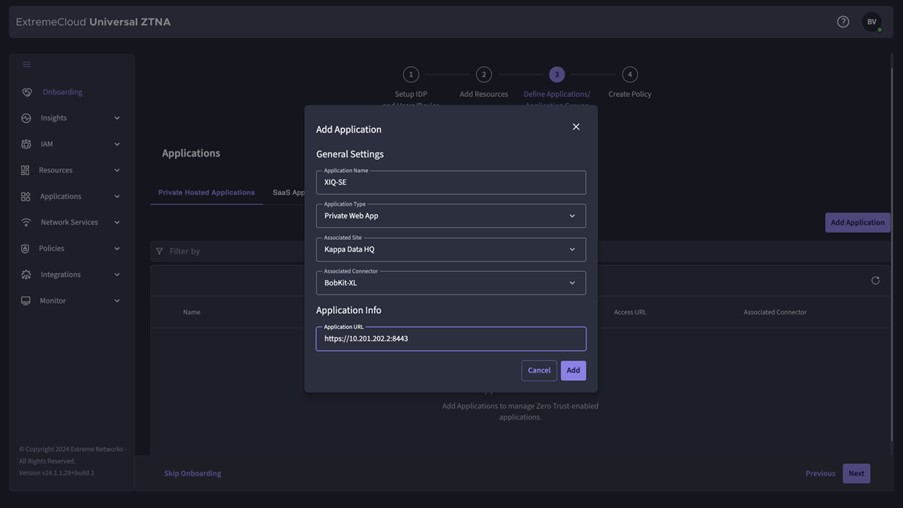
- Public SaaS Applications: These are applications where you can configure that they can only be used via a UZTNA connection. When a user connects via UZTNA, they can use the application, if they don’t have a connection to UZTNA they will be rejected. At the time of writing, these are: Mulesoft, Salesforce, Slack, G Suite, Splunk, Github, Atlassian, Dropbox and Zoom.
- Remote Access: this is a user who has the UZTNA Agent on their device with which they connect towards ExtremeCloud. This is agent-based or possibly also agentless.
- ExtremeCloud: this is the Universal ZTNA application where the policies are defined. The Secure Tunnel Relay ensures that the connections coming in through the agents are sent to the right applications.
- IaaS (Infrastructure as a Service): applications running in the Public Cloud (AWS, Azure, Google Cloud)
- Data Center: applications running in a Private Data Center (a service connector is installed on the hypervisor)
- Campus: Applications running on campus (a service connector is installed in the campus network)
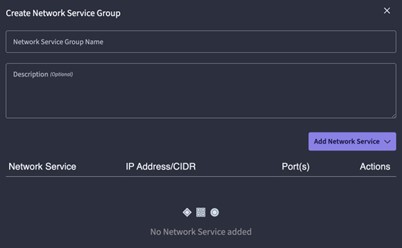
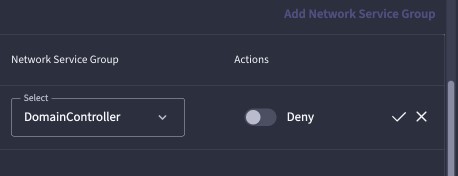
UZTNA Policies
Extreme Universal ZTNA flow
Step 1
Step 2
Step 3
Step 4
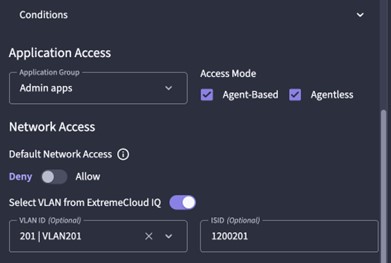
Conditions
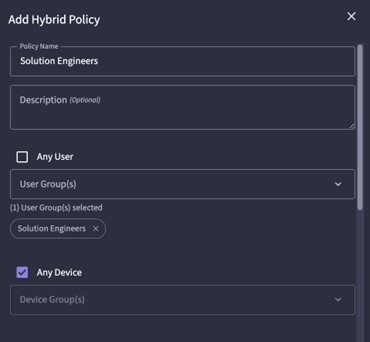
There is also a form of Conditional Access for Cloud NAC built into UZTNA. That way, access can be denied/allowed based on:
- Location
- Time
- Authentication (EAP-TLS, EAP-TTLS, MBA,…)
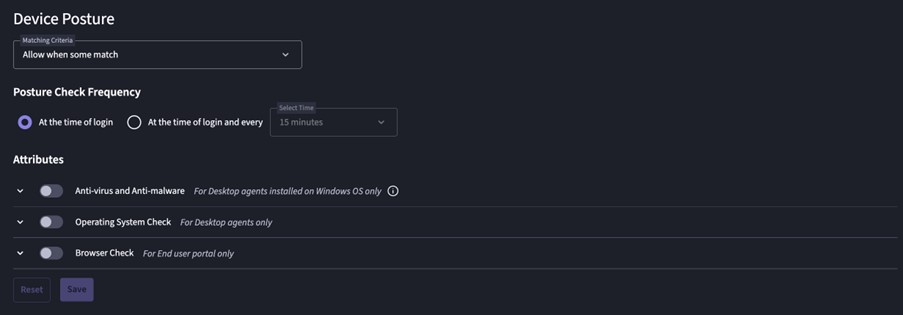
Device Posture
Access to applications can be denied if the agent notices that some things are out of order.
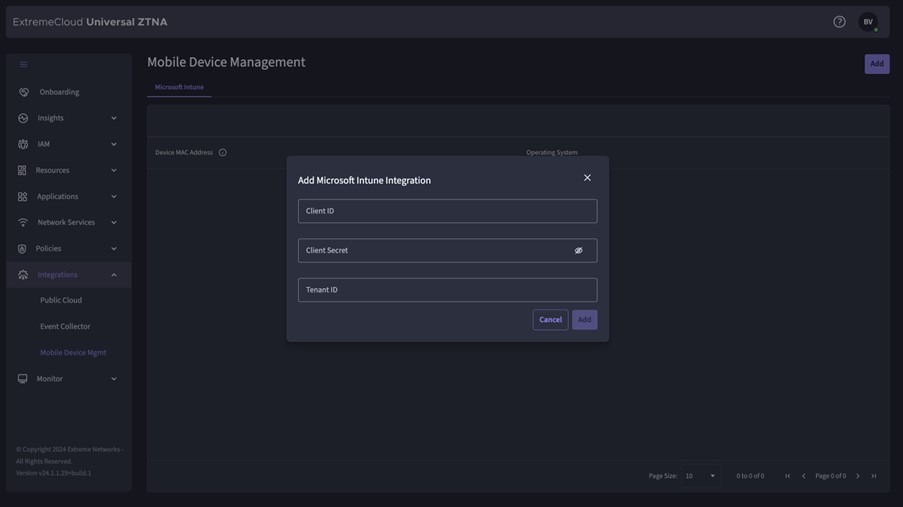
Mobile Device Managament (MDM)
There is also an integration with Microsoft Intune so you can only give compliant devices access via UZTNA.
Switch Configuration
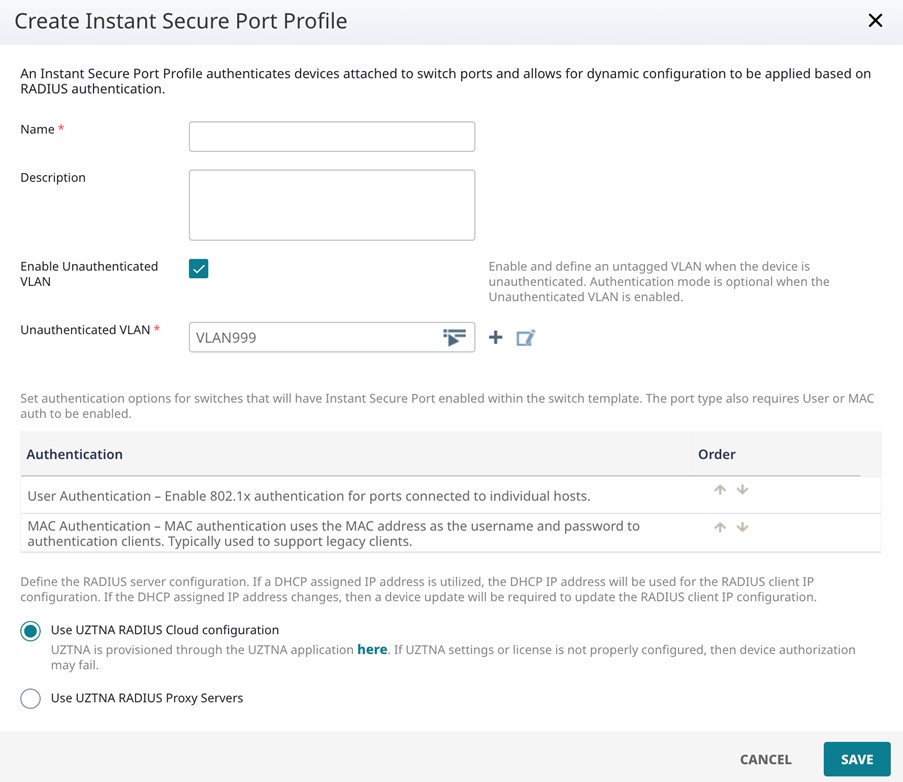
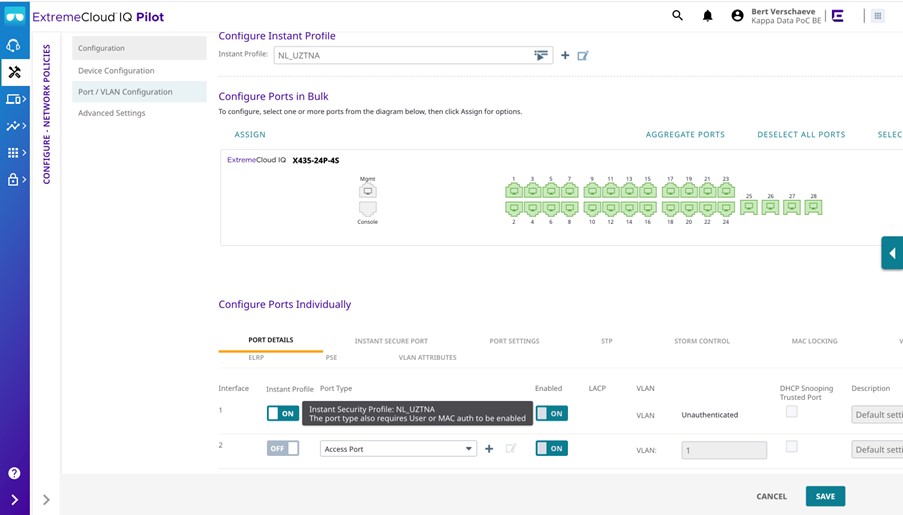
Within ExtremeCloud IQ, you can select the “Instant Secure Port” to make the switch port a “NAC” port. This way, Radius requests on that port are forwarded to UZTNA.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usWhy should organizations consider implementing Extreme UZTNA as part of their cybersecurity strategy?
Organizations should consider implementing Extreme UZTNA as part of their cybersecurity strategy because it provides a scalable, flexible, and robust security solution that adapts to modern threats and IT environments. By adopting ZTNA, organizations can:
- Enhance security across all environments: Whether on-premises, in the cloud, or in hybrid setups, ZTNA ensures consistent security.
- Increase resilience against advanced threats: Continuous verification and the least privilege principle reduce the risk of breaches and the impact of potential security incidents.
- Improve user experience: With context-aware access controls, ZTNA provides secure access without compromising usability, supporting productivity in remote and mobile workforces.
- Future-proof security: As organizations increasingly adopt cloud services and remote work, ZTNA provides a security framework that evolves with these trends, ensuring long-term protection.
Why is Extreme UZTNA important for enhancing cybersecurity?
Extreme UZTNA is important for enhancing cybersecurity because it:
- Reduces the attack surface: By limiting access to only the necessary resources and continuously verifying users and devices, ZTNA minimizes potential entry points for attackers.
- Prevents lateral movement: Even if an attacker gains initial access, ZTNA prevents them from moving laterally across the network by enforcing strict access controls for each resource.
- Adapts to modern IT environments: ZTNA is designed to secure access to both on-premises and cloud-based applications, making it ideal for hybrid and remote work environments.
- Improves incident response: With granular control and visibility over access requests, security teams can quickly identify and respond to suspicious activities.
What is Extreme Universal Zero Trust Network Access (ZTNA)?
Extreme Universal Zero Trust Network Access (UZTNA) is a cybersecurity solution that implements the Zero Trust security model, which assumes that no user or device should be trusted by default, whether inside or outside the network perimeter. This solution continuously verifies the identity of users and the security posture of devices before granting access to applications and data, ensuring that access is based on strict security policies.
How does Extreme UZTNA support compliance with cybersecurity regulations?
Extreme UZTNA supports compliance with cybersecurity regulations by providing detailed access controls, continuous monitoring, and robust reporting capabilities. This helps organizations meet requirements for data protection, access control, and auditability, which are often mandated by regulations such as GDPR, HIPAA, and the NIS 2 directive. By enforcing strict security policies and maintaining comprehensive logs of access activities, ZTNA helps organizations demonstrate compliance with these regulations.
How does Extreme UZTNA differ from traditional network security approaches?
Extreme UZTNA differs from traditional network security approaches by shifting from a perimeter-based security model to one that enforces security controls at the individual user and device level. Instead of granting broad access based on network location (e.g., inside the corporate firewall), ZTNA requires continuous verification of identity and device health, applying the principle of least privilege to grant access only to specific resources.
Contact us for a demo
Are you curious to learn how UZTNA can play an important security role at your customers? Contact us for a demo via the below button.