Firewall protection
We need a firewall for security and logically it is required by NIS2. You can also consider cloud hosted firewalls if most of your applications are cloud hosted or distributed. Check every vendor to learn more about them.

From history to the future, what is a firewall?
Firewall protection offered by Kappa Data
Firewalls at Barracuda Networks

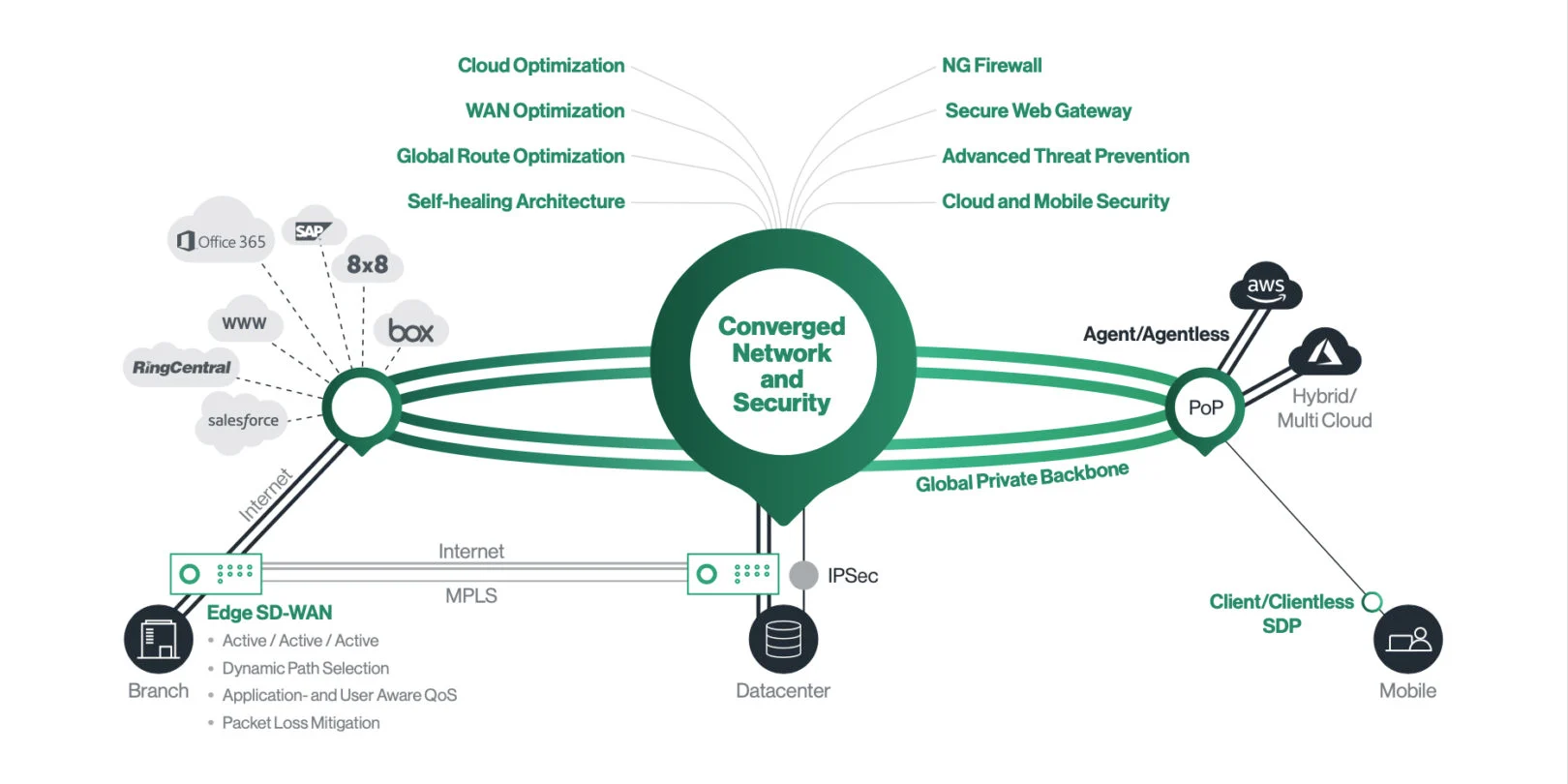
Cato Networks Firewall protection
Juniper Firewalls

Sophos Firewall protection

Stormshield Firewall

Why considering a Firewall?
A firewall is an essential part of keeping your computer systems and networks safe from unauthorized access and cyber threats. Here’s why having a firewall is important and what other options you might consider:
Firewalls are crucial because they control the flow of data in and out of your network, acting as a gatekeeper. They block unwanted traffic and allow only the safe and necessary data to pass through. This helps to prevent hackers and malicious software from accessing your systems. Firewalls also protect your sensitive data from being stolen or sent out of your network without your permission. Additionally, by managing network traffic efficiently, firewalls can help maintain good network performance.
Alternatives to Firewalls:
While firewalls are vital, there are other security measures that can also help protect your network. Here are some alternatives:
-
Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor your network for suspicious activity and can automatically block potential threats.
-
Antivirus and Antimalware Software: These programs scan your devices for malicious software and remove it to keep your system clean and safe.
-
Virtual Private Networks (VPNs): VPNs encrypt your internet connection, making it secure and private, especially useful for remote access.
-
Endpoint Security Solutions: These include various tools to protect individual devices, like antivirus software and encryption programs.
-
Network Access Control (NAC): This ensures that only authorized and compliant devices can connect to your network, adding an extra layer of security.
-
Zero Trust Security Models: This approach assumes that no user or device is trusted by default and continuously verifies every access request as if it comes from an open network.
-
Multi-Factor Authentication (MFA): MFA requires users to verify their identity in multiple ways before accessing your network, adding a strong layer of protection.
NIS2 requirements
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow are firewalls relevant to the NIS2 law?
Firewalls are relevant to the NIS2 law because they are a critical component of the security measures that organizations must implement to protect their network and information systems. Firewalls help ensure the integrity, confidentiality, and availability of the data and services that are essential for complying with NIS2 requirements.
How can organizations ensure their firewalls are compliant with NIS2 requirements?
Organizations can ensure their firewalls are compliant with NIS2 requirements by:
- Regularly updating firewall software: Ensuring that firewalls are running the latest security patches and updates.
- Configuring robust security policies: Implementing and maintaining strict access control and traffic filtering rules.
- Performing regular audits and assessments: Conducting security audits to identify and remediate vulnerabilities.
- Monitoring and logging: Continuously monitoring network traffic and maintaining logs for analysis and compliance reporting.
How do firewalls enhance cybersecurity in an organization?
Firewalls enhance cybersecurity by:
- Blocking unauthorized access: Preventing unauthorized users from accessing private networks.
- Filtering traffic: Allowing or blocking specific traffic based on security policies.
- Monitoring network activity: Logging and analyzing traffic patterns to detect suspicious activity.
- Protecting against attacks: Shielding the network from threats such as malware, phishing, and denial-of-service (DoS) attacks.
How do next-generation firewalls (NGFW) enhance compliance with NIS2?
Next-generation firewalls (NGFW) enhance compliance with NIS2 by offering advanced security features that go beyond traditional firewalls, such as:
- Deep packet inspection: Analyzing the contents of data packets to detect and block sophisticated threats.
- Intrusion prevention systems (IPS): Identifying and preventing potential security breaches in real-time.
- Application control: Managing and securing application traffic based on policies.
- Integrated threat intelligence: Using real-time threat intelligence to protect against emerging threats.
What is a firewall and what role does it play in network security?
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predefined security rules. Its primary role is to establish a barrier between a trusted internal network and untrusted external networks, such as the internet, to prevent unauthorized access and protect against cyber threats.
What specific requirements of the NIS2 law can firewalls help address?
Firewalls can help address several specific requirements of the NIS2 law, including:
- Risk management: By mitigating the risk of unauthorized access and cyber attacks.
- Incident response: By logging and monitoring network activity, which aids in the detection and response to security incidents.
- System security: By enforcing security policies and protecting critical systems from external threats.
- Continuity of services: By preventing disruptions caused by cyber attacks, thus ensuring the continuous operation of essential services.
Contact us for a demo
Are you curious to learn how Kappa Data can help you with Firewall solutions of different brand and for every type of organization? Contact us for a demo via the below button.
